Experience Center
Security Policy Audit Report
The Security Policy Audit Report allows you to view your Security Policy settings and improve them by following best practices guidelines.
You can view the report in the Admin Portal by going to Analytics > Internet & SaaS > Analytics > Security Policy Audit Report.
Report Sections
The report has three main sections:
- Traffic Inspection
- SSL Inspection: This includes the percentage of encrypted traffic that is being inspected, the Revoked Server certificate, and the Untrusted SSL Server certificate.
- Inbound/Outbound: Inspected inbound and outbound traffic.
- Protocol Inspection: This includes the following protocols:
- Inspect HTTP
- Inspect FTP over HTTP
- Inspect FTP
- Inspect Tunneled HTTP
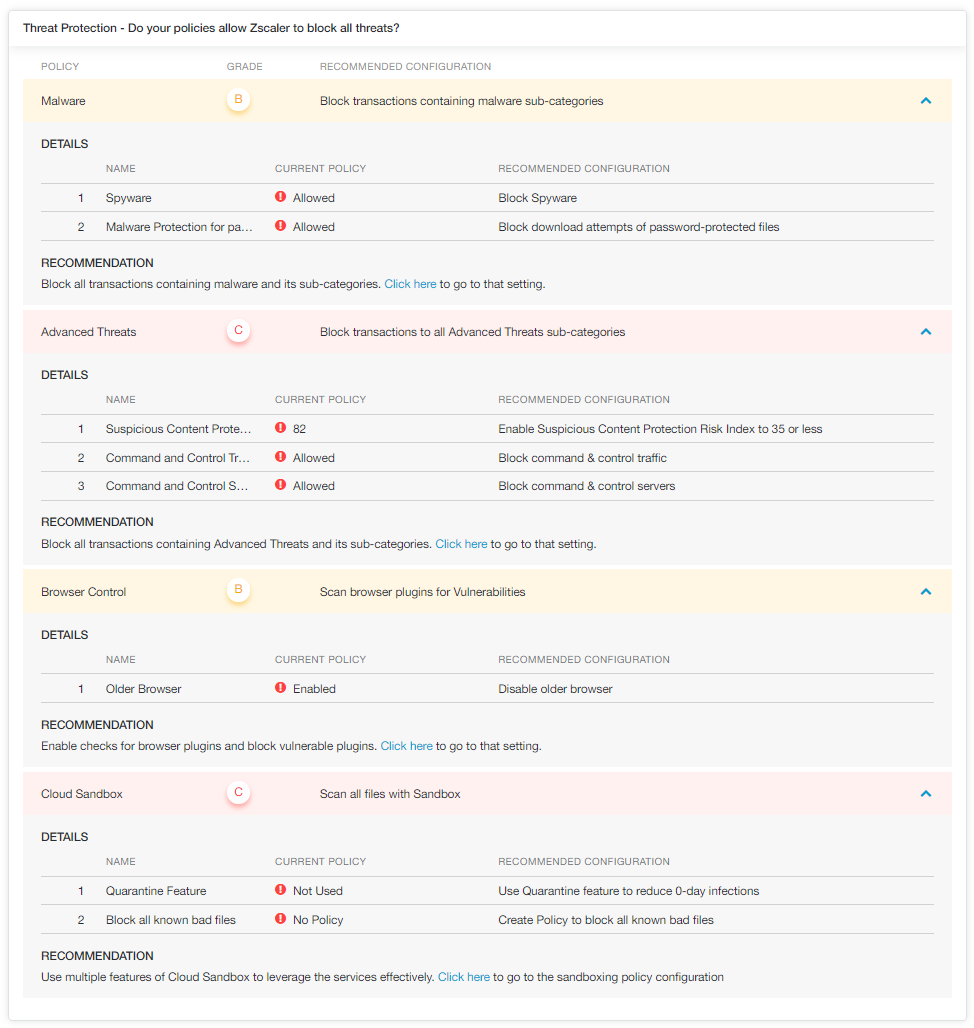
- Threat Protection
- Malware: Types of malware include:
- Viruses
- Unwanted applications
- Trojans
- Worms
- Adware
- Spyware
- Advanced Threats: Types of Advanced Threats include:
- PageRisk
- Botnet
- Malicious Active Content protection
- Fraud protection
- Unauthorized Communication protection
- XSS
- Suspicious destination
- Browser Control: This includes checks and Allow All Browsers. It's recommended to enable Checks & User Notifications and to block older browsers.
The Browser Vulnerability Protection section is only applicable when you are using browser-based authentication.
- Cloud Sandbox: This includes Sandbox policies 1 through 4.
- Malware: Types of malware include:
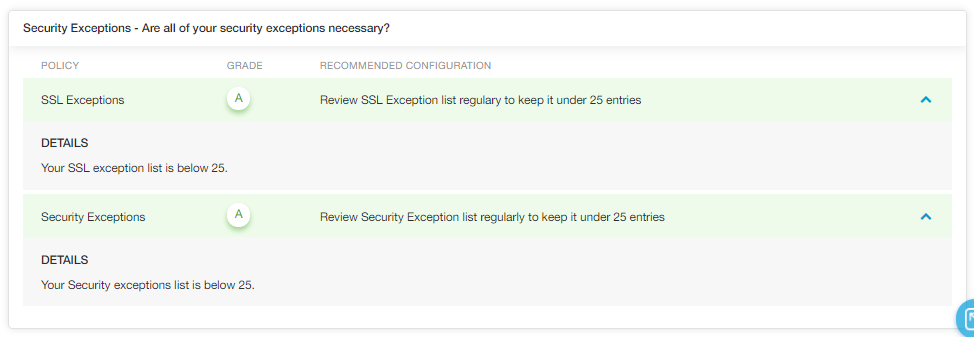
- Security Exceptions
Report Grading
The possible grades you can receive are A, B, C, or N/A, with C being the lowest. Your grade is impacted if you don't comply with the best practice guidelines. If you don't have a subscription for a certain area (e.g. Sandbox), then any non-compliance in that area won't impact your grade.
If you don't follow the best practice settings for the following areas and policies, your grade for non-compliance will be a C:
- See table.Close
Area Policy Best Practice Setting Malware Protection: Traffic Inspection Inspect Inbound Traffic Enabled Malware Protection: Traffic Inspection Inspect Outbound Traffic Enabled Malware Protection: Protocol Inspection Inspect HTTP Enabled Advanced Threats: Botnet Command & Control Servers Block Advanced Threats: Botnet Command & Control Traffic Block Advanced Threats: Malicious Active Content Malicious Content & Sites Block Advanced Threats: Fraud Protection Known Phishing Sites Block Advanced Threats: Fraud Protection Suspected Phishing Sites Block Sandbox Known malicious files from any URL category of any file type Action = Block
ALL FILE TYPES
ALL URL CATSSandbox All other file type and URL category combinations First Time Action = Allow and Scan
If you don't follow the best practice settings for all other areas, your grade for non-compliance will be a B.