Experience Center
About SSL Inspection Policy
SSL inspection policies are used to perform scanning of the SSL traffic based on the source and destination of the traffic. These policies help you to:
- Simplify the deployment and ongoing operations of SSL inspection.
- Address the compliance and operational environment requirements.
Pre-defined Special Rules
Zscaler provides the following pre-defined special rules which you cannot edit but just enable or disable based on your requirements.
- Zscaler Recommended Exemptions rule: Predefined rule to automatically exempt known destinations that cannot be SSL inspected. This rule is enabled by default.
- The Zscaler recommended exemptions URL category contains a few dozen destinations that cannot be SSL inspected for various reasons, such as certificate pinning. This list also includes Zscaler-owned domains.
- To discover the traffic that is not getting SSL inspected due to this rule, you can search the weblogs using the SSL Policy Reason field for the reason, Not inspected because of Zscaler best practices. The percentage of traffic that matches this rule is commonly very small and less than 1%.
- While it is recommended not to inspect these domains, you can disable the rule by clicking edit and changing the status to disable. Alternatively, you can leave the rule enabled, but create higher order Inspect rules if you'd like to inspect only specific domains out of the list.
- O365 tenant restriction inspection rules: Predefined rules to enable Office 365 Tenancy Restrictions for location and remote user traffic.
- O365 One Click rules: Predefined rule, controlled by the Microsoft-Recommended and Legacy Office 365 One Click setting.
- UCaaS One Click rules: Predefined rule, controlled by the UCaaS One Click configuration.
About the SSL Inspection Policy Page
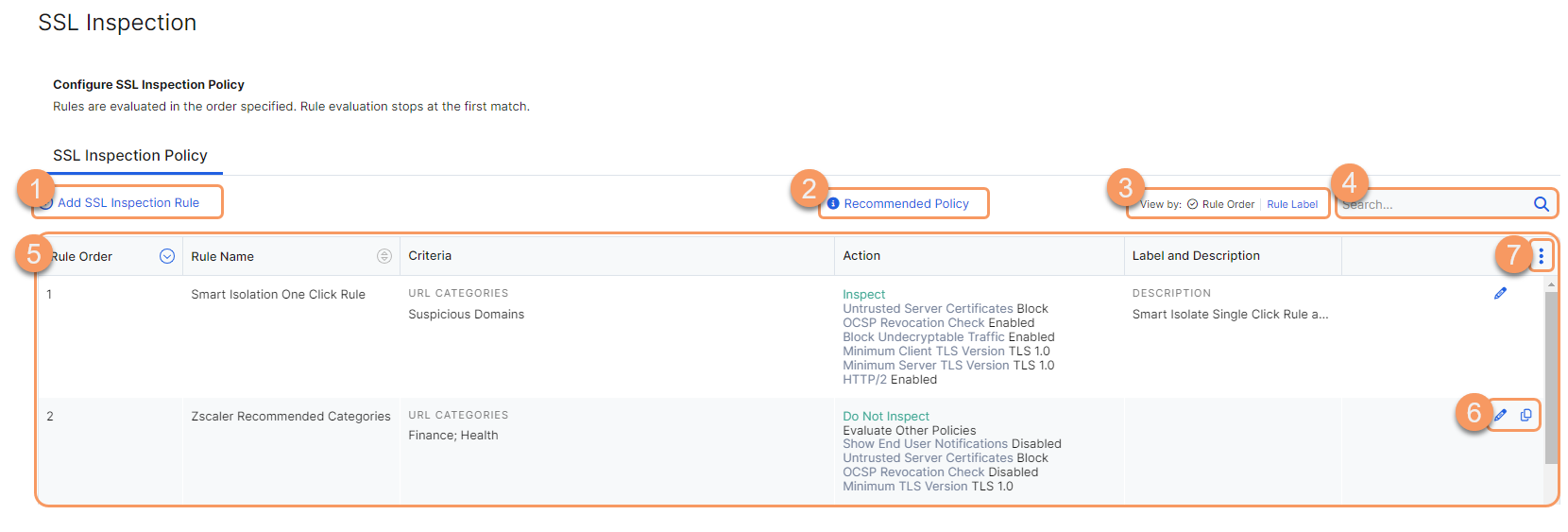
On the SSL Inspection Policy page (Policies > Common Configuration > SSL/TLS Inspection > SSL/TLS Inspection Policy), you can do the following:
- Add an SSL inspection rule.
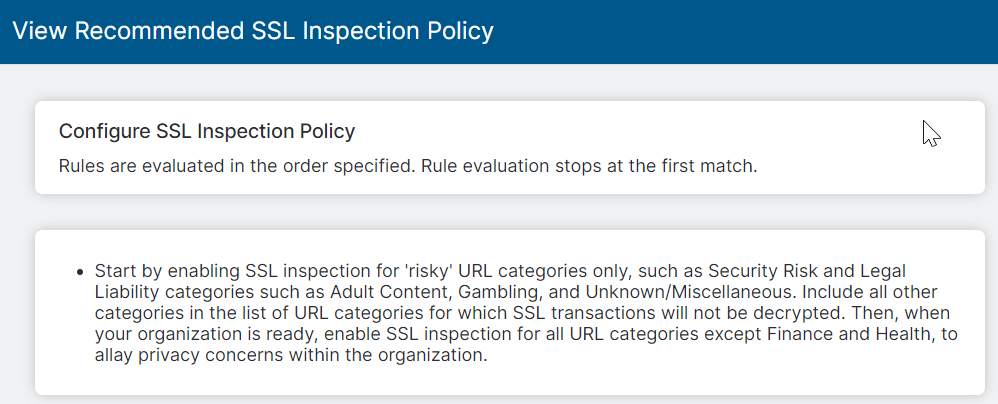
- View the recommended SSL inspection policy.
- Select one of the following View by option to see the SSL inspection rules accordingly:
- Rule Order: Displays the rules based on the rule order. By default, the rules are listed in the ascending rule order.
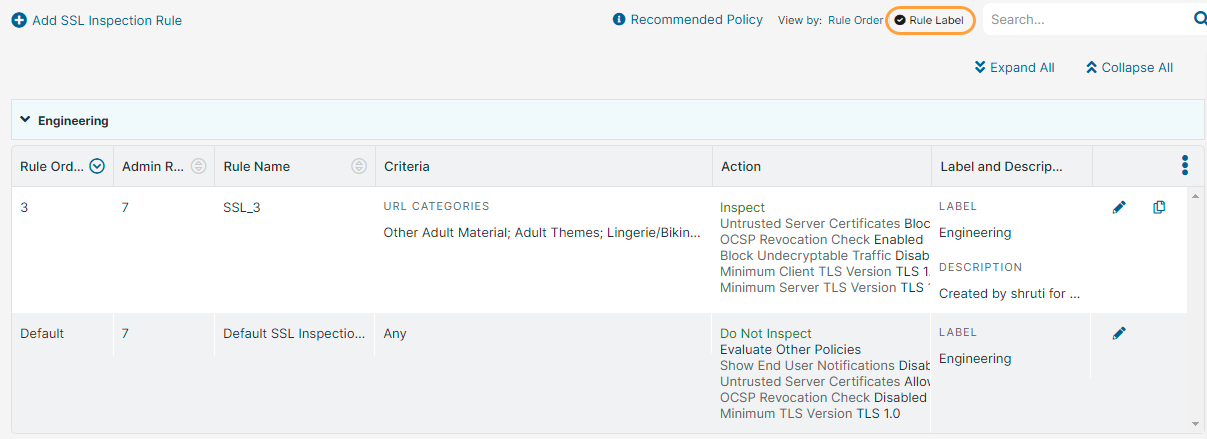
- Rule Label: Displays the rules based on the rule labels. The rules are grouped under the associated rule labels.
You can expand or collapse all the rule labels using the Expand All or Collapse All buttons.
- Search for an SSL inspection rule.
- View a list of all SSL inspection rules. For each SSL inspection rule, you can view the following information:
- Rule Order: The order of the rule.
- Rule Name: The name of the rule.
- Criteria: The criteria defined for the rule.
- Action: The action configured for the rule.
- Label and Description: The label and description of the policy rule, if available.
- Edit or duplicate an SSL inspection rule.
- Modify the table and its columns.