Experience Center
Choosing the CA Certificate for SSL Inspection
When SSL inspection is enabled, the Zscaler service establishes a separate SSL tunnel with the destination server and with the user’s browser. This allows the service to decrypt and inspect the HTTPS traffic coming to and from the user’s browser, as well as all traffic coming to and from the destination server.
To establish an SSL tunnel and return content to the user's browser, the service uses either the Zscaler intermediate certificate or a custom intermediate certificate signed by your own trusted Certificate Authority (CA). You can choose and configure the CA certificate based on your requirements. The Zscaler service does not install a Zscaler root certificate or a custom root certificate on the user's machine for SSL inspection. Customers who use Zscaler Client Connector for traffic forwarding can use the Zscaler Client Connector App Profile configuration for Windows and macOS to deploy these certificates on the user's machine. Customers who do not have Zscaler Client Connector installed on their Windows or macOS machines can push the certificate using Microsoft Active Directory (AD), Microsoft's Group Policy Object (GPO), or another Mobile Device Management (MDM) solution. The certificates need to be installed manually on Android and iOS devices or using MDM solutions.
To learn more about downloading and using certificates for SSL inspection, see:
- SSL Inspection Using Zscaler’s Default Intermediate CA Certificate
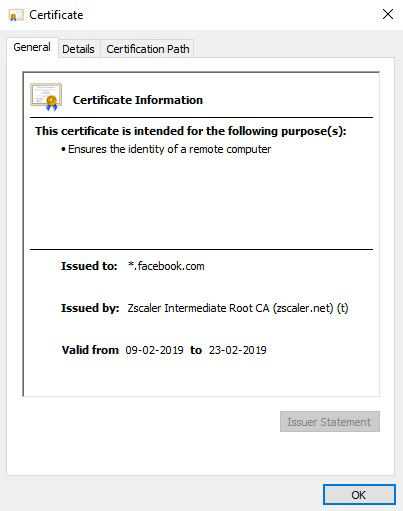
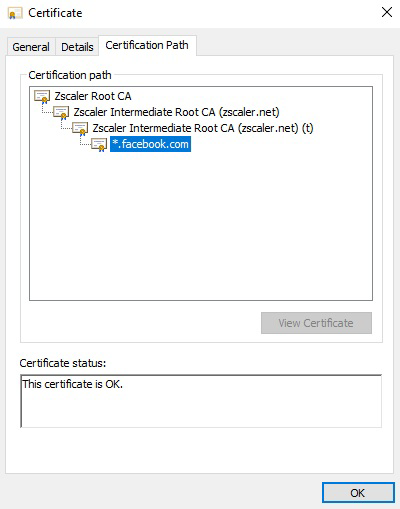
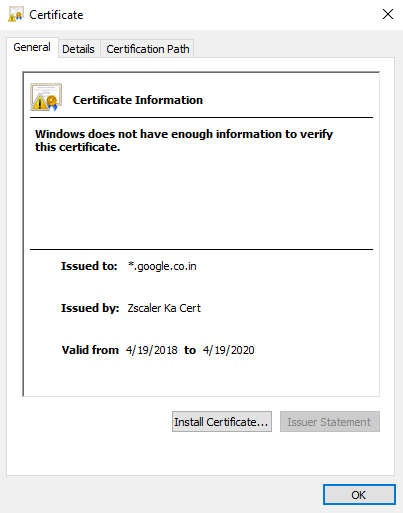
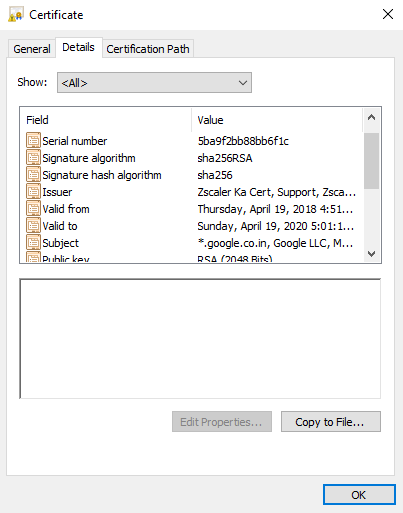
The Zscaler service dynamically generates and signs the server certificate that it presents to the client. This certificate contains the same fields as the original destination server certificate, except for the identifying information of the issuer, called the issuer distinguished name (DN). The issuer DN is set to the name of the Zscaler intermediate certificate. The browser receives this certificate signed by the Zscaler intermediate certificate along with the Zscaler intermediate certificate.
The second intermediate root certificate, Zscaler Intermediate Root CA (zscaler.net) (t), is used to sign the server certificate and is rotated every week.
CloseTo enable your browser or system to automatically trust all certificates signed by the Zscaler Certificate Authority, your users must install the Zscaler intermediate CA certificate on their workstations. Otherwise, they receive an error message stating that there is a problem with the website’s security certification.
In AD environments, you can use the AD's GPO feature to facilitate installing the certificate on multiple computers. Your organization does not need to install the Zscaler intermediate certificate because the Zscaler service sends it together with the certificate the service generated for the destination site.
To facilitate deployment in AD environments, use the GPO feature to deploy the certificate to all users in your network.
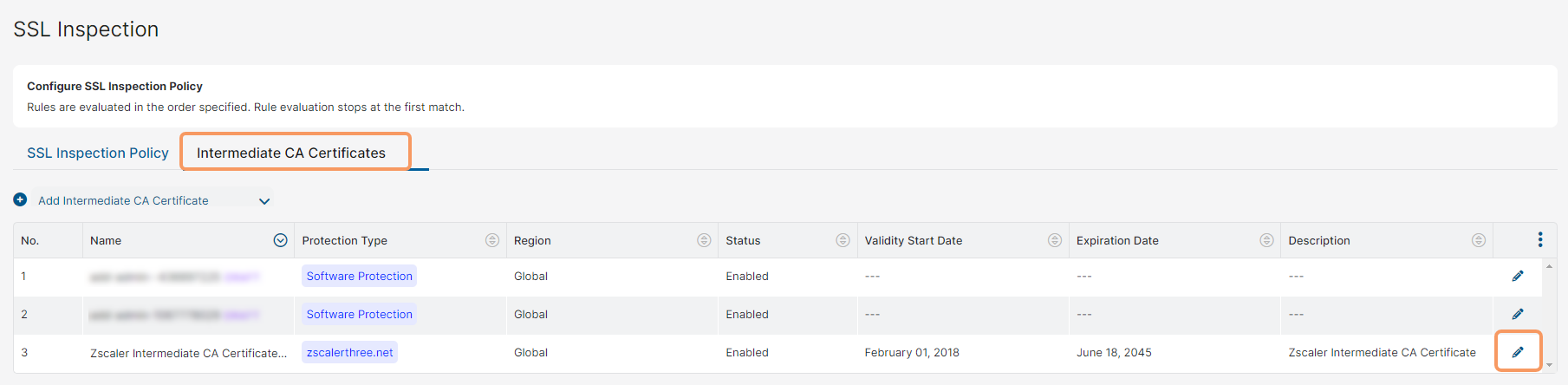
To download and use the Zscaler Intermediate CA Certificate:
- Go to Policies > Common Configuration > SSL/TLS Inspection > SSL/TLS Inspection Intermediate Certificate.
Click the Edit icon corresponding to the Zscaler Intermediate CA Certificate.
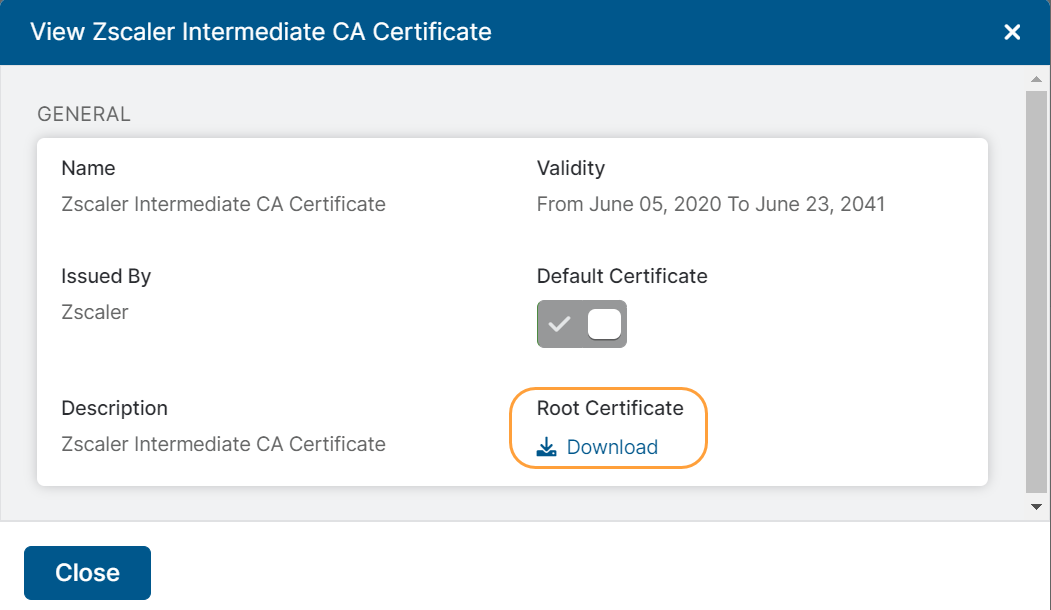
The View Zscaler Intermediate CA Certificate window appears.
In the View Zscaler Intermediate CA Certificate window, under the Root Certificate field, click Download. The root certificate is downloaded as a ZIP file.
- Navigate to the ZscalerRootCerts.zip file and unzip it.
- Import the Zscaler root certificate into the certificate store of your browser. To learn more, see Adding Custom Certificate to an Application Specific Trust Store.
You can enable the Default Certificate option to make the Zscaler Intermediate CA Certificate as the default certificate.
Close - SSL Inspection Using a Custom Intermediate CA Certificate
Zscaler offers subscriptions to software and cloud HSM protection types to configure your intermediate CA certificates for SSL inspection. You can subscribe to one or both of the protection types based on your requirements.
If you have subscribed to only the software protection type, Zscaler allows you to create up to two intermediate CA certificates, but only one can be enabled at a time and used for SSL interception. If you have subscribed to both software and cloud HSM protection types, Zscaler allows you to create up to 8 intermediate CA certificates, but only 4 can be enabled at a time and used for SSL interception.
You can only have one default intermediate CA certificate. It can either be the Zscaler’s default intermediate certificate or an enabled custom intermediate CA certificate.
Click on the following protection types to learn more about configuring intermediate certificates.
The Zscaler service doesn't use your organization’s root certificate or private keys. Instead, it uses the custom intermediate certificate signed by your own CA, so you can use a trusted CA that is already deployed on your organization's machines. You can control the validity period of the intermediate certificate or revoke it in the Admin Portal at any time.
To configure an intermediate certificate, you can generate a Certificate Signing Request (CSR) in the Admin Portal. The service generates the CSR with a key pair (i.e., public and private key) and encrypts the private key using AES. The private key is stored securely in the Zscaler Central Authority (CA) for the software intermediate certificate and Zscaler intermediate certificate and the cloud HSM solution for the cloud HSM intermediate certificate, while the CSR contains the public key. To learn more about how Zscaler safeguards SSL keys and data collected during SSL inspection, see Safeguarding SSL Keys and Data Collected During SSL Inspection.
After your CA signs the CSR, you can upload the signed certificate to the service. During the SSL negotiation with the user’s browser, the Zscaler service dynamically generates and signs the server certificate that it presents to the client with this intermediate certificate. The certificate issuer is set to the organization name, and theZscaler service generates the certificate once per site and caches these certificates on the Internet & SaaS Public Service Edge. These cached certificates are usually valid until their expiration date. The following is an example of a certificate signed by an organization's custom intermediate certificate.
Close - CDP for All Certificates
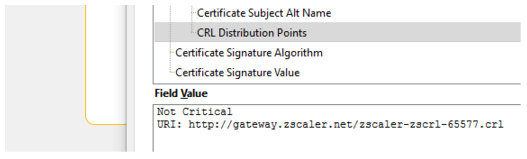
The Zscaler service provides a Certificate Revocation List (CRL) distribution point (CDP) for every certificate it generates, so that client applications can locate the Certificate Revocation Lists (CRLs) as necessary. The certificate displays the CDP, as shown in the following image. The CRLs are hosted by the Zscaler service and provide the serial numbers of revoked certificate issuers.
Close