Secure Internet and SaaS Access (ZIA)
IPSec VPN Configuration Guide for Juniper SSG 20
This article uses only sample IP addresses in the configuration steps and screenshots. For tunnel interface configuration, you must use only RFC 1918 IP addresses and not APIPA addresses.
This article shows how to configure two IPSec VPN tunnels from a Juniper SSG 20 firewall running ScreenOS 6.2.0r1.0 to two ZIA Public Service Edges in the Zscaler cloud. To learn more about WebUI, refer to the Juniper documentation.
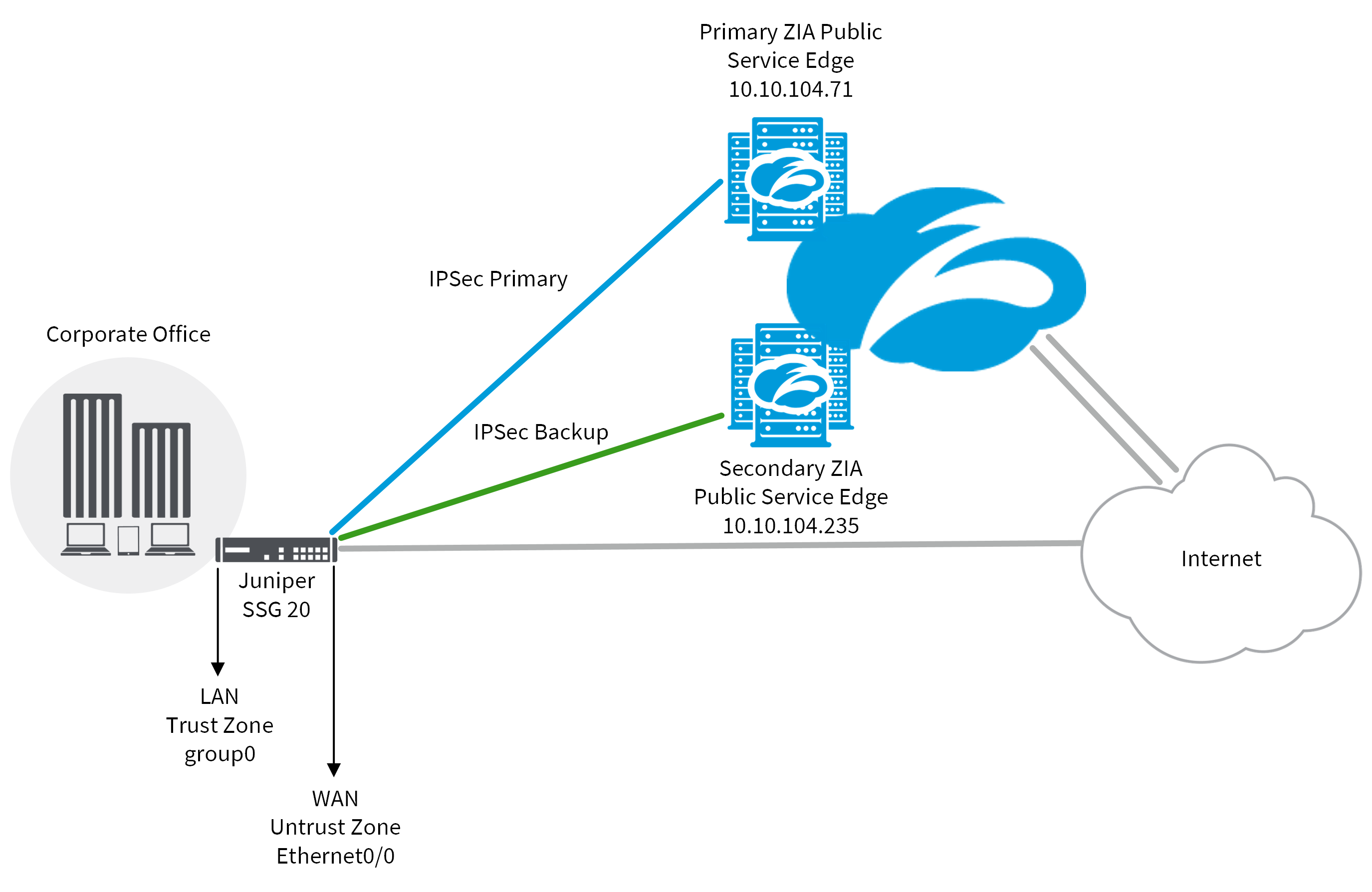
As shown in the following figure, the internal traffic of the corporate office is in the Trust zone. The WAN port Ethernet 0/0 is in the Untrust zone. It sends internet-bound traffic through the VPN tunnel to the Zscaler cloud and performs NAT on the traffic it sends to the internet.
Zscaler IPSec tunnels support a limit of 400 Mbps for each public source IP address. If your organization wants to forward more than 400 Mbps of traffic, Zscaler recommends using one of the following configurations:
- Configure multiple IPSec tunnels with different public source IP addresses.
- Configure multiple IPSec VPN tunnels with the same public source IP address using NAT-T and source port randomization with IKEv2 for all the configured tunnels.
For example, if your organization forwards 800 Mbps of traffic, you can configure two primary VPN tunnels and two backup VPN tunnels.
Dead Peer Detection (DPD) must be enabled so the firewall can detect if a VPN is offline. If this occurs, it routes the internet-bound traffic through the backup VPN. In this configuration example, a route-based VPN is configured, where two tunnels are created and then inserted as the default routes in the routing table.
Prerequisites
Ensure you have the following information for setting up the IPSec VPN tunnels:
Configuring the IPSec VPN Tunnel in the ZIA Admin Portal
In this example configuration, the peers are using an FQDN and a pre-shared key (PSK) for authentication.
To configure the IPSec VPN tunnels in the ZIA Admin Portal:
You need the FQDN and PSK when linking the VPN credentials to a location and creating the IKE gateways.
- Linking the VPN Credentials to a Location
Configuring the IPSec VPN Tunnel in the Juniper SSG 20 WebUI
This article only covers the configuration details of IPSec VPN tunnels between the Juniper SSG 20 firewall and the ZIA Public Service Edges. For any other specific information about Juniper SSG 20, refer to the Juniper documentation.
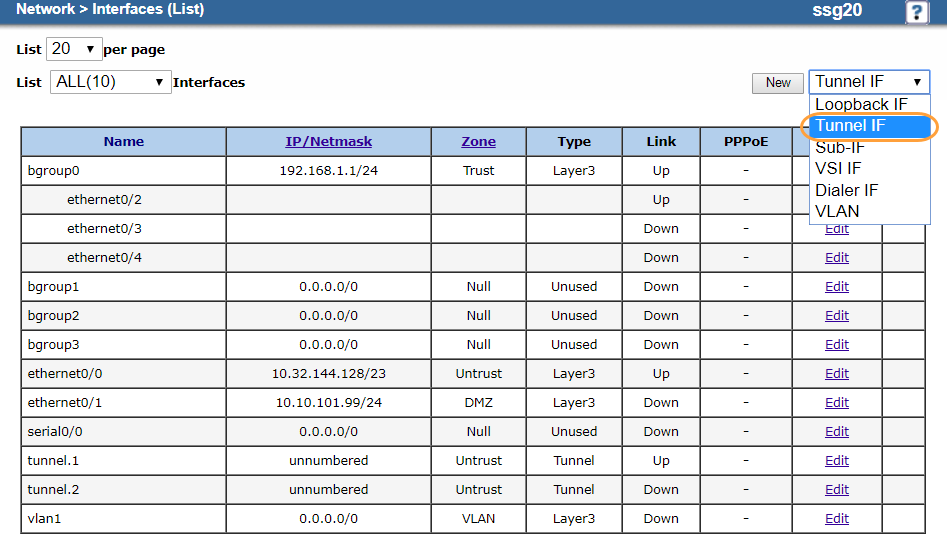
The following image shows the interface setup in the Juniper WebUI (Network > Interfaces > List):

Ensure that the internet port (ethernet 0/0) is in the Untrust zone and the bgroup0 LAN and wireless ports are in the Trust zone.
To configure the IPSec VPN tunnels on Juniper SSG 20:
Zscaler does not support Extended Sequence Number (ESN) based proposals during IPSec tunnel negotiation.
- 1. Configure the Tunnel Interfaces
Configure two IPSec tunnel interfaces using the internet port (ethernet 0/0). Ensure both tunnel interfaces are in the Untrust zone.
To configure the primary tunnel interface:
Log in to the Juniper SSG 20 WebUI.
Go to Network > Interfaces > List.
In the upper-right corner, choose Tunnel IF.
Click New.
On the Configuration page:
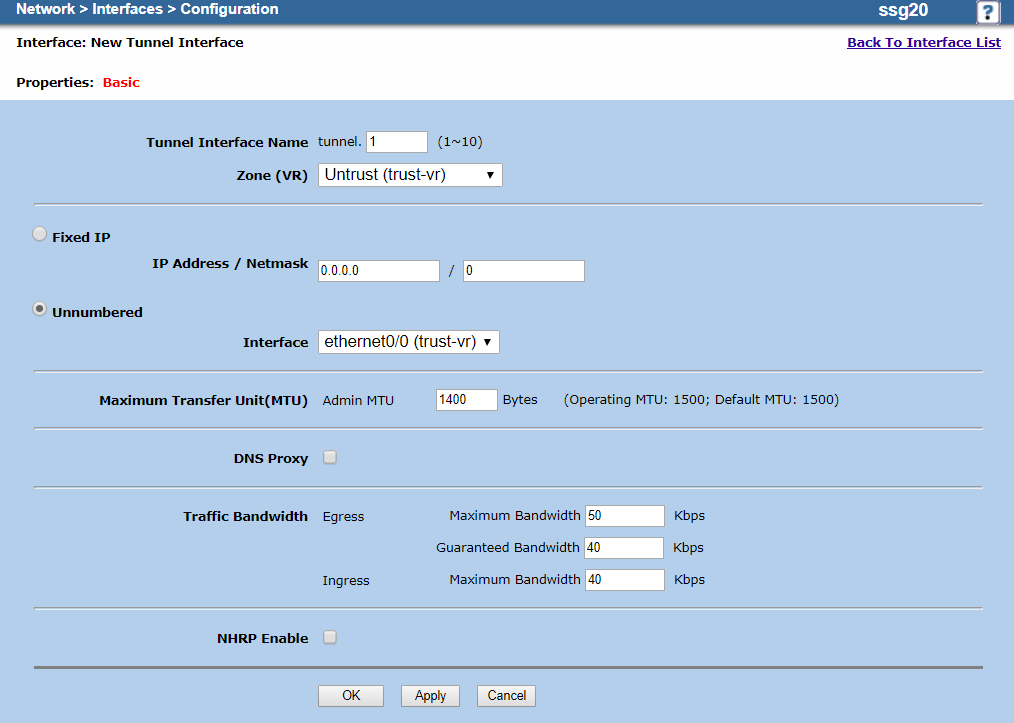
- Tunnel Interface Name: Enter a number for the tunnel interface name. The name is prepended with tunnel. In this example, it's
tunnel.1. - Zone (VR): Choose Untrust (trust-vr).
- Select Unnumbered.
- Interface: Choose ethernet0/0 (trust-vr).
- Maximum Transfer Unit(MTU): Enter the optimal MTU for your tunnel. In this example, it's
1400Bytes. - Deselect DNS Proxy.
- Traffic Bandwidth:
- Egress Maximum Bandwidth: Enter the maximum bandwidth (Kbps) for outbound traffic. In this example, it's
50kbps. - Egress Guaranteed Bandwidth: Enter the guaranteed bandwidth (Kbps) for outbound traffic. In this example, it's
40kbps. - Ingress Maximum Bandwidth: Enter the maximum bandwidth (Kbps) for inbound traffic. In this example, it's
40kbps.
- Egress Maximum Bandwidth: Enter the maximum bandwidth (Kbps) for outbound traffic. In this example, it's
- Deselect NHRP Enable.
- Tunnel Interface Name: Enter a number for the tunnel interface name. The name is prepended with tunnel. In this example, it's
- Click OK.
After configuring the primary tunnel, repeat this procedure to configure the backup tunnel interface (tunnel.2).
Close - 2. Create a Phase 1 Proposal
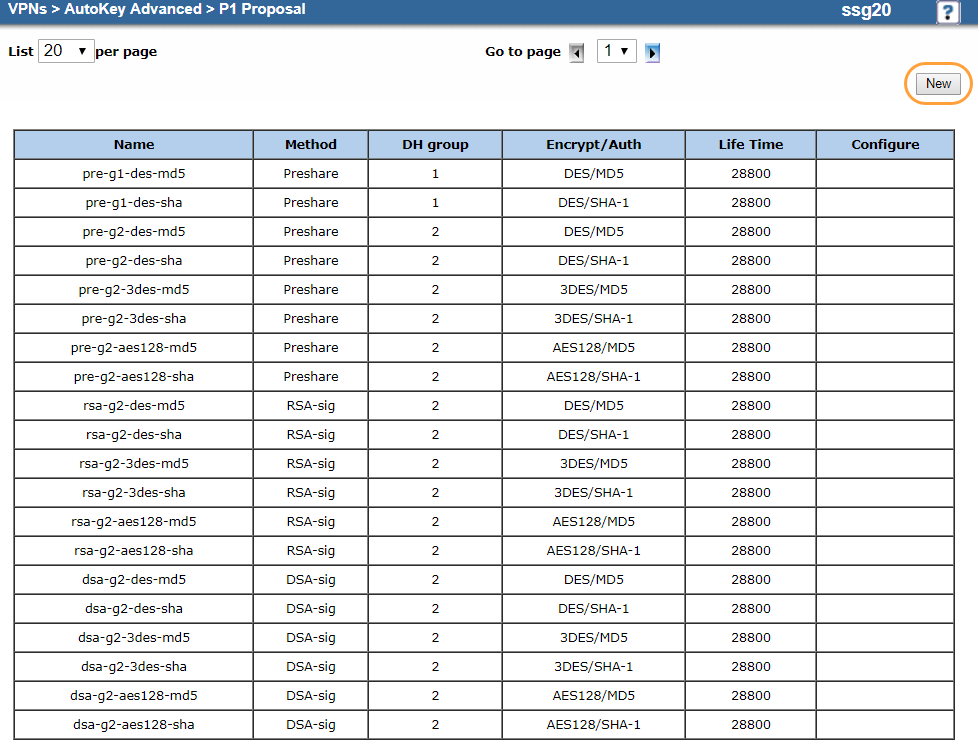
Create a Phase 1 proposal with the following IKE parameters.
To create a Phase 1 proposal:
Go to VPNs > AutoKey Advanced > P1 Proposal.
Click New.
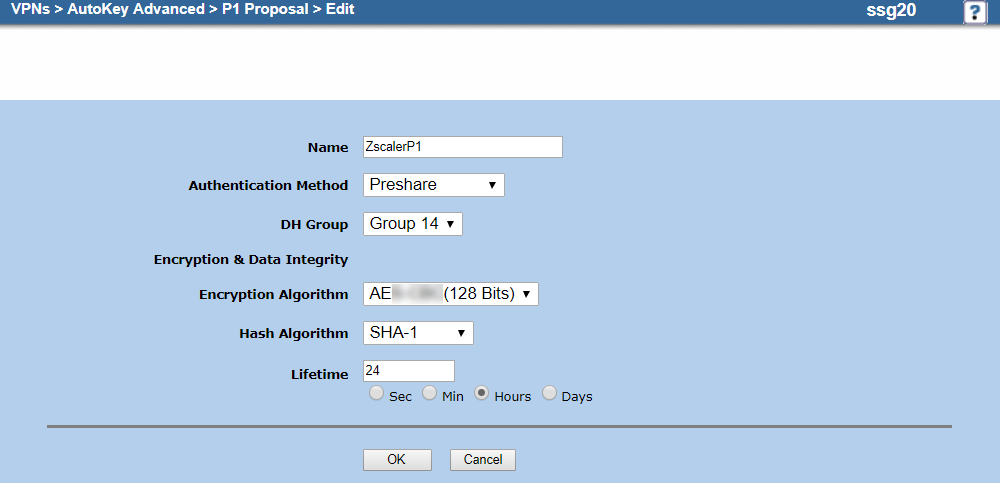
On the P1 proposal Edit page:
- Name: Enter a name for the P1 proposal. In this example, it's
ZscalerP1. - Authentication Method: Choose Preshare.
- DH Group: Choose Group 14.
- Encryption Algorithm: Choose AES-GCM(128 Bits).
- Hash Algorithm: Choose SHA-1.
- Lifetime: Enter a lifetime. In this example, it's
24hours.
- Click OK.
- 3. Create a Phase 2 Proposal
Create a Phase 2 proposal with the following IKE parameters.
To create a Phase 2 proposal:
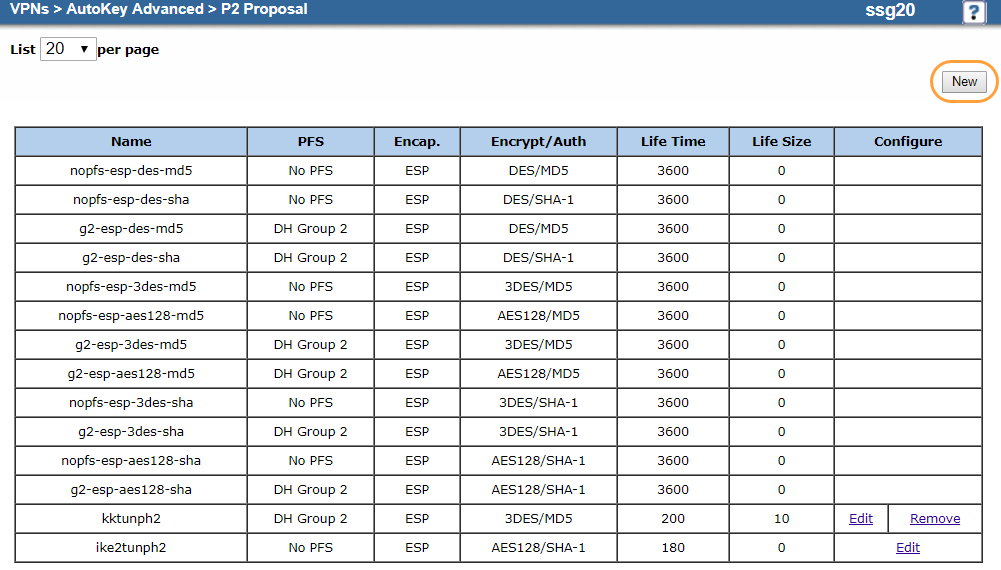
Go to VPNs > AutoKey Advanced > P2 Proposal.
Click New.
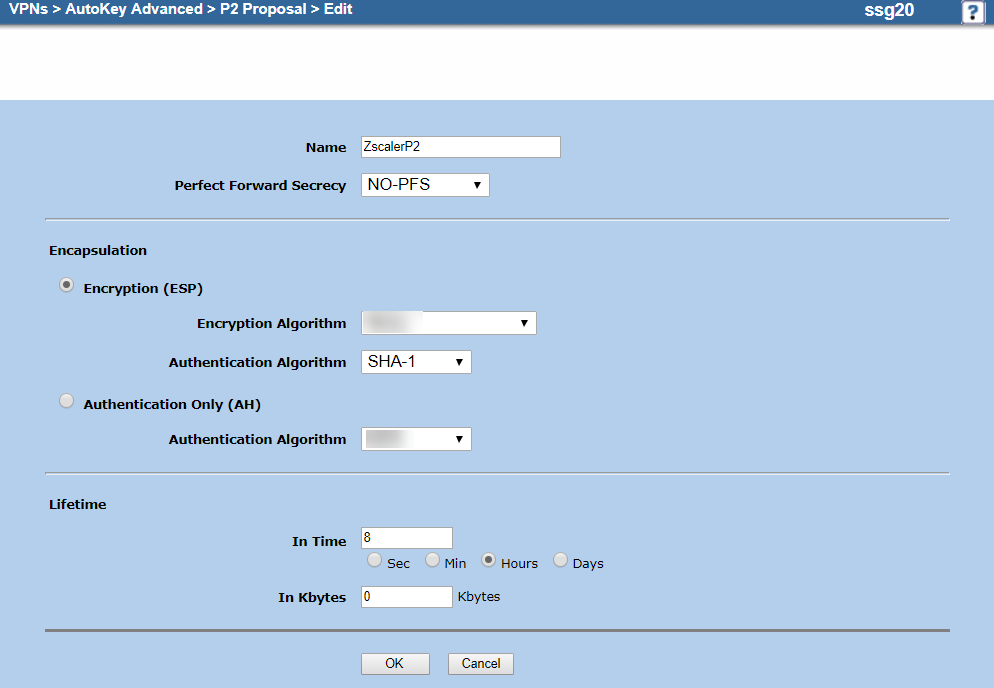
On the P2 proposal Edit page:
- Name: Enter a name for the P2 proposal. In this example, it's
ZscalerP2. - Perfect Forward Secrecy: Choose NO-PFS.
Encapsulation: Select Encryption (ESP).
- Encryption Algorithm: Choose AES-GCM based encryption.
For Phase 2, Zscaler recommends using AES-GCM-based ciphers if you have purchased a separate encryption SKU. If you do not have a separate subscription, Zscaler recommends using NULL encryption.
- Authentication Algorithm: Choose SHA-1.
- Lifetime:
- In Time: Enter a lifetime. In this example, it's
8hours. - In Kbytes: Enter
0bytes.
- In Time: Enter a lifetime. In this example, it's
- Click OK.
- 4. Configure the IKE Gateways
Configure two IKE gateways, one for each ZIA Public Service Edge. In this example, the primary gateway created is named Primary-Gateway with the ZIA Public Service Edge VIP addresses 165.225.80.34. The backup gateway is named Backup-Gateway with the ZIA Public Service Edge VIP address 185.46.212.34.
To configure the primary IKE gateway:
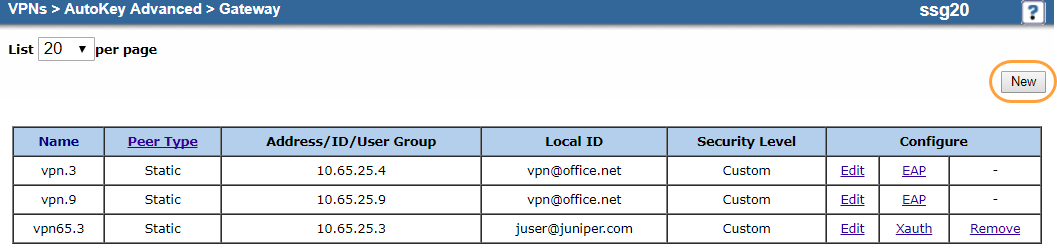
Go to VPNs > AutoKey Advanced > Gateway.
Click New.
On the gateway Edit page:
- Gateway Name: Enter a name for the IKE gateway. In this example, it's
Primary-Gateway. - Version: Select IKEv2.
- Select Remote Gateway and then select Static IP Address under it.
- IP Address/Hostname: Enter the ZIA Public Service Edge VIP address for the primary gateway. In this example, it's
165.225.80.34. - Peer ID: Leave blank.
- User: Choose None.
- Group: Choose None.
- IP Address/Hostname: Enter the ZIA Public Service Edge VIP address for the primary gateway. In this example, it's
Click Advanced.
On the advanced gateway Edit page:
- Select IKEv2 Auth Method.
- Self: Choose preshare.
- Peer: Choose preshare.
- Preshared Key: Enter the pre-shared key for the VPN credentials you added in the ZIA Admin Portal.
- Use As Seed: Leave unselected.
- Local ID: Enter the FQDN for the VPN credentials you added in the ZIA Admin Portal. In this example, it's the FQDN
example@safemarch.com. - Outgoing Interface: Choose ethernet0/0.
- Security Level:
- User Defined: Choose Custom.
- Phase 1 Proposal: Choose the P1 proposal you created in 2. Create a Phase 1 Proposal. In this example, it's ZscalerP1.
- Mode (Initiator): You can't modify this field.
- Enable NAT-Traversal: Select.
- UDP Checksum: Leave unselected.
- Keepalive Frequency: Enter
5seconds.
- Select DPD under Peer Status Detection.
- Interval: Enter
5seconds. - Retry: Enter
5seconds. - Select Always Send.
- Interval: Enter
- Preferred Certificate(optional):
- Local Cert: Choose None.
- Peer CA: Choose None.
- Peer Type: Choose the peer type. In this example, it's X509-SIG.
- Use Distinguished Name for Peer ID: Leave unselected.
- Click Return.
Click OK.
- Repeat the procedure to create the backup IKE gateway (Backup-Gateway) using the ZIA Public Service Edge VIP address 185.46.212.34.
- 5. Configure the AutoKey IKE VPN Tunnels
Configure two AutoKey IKE VPN tunnels to two different ZIA Public Service Edges. In this example, the primary VPN tunnel is configured from the primary IKE gateway (Primary-Gateway). It uses the global ZIA Public Service Edge IP address 185.46.212.88 for VPN monitoring. The backup VPN tunnel is configured from the backup IKE gateway (Backup-Gateway). It uses the global ZIA Public Service Edge IP address 185.46.212.89 for VPN monitoring.
To configure the primary VPN tunnel:
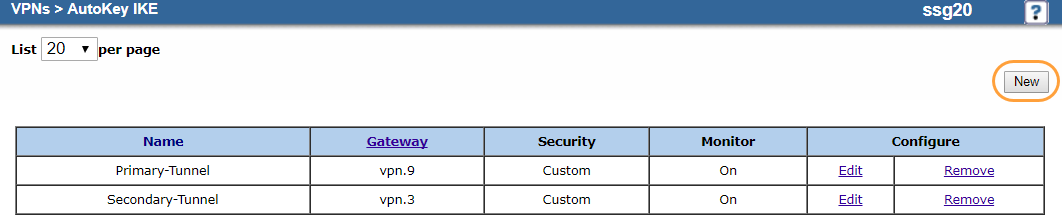
- Go to VPNs > AutoKey IKE.
- Click New.
- On the AutoKey IKE Edit page:
- VPN Name: Enter a name for the VPN tunnel. In this example, it's
Primary-Tunnel. - Select Remote Gateway.
- Select Predefined and then choose the primary IKE gateway you configured in 4. Configure the IKE Gateways. In this example, it's Primary-Gateway.
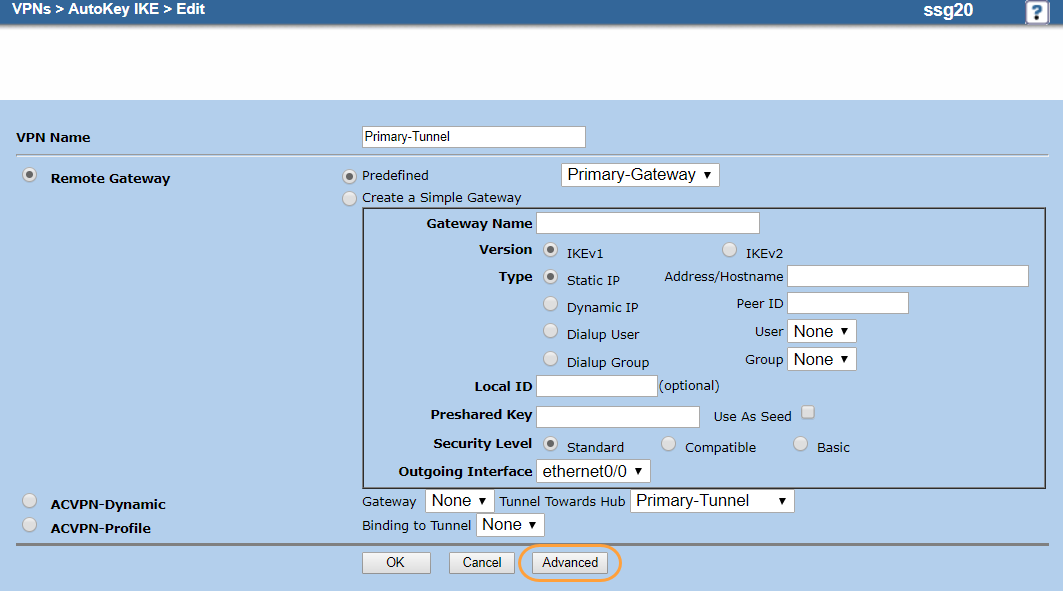
- Click Advanced.
- On the advanced AutoKey IKE Edit page:
- Security Level:
- User Defined: Choose Custom.
- Phase 2 Proposal: Choose the P2 proposal you created in 3. Create a Phase 2 Proposal. In this example, it's ZscalerP2.
- Select Replay Protection.
- Transport mode: Leave unselected.
- Bind to: Choose Tunnel Interface, and choose the primary tunnel interface you configured in 1. Configure the Tunnel Interfaces. In this example, it's tunnel.1.
- Proxy-ID: Leave unselected.
- DSCP Marking: Select Disable.
- VPN Group: Choose None.
- Select VPN Monitor.
- Source Interface: Choose ethernet0/0.
- Destination IP: Enter the global ZIA Public Service Edge IP address for your primary tunnel. In this example, it's
185.46.212.88. - Select Optimized.
- Select Rekey.
- Click Return.
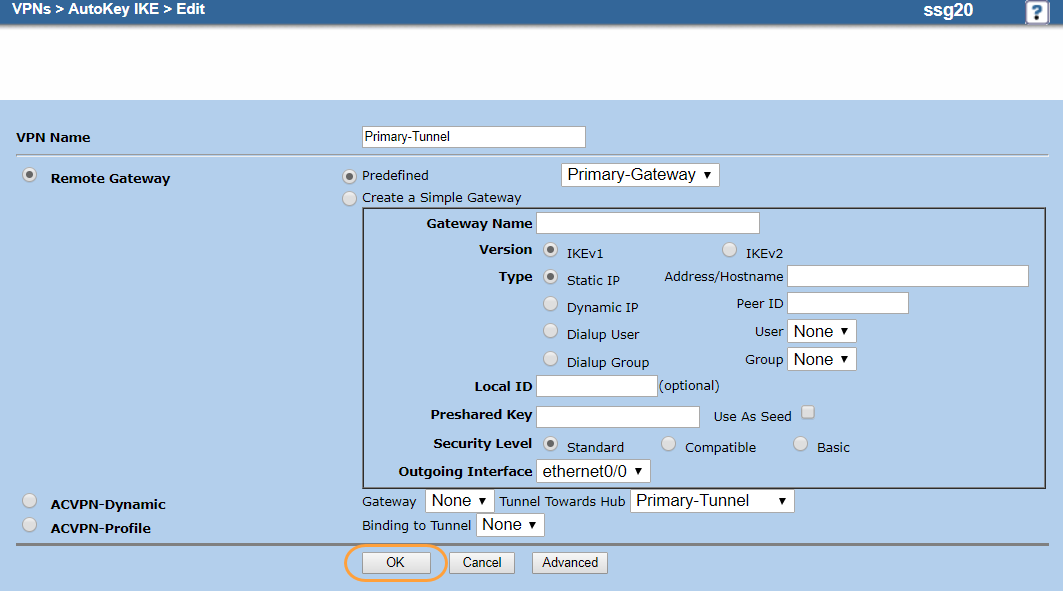
- Click OK.
- Repeat the procedure to create a backup VPN tunnel (Backup-Tunnel) using the backup tunnel interface (tunnel.2), IKE gateway (Backup-Gateway), and global ZIA Public Service Edge IP address (185.46.212.89).
- 6. Configure Policy-Based Routing
Configure policy-based routing (PBR) so your organization can send its outbound traffic from the Trust to the Untrust security zone and through the tunnel interfaces.
To configure PBR:
- a. Configure an Extended Access Control List
Configure an extended Access Control List (ACL). The extended ACL defines the destination IP address, ports, and protocols.
To configure the extended ACL:
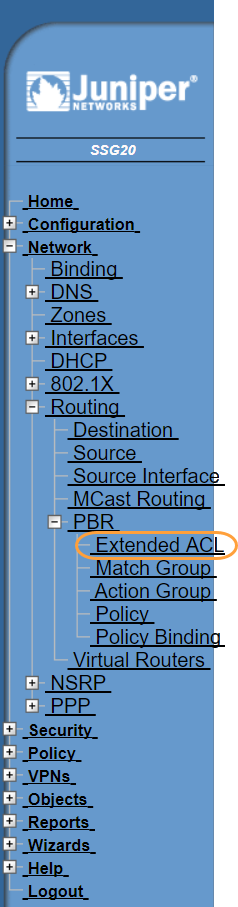
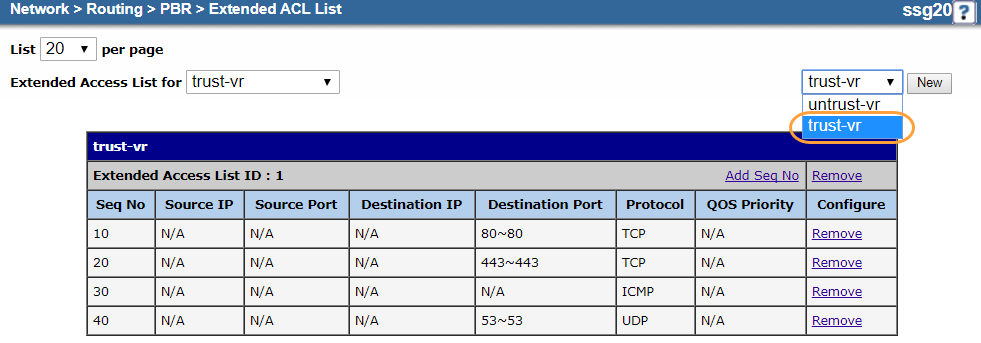
- Go to Network > Routing > PBR > Extended ACL.
- In the upper-right corner, choose trust-vr.
- Click New.
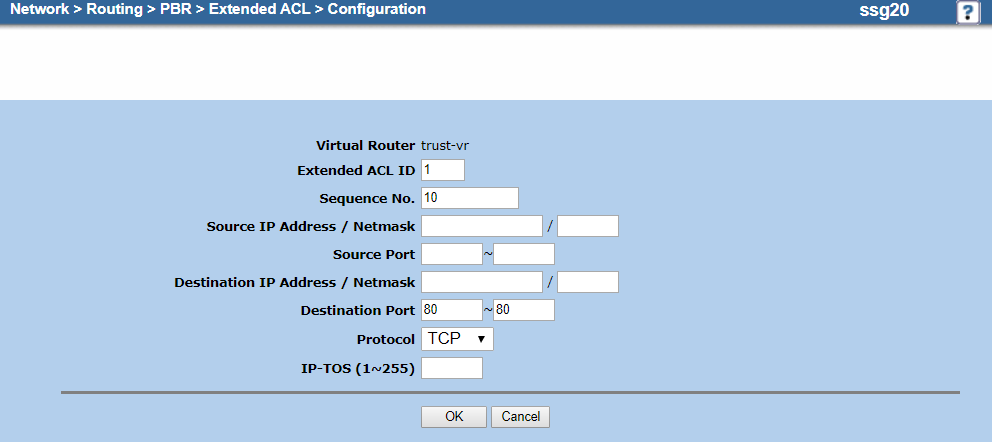
- On the extended ACL Configuration page, do the following to add an entry for TCP traffic on port 80:
- Virtual Router: It's automatically named trust-vr. You can't modify this field.
- Extended ACL ID: Enter
1. - Sequence No.: Enter
10. - Source IP Address / Netmask: Leave blank.
- Source Port: Leave blank.
- Destination IP Address / Netmask: Leave blank.
- Destination Port: Enter
80~80. - Protocol: Choose TCP.
- IP-TOS (1~255): Leave blank.
- Click OK.
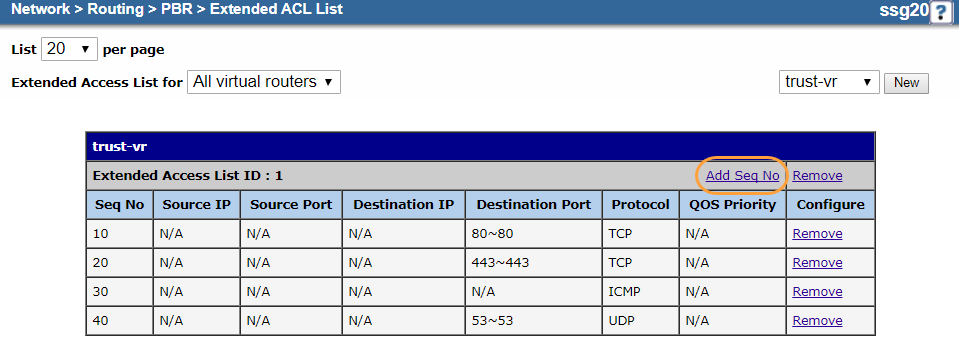
- Click Add Seq No.
- On the extended ACL Configuration page, do the following to add an entry for TCP traffic on port 443:
- Virtual Router: It's automatically named trust-vr. You can't modify this field.
- Extended ACL ID: It's automatically set to 1. You can't modify this field.
- Sequence No.: Enter
20. - Source IP Address / Netmask: Leave blank.
- Source Port: Leave blank.
- Destination IP Address / Netmask: Leave blank.
- Destination Port: Enter
443~443. - Protocol: Choose TCP.
- IP-TOS (1~255): Leave blank.
- Click OK.
- Click Add Seq. No.
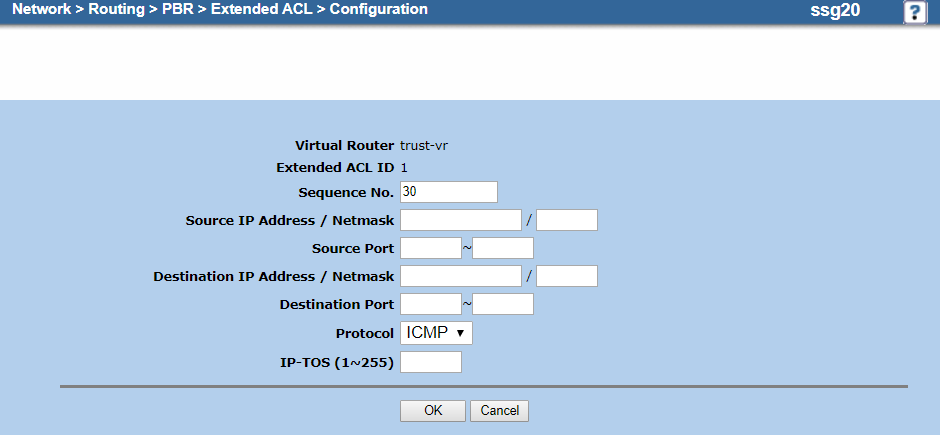
- On the extended ACL Configuration page, do the following to add an entry for ICMP traffic:
- Virtual Router: It's automatically named trust-vr. You can't modify this field.
- Extended ACL ID: It's automatically set to 1. You can't modify this field.
- Sequence No.: Enter
30. - Source IP Address / Netmask: Leave blank.
- Source Port: Leave blank.
- Destination IP Address / Netmask: Leave blank.
- Destination Port: Leave blank.
- Protocol: Choose ICMP.
- IP-TOS (1~255): Leave blank.
- Click OK.
- Click Add Seq. No.
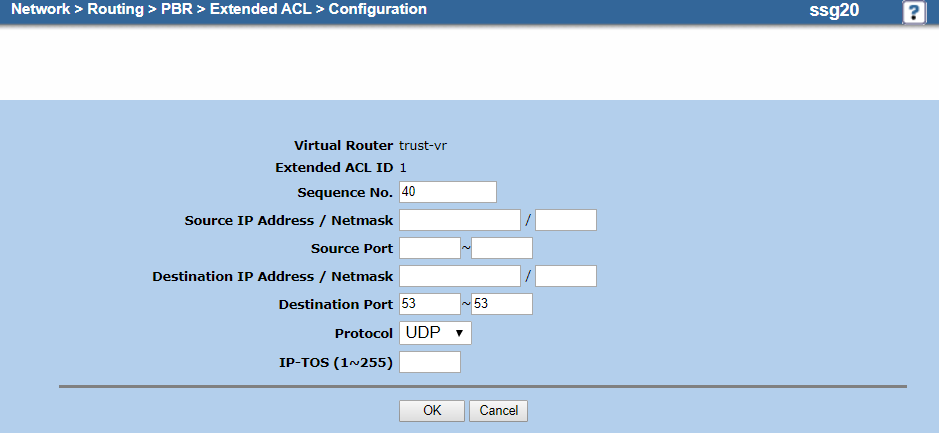
- On the extended ACL Configuration page, do the following to add an entry for UDP traffic on port 53:
- Virtual Router: It's automatically named trust-vr. You can't modify this field.
- Extended ACL ID: It's automatically set to 1. You can't modify this field.
- Sequence No.: Enter
40. - Source IP Address / Netmask: Leave blank.
- Source Port: Leave blank.
- Destination IP Address / Netmask: Leave blank.
- Destination Port: Enter
53~53. - Protocol: Choose UDP.
- IP-TOS (1~255): Leave blank.
- Click OK.
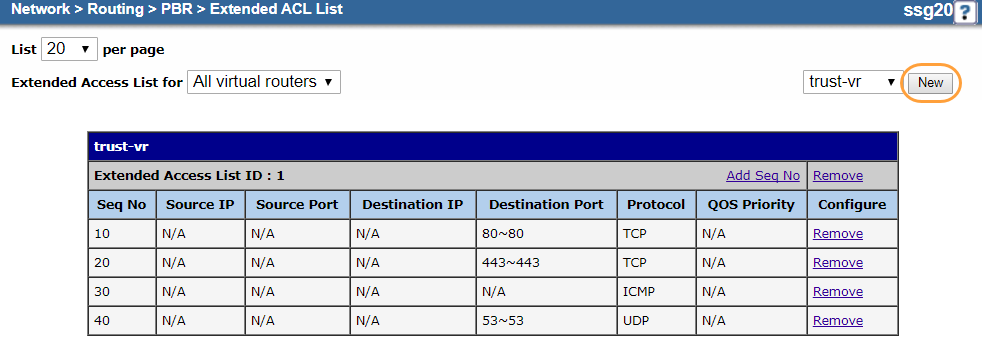
Your extended ACL configuration should look similar to the following:
Close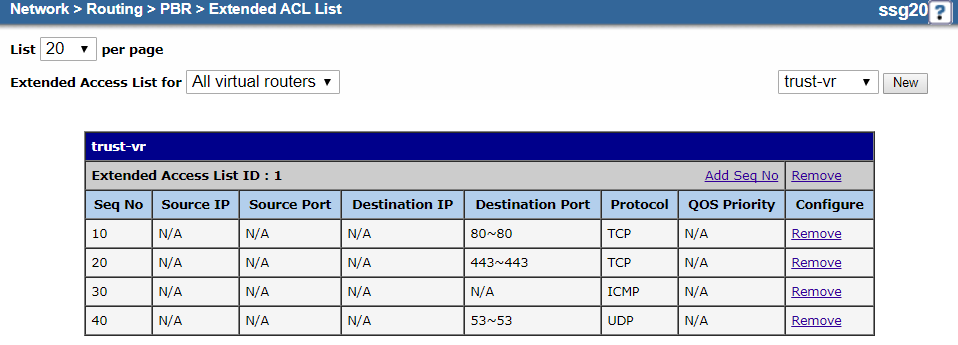
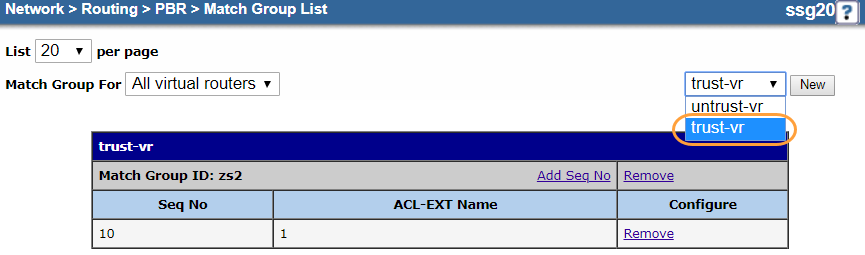
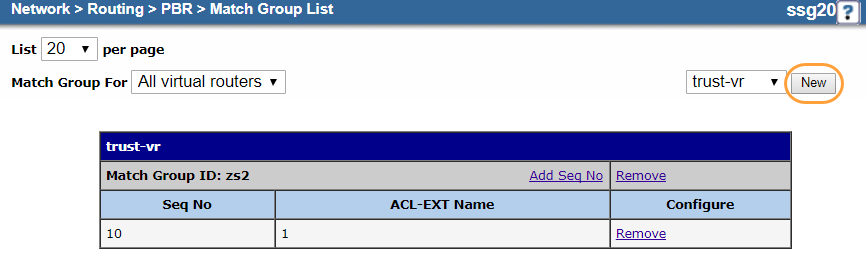
- b. Create a Match Group
Create a match group for the extended ACL.
- Go to Network > Routing > PBR > Match Group.
- In the upper-right corner, choose trust-vr.
- Click New.
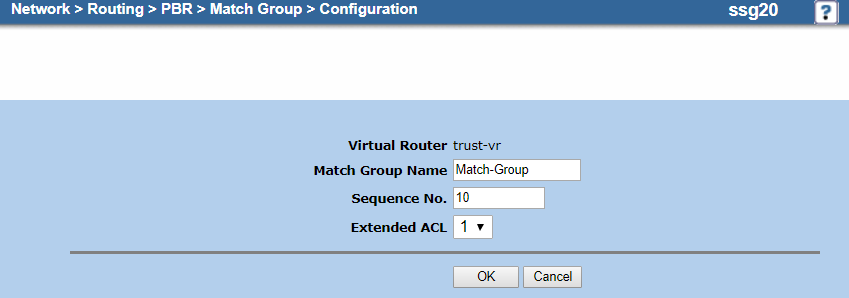
- On the match group Configuration page:
- Virtual Router: It's automatically named trust-vr. You can't modify this field.
- Match Group Name: Enter a name for the match group. In this example, it's
Match-Group. - Sequence No.: Enter
10. - Extended ACL: Choose the extended ACL you configured in a. Configure an Extended Access Control List. In this example, it's 1.
- Click OK.
Your match group configuration should look similar to the following:
Close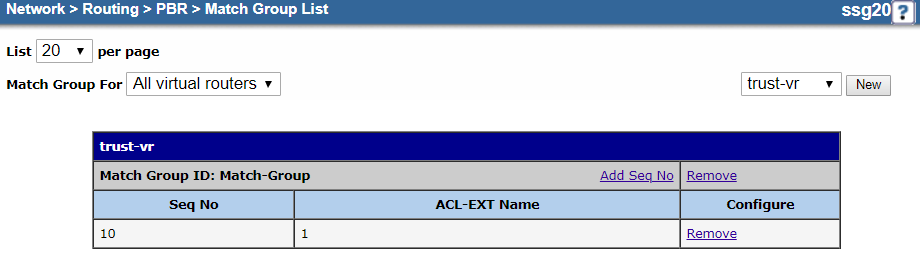
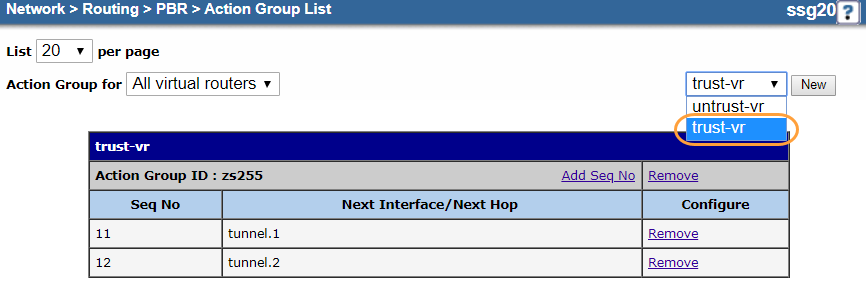
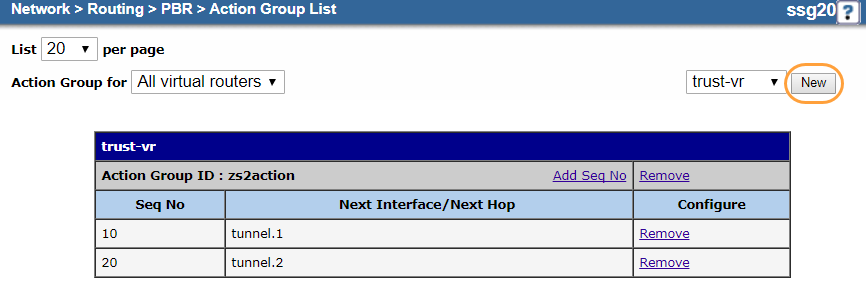
- c. Create an Action Group
Create an action group and route it to the tunnel interfaces.
- Go to Network > Routing > PBR > Action Group.
- In the upper-right corner, choose trust-vr.
- Click New.
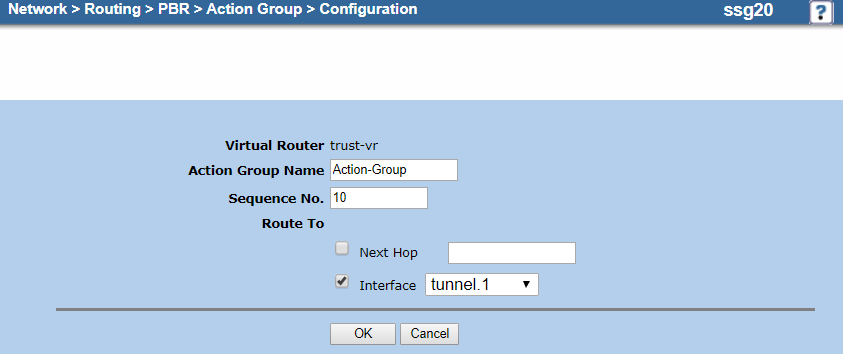
- On the action group Configuration page, do the following to add an entry for the primary tunnel interface:
- Virtual Router: It's automatically named trust-vr. You can't modify this field.
- Action Group Name: Enter a name for the action group. In this example, it's
Action-Group. - Sequence No.: Enter
10. - Route To:
- Next Hop: Leave unselected.
- Select Interface and then choose the primary tunnel interface you configured in 1. Configure the Tunnel Interfaces. In this example, it's tunnel.1.
- Click OK.
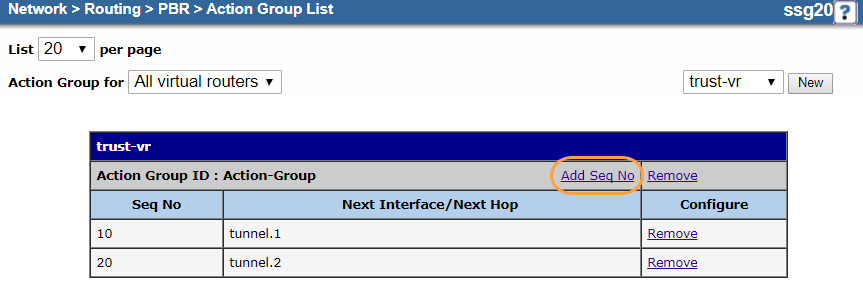
- Click Add Seq No.
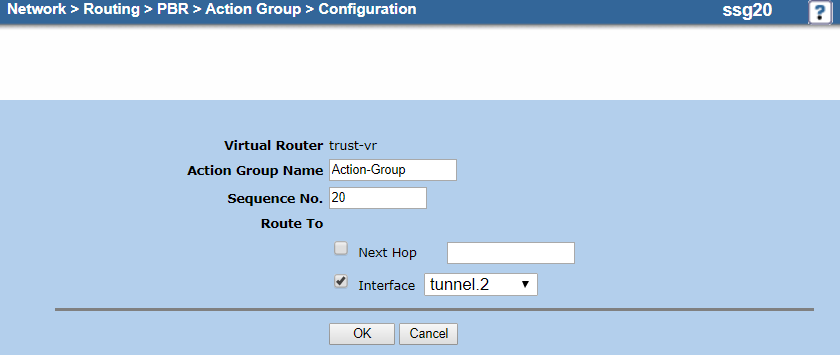
- On the action group Configuration page, do the following to add an entry for the backup tunnel interface:
- Virtual Router: It's automatically named trust-vr. You can't modify this field.
- Action Group Name: Enter the same action group name used in step d. In this example, it's
Action-Group. - Sequence No.: Enter "20".
- Route To:
- Next Hop: Leave unselected.
- Select Interface and then choose the backup tunnel interface you configured in 1. Configure the Tunnel Interfaces. In this example, it's tunnel.2.
- Click OK.
Your action group configuration should look similar to the following:
Close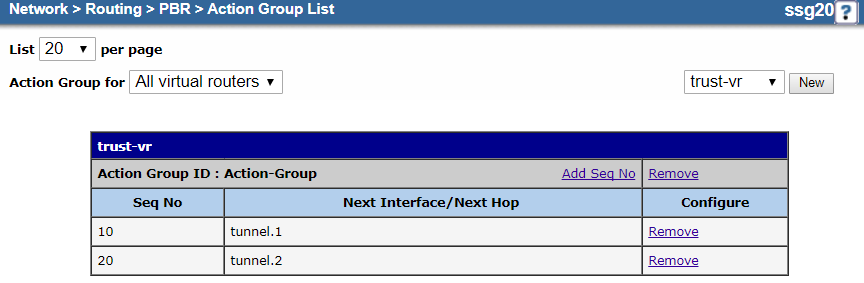
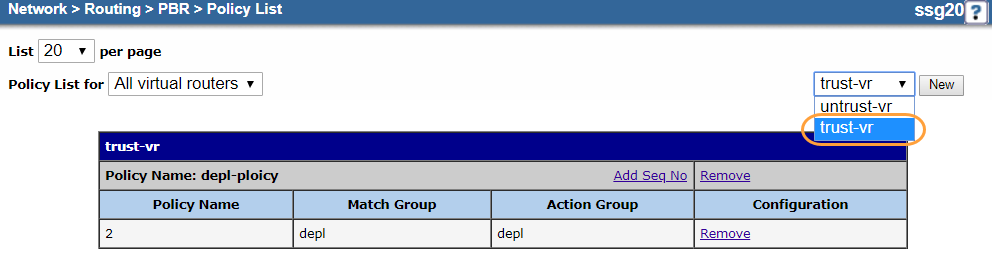
- d. Create a Policy
Create a policy for the match and action group.
- Go to Network > Routing > PBR > Policy.
- In the upper-right corner, choose trust-vr.
- Click New.
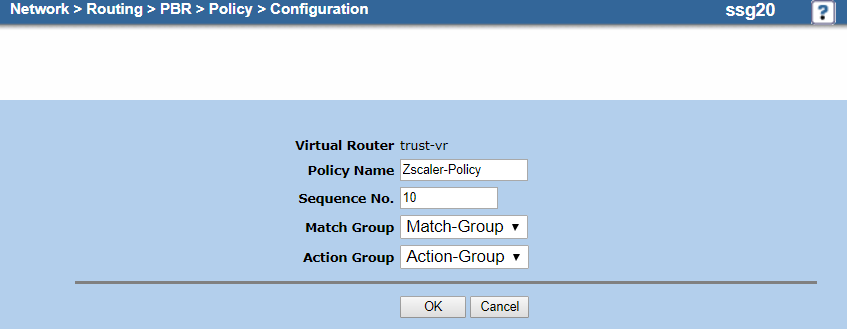
- On the policy Configuration page:
- Virtual Router: It's automatically named trust-vr. You can't modify this field.
- Policy Name: Enter a name for the policy. In this example, it's
Zscaler-Policy. - Sequence No.: Enter
10. - Match Group: Choose the match group you created in b. Create a Match Group. In this example, it's Match-Group.
- Action Group: Choose the action group you created in c. Create an Action Group. In this example, it's Action-Group.
- Click OK.
- e. Bind the Policy to the Trust Interfaces
Bind the policy to the Trust interfaces.
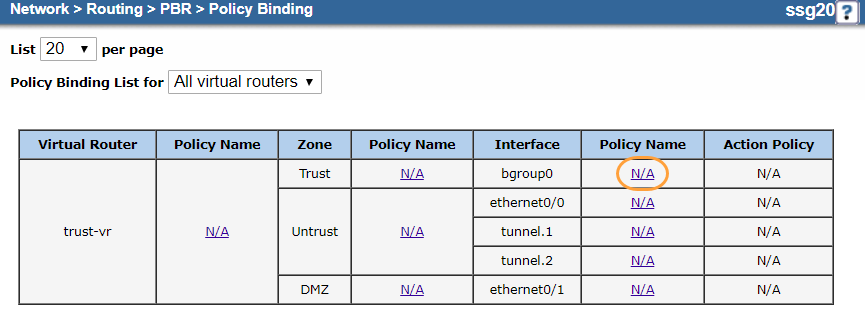
- Go to Network > Routing > PBR > Policy Binding.
- Under the Policy Name column to the right of the bgroup0 interface, click N/A.
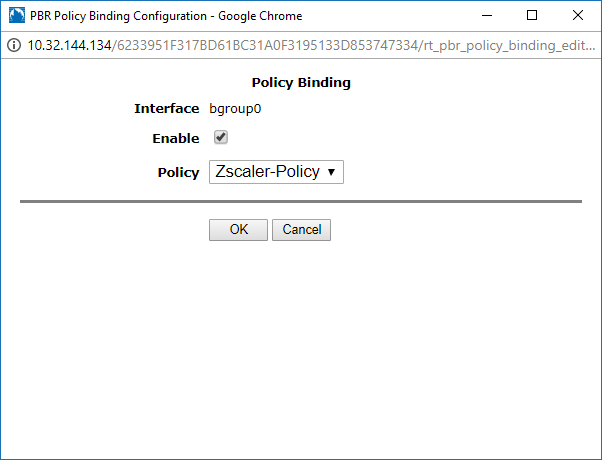
- In the Policy Binding window:
- Interface: It's automatically named bgroup0. You can't modify this field.
- Select Enable.
- Policy: Choose the policy you created in d. Create a Policy. In this example, it's Zscaler-Policy.
- Click OK.
- Repeat the procedure to bind the policy to the wireless0/0 interface.
- f. Create Policies for the Security Zones
Create two policies, one policy that allows traffic from the Trust to the Untrust zone and another policy that allows traffic from the Untrust to the Trust zone.
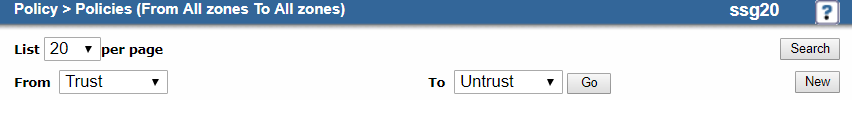
- Go to Policy > Policies.
- On the Policies page:
- From: Choose Trust.
- To: Choose Untrust.
- Click New.
- On the Policies (From Trust to Untrust) page:
- Name (optional): Leave blank.
- Source Address: Select Address Book Entry and then choose Any from the drop-down menu.
- Destination Address: Select Address Book Entry and then choose Any from the drop-down menu.
- Service: Choose Any.
- Application: Choose None.
- WEB Filtering: Leave unselected.
- Action: Choose Permit.
- Tunnel:
- VPN: Choose None.
- Modify matching bidirectional VPN policy: Leave unselected.
- L2TP: Choose None.
- Logging: Leave unselected.
- Position at Top: Leave unselected.
- Session-limit: Leave unselected.
- Counter: Enter
0. - Alarm without drop: Leave unselected.
- Click OK.
- Repeat the procedure to configure a second policy that allows traffic from Untrust to Trust.
Your policy configuration should look similar to the following:
Close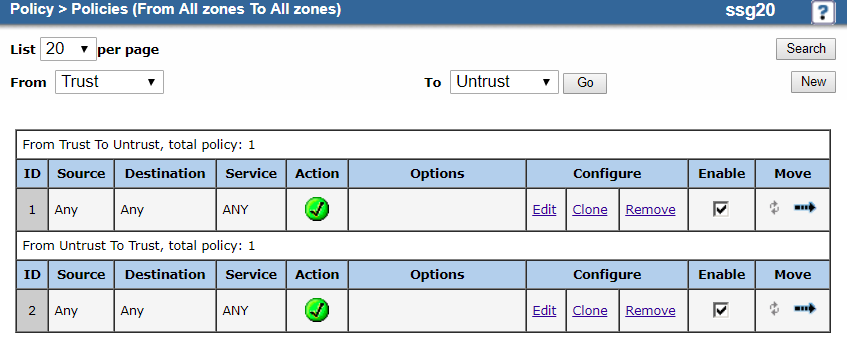
- a. Configure an Extended Access Control List
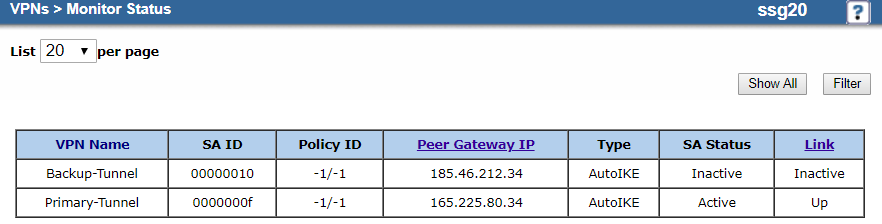
After completing the configuration, you can go to VPNs > Monitor Status to see the status of the IPSec VPN tunnels.
Testing the Configuration
You can test the configuration by browsing from the Trust zone (through the wireless or bgroup0 LAN ports) to any website. You must log in to the Zscaler cloud before you can access the site.
Troubleshooting
In the ZIA Admin Portal, you can go to Analytics > Tunnel Insights to see data as well as monitor the health and status of your configured IPSec VPN tunnels. To learn more, see About Insights and About Insights Logs.
On the SSG 20 device, you can use the following CLI commands to monitor and troubleshoot the IPSec VPN tunnels.
- Viewing the SA
Use the
get sacommand to view SAs and to check the status of the tunnel. In the following response, the "sta"ssg5-serial-wlan-> get sa total configured sa: 2 HEX ID Gateway Port Algorithm SPI Life:sec kb Sta PID vsys 00000014< 10.10.104.71 500 esp:null/md5 00000000 expir unlim I/I -1 0 00000014> 10.10.104.71 500 esp:null/md5 00000000 expir unlim I/I -1 0 00000015< 10.10.104.235 500 esp:null/md5 33511797 2149 unlim A/U -1 0 00000015> 10.10.104.235 500 esp:null/md5 008a8a67 2149 unlim A/U -1 0
Use the get sa active command to check the active SAs:
Total active sa: 1 total configured sa: 2 HEX ID Gateway Port Algorithm SPI Life:sec kb Sta PID vsys 00000015< 10.10.104.235 500 esp:null/md5 33511797 2048 unlim A/U -1 0 00000015> 10.10.104.235 500 esp:null/md5 008a8a67 2048 unlim A/U -1 0
Use the get sa stat command to check the active SAs
total configured sa: 2 HEX ID Gateway Fragment Auth-Fail Other Totalbytes 00000014< 10.10.104.71 0 0 0 0 00000014> 10.10.104.71 0 0 0 0 00000015< 10.10.104.235 0 0 0 345976469 00000015> 10.10.104.235 0 0 0 32472216
Use the get sa id 20 command to check the active SAs
index 0, name VPN-71, peer gateway ip 10.10.104.71. vsys<Root> auto key. tunnel if binding node, tunnel mode, policy id in:<-1> out:<-1> vpngrp:<-1>. sa_list_nxt:<0xffffffff>. tunnel id 20, peer id 0, NSRP Local. site-to-site. Local interface is ethernet0/0 <10.10.120.41>. esp, group 2, null encryption, md5 authentication autokey, IN inactive, OUT inactive monitor<1>, latency: -1, availability: 0 DF bit: clear app_sa_flags: 0x5000a4 proxy id: local 0.0.0.0/0.0.0.0, remote 0.0.0.0/0.0.0.0, proto 0, port 0 ike activity timestamp: 1782025 nat-traversal map not available incoming: SPI 00000000, flag 00004000, tunnel info 40000014, pipeline life 0 sec, expired, 0 kb, 0 bytes remain anti-replay on, last 0x0, window 0x0, idle timeout value <0>, idled 1744 seconds next pak sequence number: 0x0 outgoing: SPI 00000000, flag 00000000, tunnel info 40000014, pipeline life 0 sec, expired, 0 kb, 0 bytes remain anti-replay on, last 0x0, window 0x0, idle timeout value <0>, idled 1744 seconds next pak sequence number: 0x0 ssg5-serial-wlan-> get sa id 21 index 1, name vpn-81, peer gateway ip 10.10.104.235. vsys<Root> auto key. tunnel if binding node, tunnel mode, policy id in:<-1> out:<-1> vpngrp:<-1>. sa_list_nxt:<0xffffffff>. tunnel id 21, peer id 1, NSRP Local. site-to-site. Local interface is ethernet0/0 <10.10.120.41>. esp, group 2, null encryption, md5 authentication autokey, IN active, OUT active monitor<1>, latency: 1, availability: 100 DF bit: clear app_sa_flags: 0x4000a7 proxy id: local 0.0.0.0/0.0.0.0, remote 0.0.0.0/0.0.0.0, proto 0, port 0 ike activity timestamp: 1732254 nat-traversal map not available incoming: SPI 33511799, flag 00004000, tunnel info 40000015, pipeline life 3600 sec, 3537 remain, 0 kb, 0 bytes remain anti-replay on, last 0x1724, window 0xffffffff, idle timeout value <0>, idled 0 seconds next pak sequence number: 0x0 outgoing: SPI 01c2e484, flag 00000000, tunnel info 40000015, pipeline life 3600 sec, 3537 remain, 0 kb, 0 bytes remain anti-replay on, last 0x0, window 0x0, idle timeout value <0>, idled 0 seconds next pak sequence number: 0xc52 ssg5-serial-wlan->
Close - Clearing the SA