Experience Center
Configuring the Default Sandbox Rule
The default rule for the Sandbox policy blocks all Windows executables and Windows library files from suspicious URLs that contain certain malicious file types. Additionally, if a user downloads a Windows executable or Windows library file from a suspicious URL, and it contains an unknown file, the default action is to allow users to download the file then send the file to the Sandbox engine for analysis.
To configure the default Sandbox rule:
- Step 1: Enable Inbound and Outbound Traffic Inspection
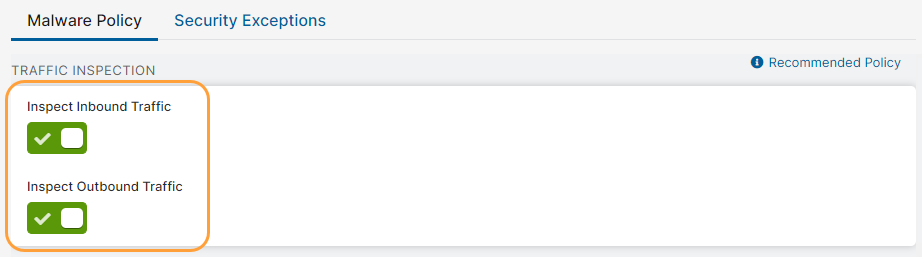
You must enable inbound and outbound traffic inspection in your Malware Protection policy to have files sent for sandboxing.
To enable inbound and outbound traffic inspection:
- Go to Policies > Cybersecurity > Inline Security > Malware Protection.
Enable Inspect Inbound Traffic and Inspect Outbound Traffic.
- Click Save and activate the change.
The Sandbox only analyzes files that are downloaded (inbound).
Close - Step 2: Edit the Default Sandbox Rule
You can change the settings of the default Sandbox rule, but you can't delete it. Zscaler recommends that you don't change the default settings.
To edit the default Sandbox rule:
- Go to Policies > Cybersecurity > Inline Security > Sandbox.
Click the Edit icon next to the default rule.
The Edit Sandbox Rule window appears.
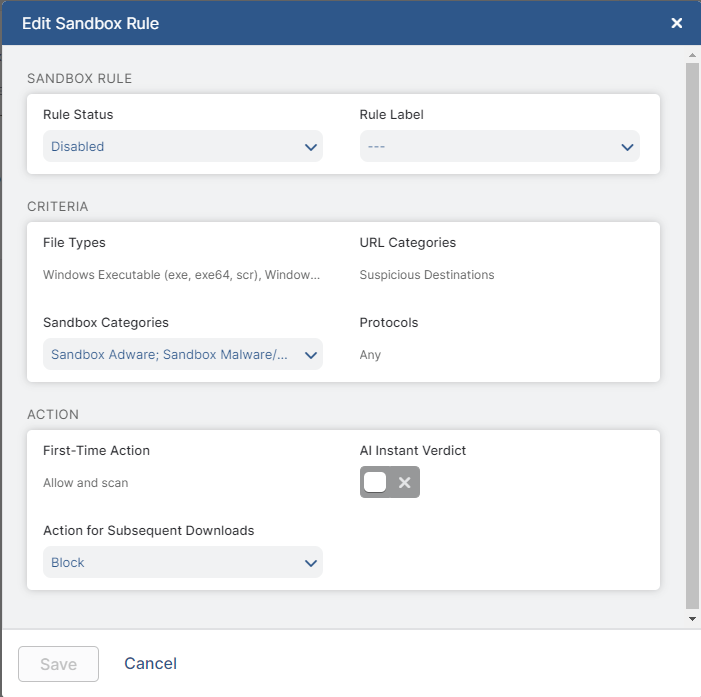
In the Edit Sandbox Rule window:
- Rule Status: The default Sandbox rule is enabled and enforced. You can modify this field, but Zscaler doesn't recommend doing so.
- Rule Label: The default rule is associated with the selected label. You can modify this field.
- File Types: The default rule analyzes Windows executables and Windows library files. It also analyzes these files if they’re contained in ZIP archive files (.zip). With the Standard Sandbox subscription, the service only analyzes files that are equal to 2 MB or less. You can't modify this field.
URL Categories: The default rule analyzes the file types above if they are downloaded from URLs in Suspicious Destinations. Suspicious destinations include the following URL categories:
- Nudity
- Pornography
- Anonymizer
- FileHost
- Shareware Download
- Web Host
- Miscellaneous or Unknown
- Other Miscellaneous
You can't modify this field.
- Sandbox Categories: The default rule applies to the following malicious file types
- Sandbox Adware: Files that automatically render advertisements/install adware. Often, these advertisements are unwanted and can lead to spyware or other grayware-oriented privacy violations.
- Sandbox Malware/Botnet: Files that behave like APTs, exploits, botnets, trojans, keyloggers, spyware, and other malware. This is a catchall category for any malicious file that doesn't fall under the other Sandbox categories. Most Sandbox-classified files aren't clearly known to be a specific threat or malware family-oriented because there aren't specific signatures or indicators to categorize the file. Instead the Zscaler service categorizes the file based on an aggregation of the file’s OS and application behaviors and network activity.
- Sandbox P2P/Anonymizer: Files that contain anonymizers and P2P clients. The Zscaler service detects if the file is exhibiting behavior consistent with P2P/anonymizer programs, such as Tor Browser or other VPN services, that essentially make a user’s internet activity untraceable.
ZPA Application Segment: Inspection of application segments of Private Applications for security and data protection services enables leveraging single posture for securing internet & SaaS and Private Applications.
Select up to 255 application segments of Private Applications. Selecting no value ignores the criterion in the policy evaluation. The list displays only those application segments of Private Applications that have the Source IP Anchor option enabled.You can make changes if necessary, but Zscaler recommends that you don't modify this field.
Protocols: The default rule applies to file downloads from the following protocols.
- FTP over HTTP: File downloads from FTP over HTTP websites.
- HTTP: File downloads from HTTP websites.
- HTTPS: File downloads from HTTP websites encrypted by TLS/SSL.
- Native FTP: File downloads from native FTP servers.
You can't modify this field.
- First-Time Action: If a user downloads a Windows executable or Windows library file from a suspicious URL, and it contains an unknown file, the default action is to allow users to download the file then send the file to the Sandbox engine for analysis. You can't modify this field.
- AI Instant Verdict: This field is applicable only if the First-Time Action is Quarantine or Allow and Scan. You can’t modify this field for the default sandbox rule.
Action for Subsequent Downloads: The default action is to Block Sandbox classified files (files the Sandbox previously analyzed) that match the criteria above. If a user attempts to download a malicious Sandbox classified file, the service displays a block notification and prevents the download.
If you choose Allow, the service allows users to download the files even if they're malicious, but logs the transactions. You can modify this field, but Zscaler doesn't recommend doing so.
Click Save.
- Click Save and activate the change.
If a file doesn't match the criteria of the default Sandbox rule, then the file download is allowed even if it's malicious.
Close
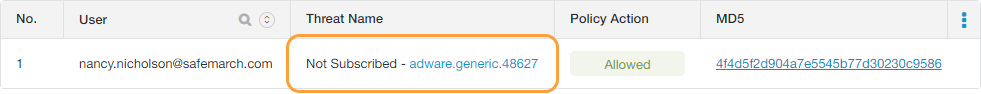
The Zscaler service logs all Sandbox transactions on the Web Insights Logs page. If a malicious file is allowed because it doesn't match criteria of the default Sandbox rule, the Zscaler service displays Not Subscribed in the Threat Name column.