Experience Center
Configuring AppProtection Profiles
Within the Admin Portal, you can add AppProtection profiles to use in AppProtection policies. For a complete list of ranges and limits for AppProtection profiles, see Ranges & Limitations.
To add an AppProtection profile:
- Go to Policies > Cybersecurity > Inline Security > Protection Profiles > AppProtection.
- Click Add AppProtection Profile.
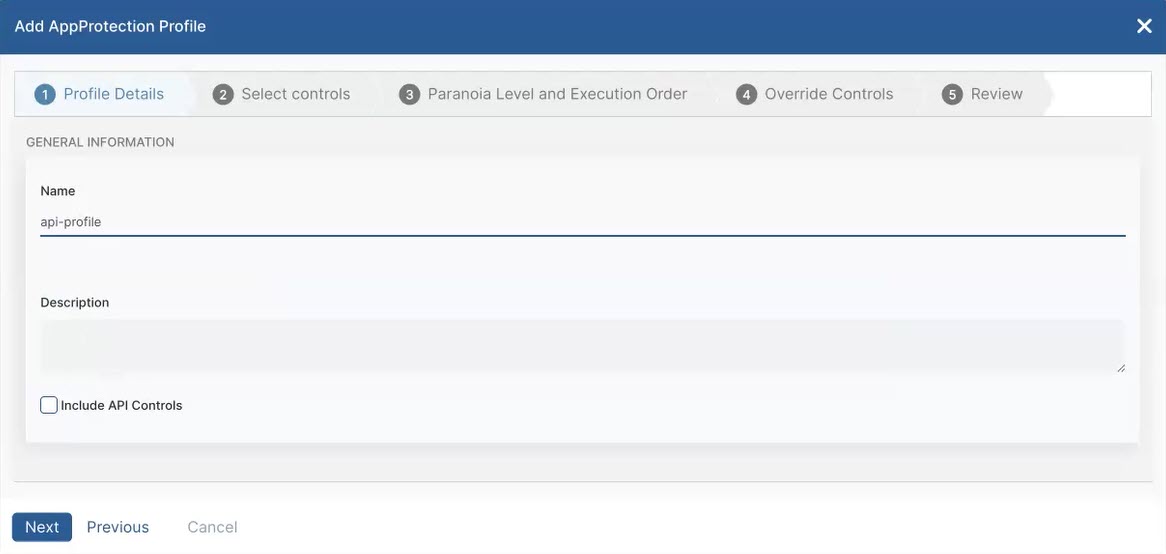
The Add AppProtection Profile window appears. - In the Add AppProtection Profile window, enter the following information:
- Step 1: Profile Details
- Enter the relevant details in the General Information section:
- Name: Enter a name for the AppProtection profile. The name cannot contain special characters, with the exception of periods (.), hyphens (-), and underscores ( _ ).
- Description: (Optional) Enter a description.
- (Optional) Select the Include API Controls checkbox to display the API Controls option in the next step. API Controls are only available if you have already designated application segments for API Protection.
- Click Next.
- Enter the relevant details in the General Information section:
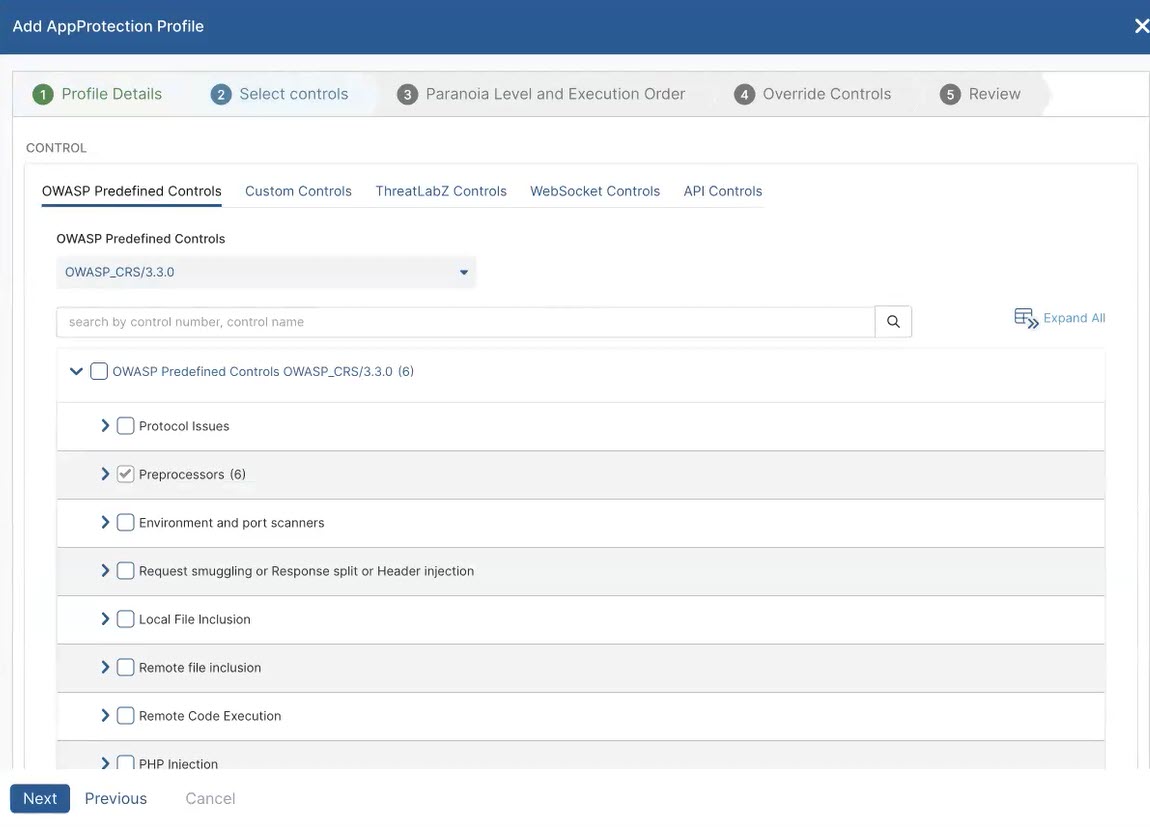
- Step 2: Select Controls
- On the Select Controls tab, choose from the OWASP Predefined Controls, Custom Controls, ThreatLabZ Controls, WebSocket Controls, and API Controls you have defined. Use the latest version of OWASP predefined controls.
API Controls are only available if you have already designated application segments for API Protection and selected the Include API Controls checkbox.
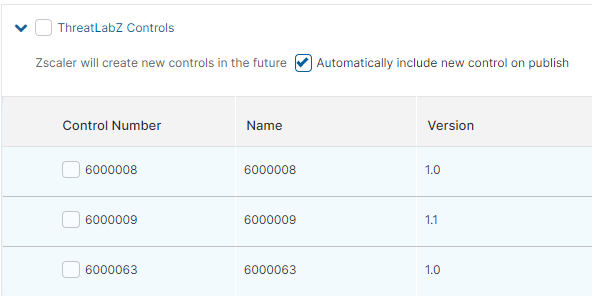
All AppProtection profiles automatically have some OWASP predefined controls from the Preprocessors category enabled. They have a default action of Block, and you cannot override the action. You can view the Preprocessors in the expanded view of the OWASP predefined controls table.
Rule 920274 blocks traffic containing characters beyond a restricted set. Most browsers and applications may include headers containing characters not included in this character set. This may result in blocking a large number of non-malicious requests.
If you select ThreatLabZ Controls, you can select the checkbox that allows Zscaler to automatically add any new ThreatLabZ predefined controls to the AppProtection profile that is published. If the checkbox isn’t selected, the ThreatLabZ predefined controls need to be manually added to the AppProtection profile.
- Click Next.
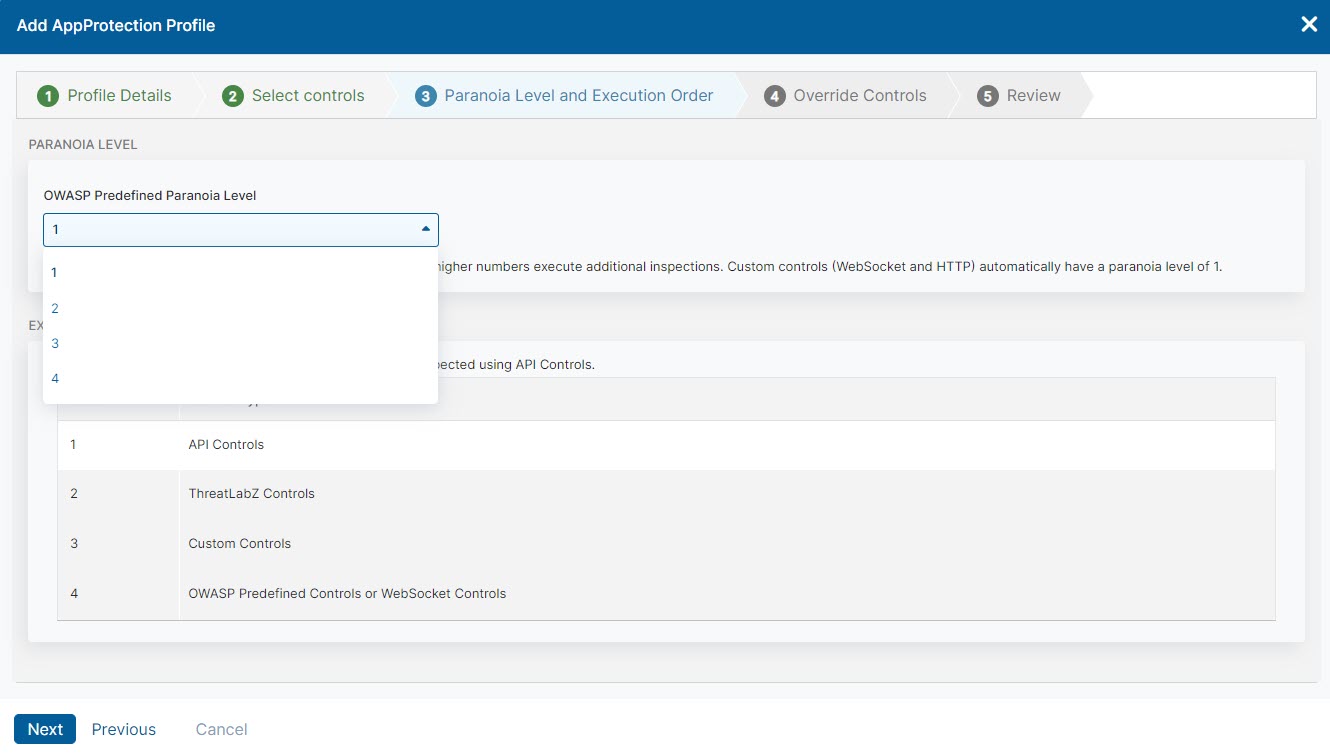
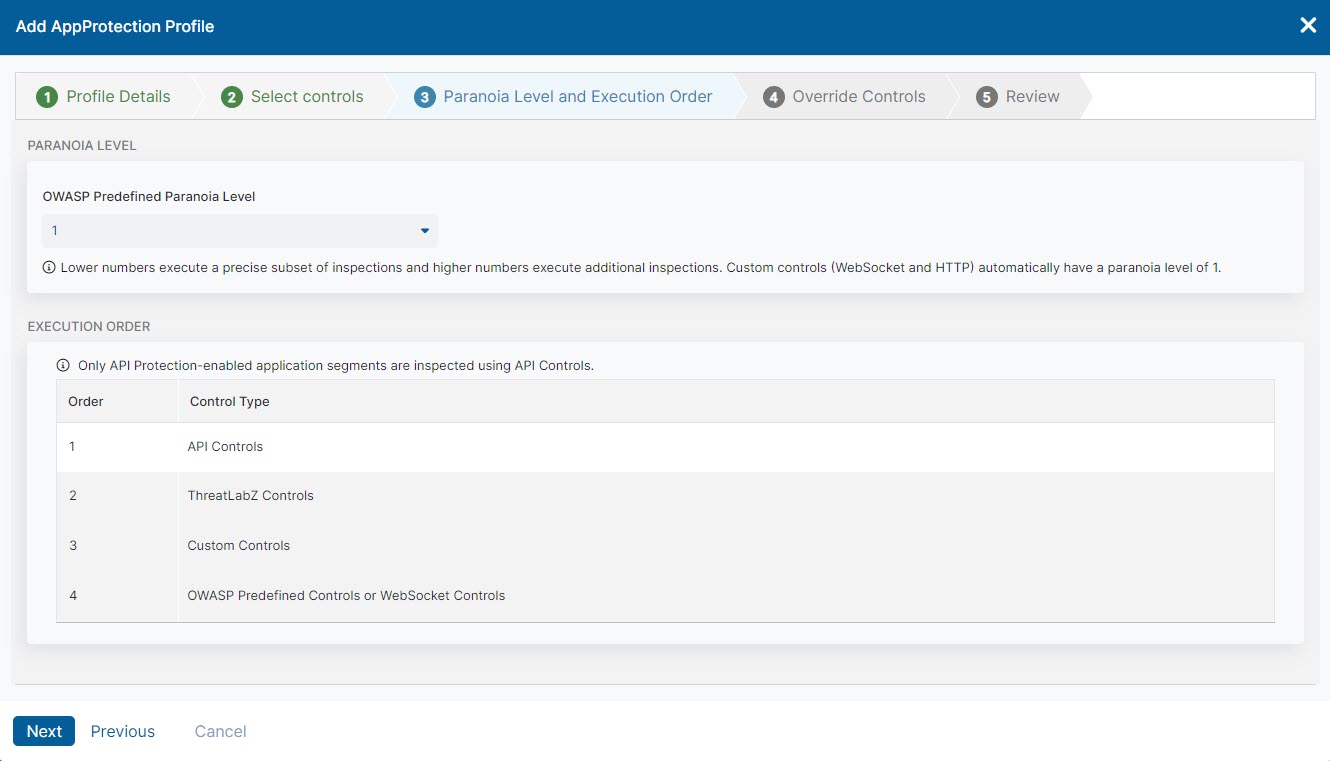
- Step 3: Paranoia Level and Execution Order
Custom controls (either HTTP or WebSocket) have a paranoia level of 1.
- Choose a Paranoia Level from 1 to 4 with 1 being the highest level of concern and 4 being the least level of concern.
Higher paranoia levels execute checks using a wide net of matches that increases the potential for false positives. Lower paranoia levels execute checks using a precise set of matches resulting in fewer chances of false positives.
- Review the Execution Order. No further action is required.
If you select custom (HTTP or WebSocket) and predefined controls (ThreatLabZ, OWASP, WebSocket, or API), API controls are executed first, then ThreatLabZ controls, then custom controls, then other predefined controls (OWASP and WebSocket).
- Click Next.
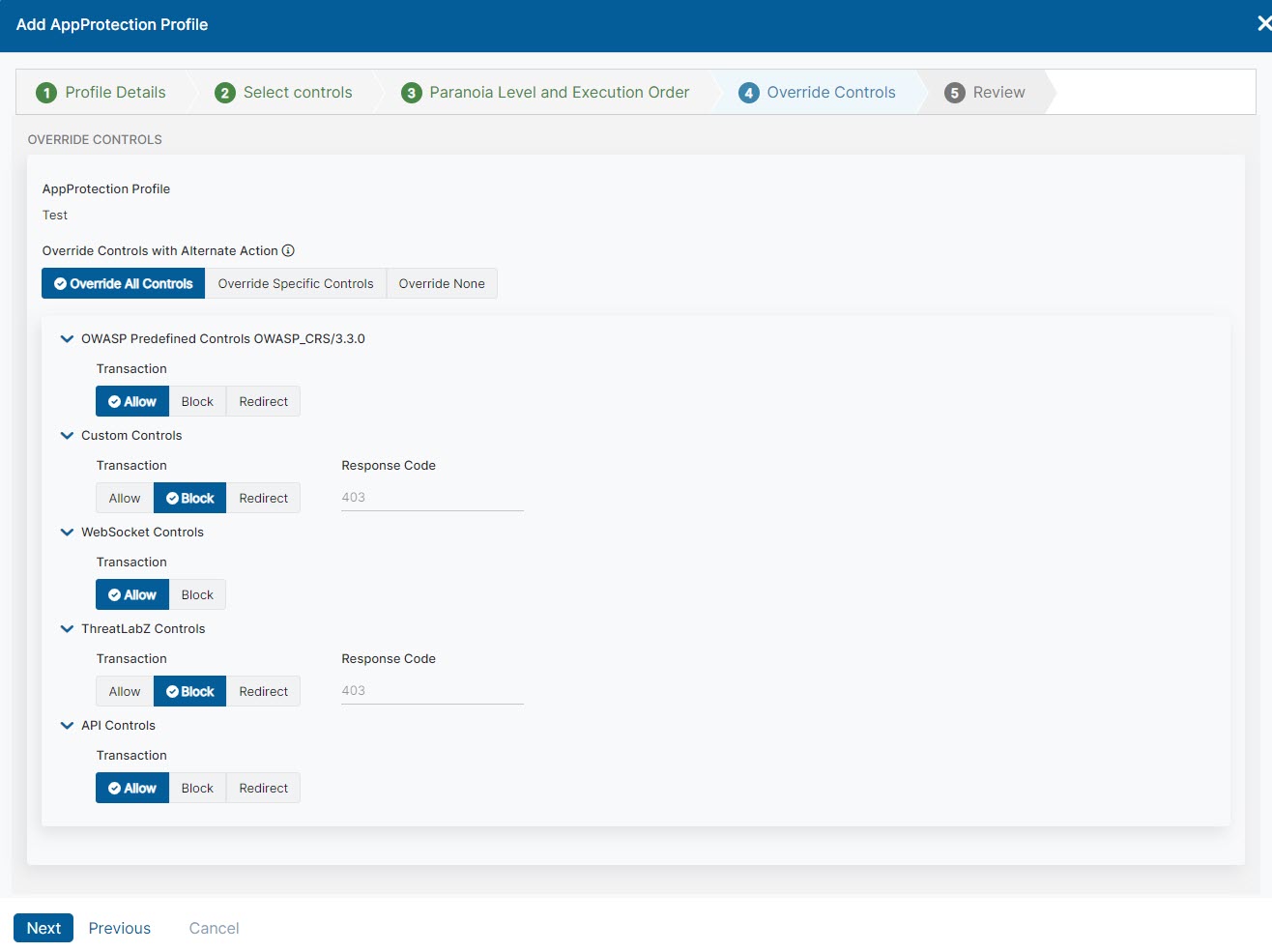
- Step 4: Override Actions
You can set up the AppProtection policy to perform no override actions (None) or various types of override actions (Common and Specific). This can be as exact as setting a different action for inspecting transaction traffic on each previously selected ThreatLabZ control, OWASP predefined control, WebSocket control, custom control, and API control.
If using the Common or Specific override action options, consider initially setting the default action to Allow for rules with a higher paranoia level. This provides visibility without denying access.
- Select if you want to allow the AppProtection policy to override controls to perform a different action for inspecting traffic:
- Common
Choose one of the standard override options for all of the API controls, ThreatLabZ Controls, OWASP predefined controls, WebSocket controls, and/or all custom controls:
- Allow: The user is allowed to proceed with the current URL.
- Block: The user receives a 403 response code.
- Redirect: The user receives a different URL. Enter an alternative URL that the user will be redirected to.
- Specific
- Select the specific API controls, ThreatLabZ controls, OWASP predefined controls, WebSocket controls, and/or custom controls where you want to set override actions.
If you subscribe to automatic updates for ThreatLabZ controls, you can only use the Common override option.
- Choose one of the override options for each control selected:
- Allow: The user is allowed to proceed with the current URL.
- Block: The user receives a 403 response code.
- Redirect: The user receives a different URL. Enter an alternative URL that the user is redirected to.
Access to an IP-based application fails when it is linked to an AppProtection profile using the 920350 rule and Block action.
Close - None
No override action occurs for any of the controls. This is the default option.
Close
- Click Next.
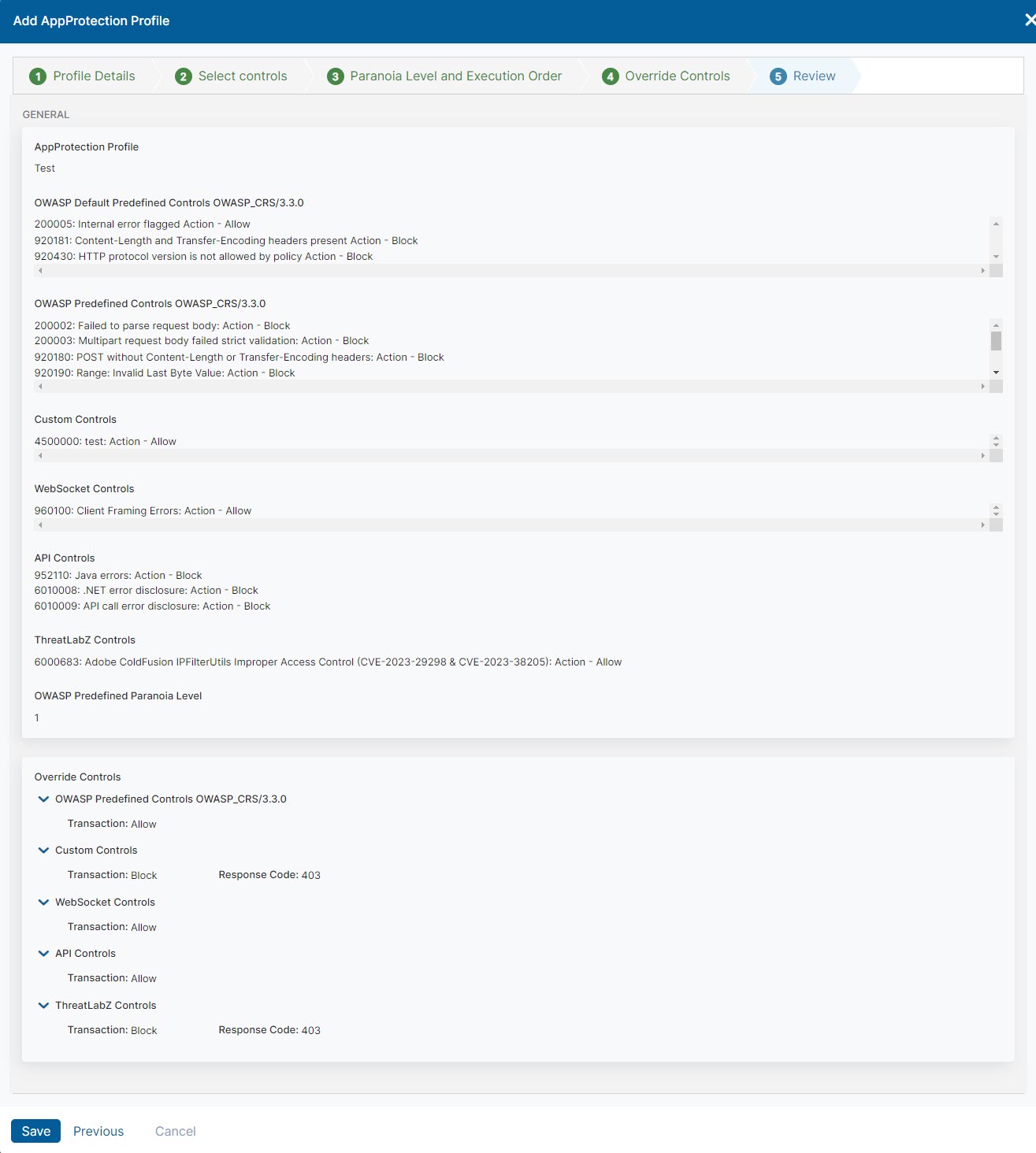
- Step 5: Review
- Click Save.