Experience Center
Configuring AppProtection Policies
AppProtection policy rules enable you to implement AppProtection control. For a complete list of ranges and limitations for AppProtection policy rules, see Ranges & Limitations.
To configure an AppProtection policy rule:
- Go to Policies > Cybersecurity > Inline Security > Protection Policies.
- Click Add Rule.
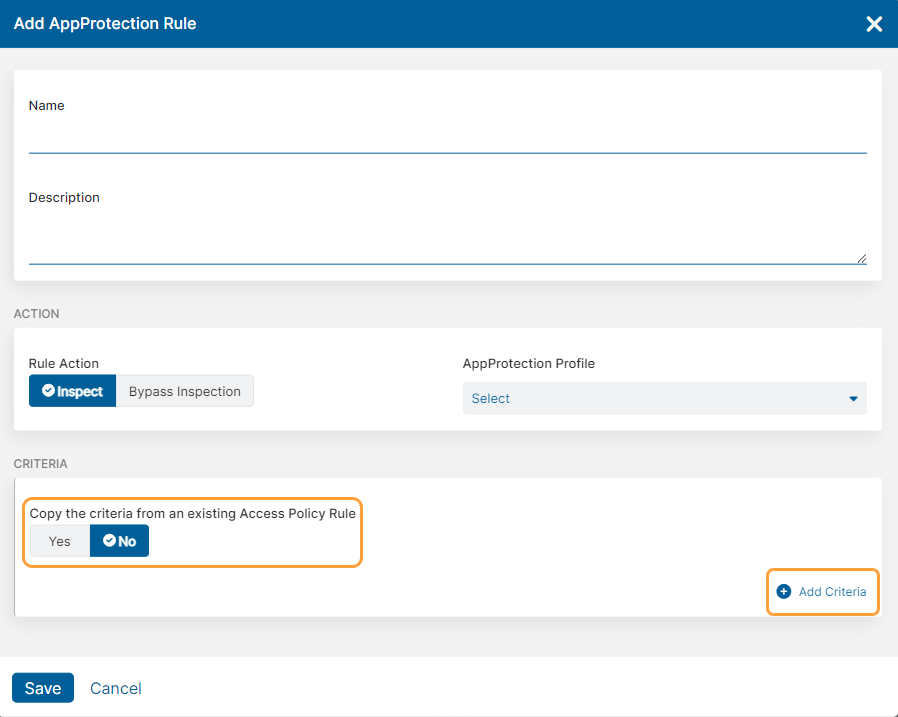
The Add AppProtection Policy window appears. - In the Add AppProtection Policy window, enter the following information:
- Name: Enter an AppProtection policy name. The name cannot contain special characters, with the exception of periods (.), hyphens (-), and underscores ( _ ).
- Description: (Optional) Enter a description.
- For the Action section, choose the configuration information for the following items:
- Rule Action: Select Inspection or Bypass Inspection.
- AppProtection Profile: Choose an AppProtection profile that is a security profile with a set of common or control specific actions.
- For the Criteria section, you can either:
- Copy from an existing Access Policy’s criteria by selecting Yes for Copy the criteria from an existing Access Policy Rule and choosing an existing Access Policy. The criteria from that access policy appears. You can modify the criteria if you want to adjust it for this AppProtection policy rule.
- Choose the criteria you want to use by clicking Add Criteria to add any of the available criteria types. The drop-down menu only displays criteria that are not already in use by the rule, except for Client Connector Posture Profile condition sets. You can add up to 10 condition sets.
- Applications
Choose the application segments and segment groups to which this rule applies:
- Application Segments: Choose the application segments, and click Done. You can search for a specific application segment, click Select All to apply all applications segments, or click Clear Selection to remove all selections. The application segments you've configured appear in the menu. There is no limit to the number you can select.
If you added multiple application segments to the policy rule, an OR Boolean operator is used between them.
There are limits to the number of application segments applied to a rule. For a complete list of ranges and limitations for AppProtection Policy rules, see Ranges & Limitations.
- Segment Groups: Choose the segment groups, and click Done. You can search for a specific segment group, click Select All to apply all segment groups, or click Clear Selection to remove all selections. The segment groups you've configured appear in the menu. There is no limit to the number you can select.
If you added multiple segment groups to the policy rule, an OR Boolean operator is used between them.
Close - Client Connector Posture Profiles
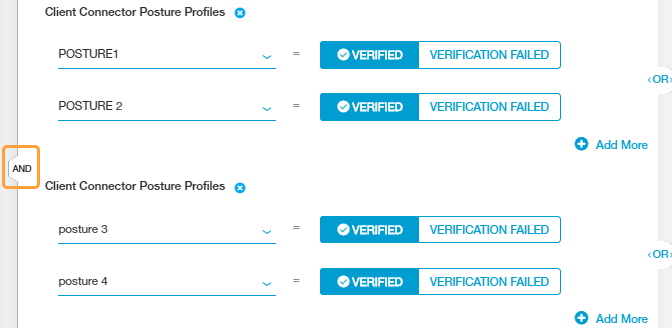
Choose the condition sets to which the rule applies. You can add up to 10 Client Connector Posture Profile condition sets to the rule. Click Add Criteria to include additional sets.
Each condition set can contain multiple posture profiles to enforce on a user’s device. For each profile, select one of the following:
- VERIFIED: Zscaler Client Connector verified the user's device against the criteria specified in the posture profile.
- VERIFICATION FAILED: Zscaler Client Connector was unable to verify the user's device against the criteria specified in the posture profile.
Make sure you have configured the posture profiles within the Zscaler Client Connector Portal. The posture profiles you configure in the Zscaler Client Connector Portal appear in the drop-down menu, where you can search for a specific profile.
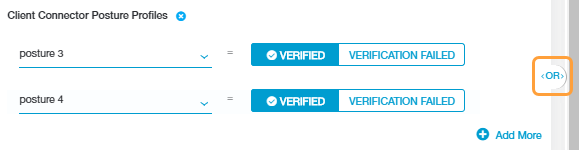
If you added multiple posture profile condition sets to the policy rule, an AND Boolean operator is used between them. Each posture profile condition set is evaluated individually.
If you added multiple posture profiles within a posture profile condition set, an OR Boolean operator is used between them by default. However, you can toggle this to an AND operator by clicking on it.
Close - Client Connector Trusted Networks
Choose the trusted networks to which the rule applies, and click Done. You can search for a specific trusted network, click Select All to have the rule apply to all trusted networks, or click Clear Selection to remove all selections. The trusted networks you've configured appear in the menu. There is no limit to the number you can select.
A forwarding profile tells Zscaler Client Connector how to treat traffic from your users' systems in different network environments. When a user connects to a network, Zscaler Client Connector checks to determine what type of network the user is connected to.
If you added multiple trusted networks to the policy rule, then an OR Boolean operator is used between them.
Make sure you have configured your Trusted Network Criteria within the Zscaler Client Connector Portal. The trusted networks you configure in the Zscaler Client Connector Portal appear in the drop-down menu.
Close - Client Types
Choose the client types to which the rule applies, and click Done. You can search for a specific client type, click Select All to apply all client types, or click Clear Selection to remove all selections. The valid client types are:
- Client Connector
- Cloud Browser
- Cloud Connector
- Machine Tunnel: To learn more, see About Machine Tunnels.
- Web Browser: To learn more, see About Browser Access.
- ZIA Service Edge: To learn more, see Understanding Source IP Anchoring.
If you added multiple client types to the policy rule, an OR Boolean operator is used between them.
Rules using the Web Browser or ZIA Service Edge client types can not also use posture profiles or trusted networks criteria. The posture profiles or trusted networks criteria only work with Client Connector.
Close - Cloud Connector Groups
The Cloud Connector Group criteria type cannot be configured with the SAML and SCIM Attributes criteria type.
Choose the Cloud Connector groups to which the policy applies, and click Done. You can search for a specific Cloud Connector group, click Select All to apply all Cloud Connector groups, or click Clear Selection to remove all selections. The Cloud Connector groups you've configured appear in the menu. There is no limit to the number you can select.
If you've added multiple Cloud Connector groups to the policy rule, an AND Boolean operator is used between them.
Close - Machine Groups
Choose the Machine groups to which this rule applies, and click Done. You can search for a specific Machine group, click Select All to apply all groups, or click Clear Selection to remove all selections. The Machine groups you've configured appear in the menu. There is no limit to the number you can select.
If a Machine group is selected, Machine Tunnel as a client type is required as well.
Close - Platforms
Choose the platforms to which the rule applies and click Save. This allows you to control which applications are designated to which devices. The valid platform types are:
- Windows
- macOS
- Linux
- iOS
- Android
If you added multiple platforms to the policy rule, then an OR Boolean operator is used between them.
Close - SAML and SCIM Attributes or Session and User Attributes
- If you are subscribed to ZIdentity for users, the SAML and SCIM Attributes criteria is replaced with Session and User Attributes. To learn more, see What Is ZIdentity?
- The SAML and SCIM Attributes criteria type cannot be configured with the Cloud Connector Group criteria type.
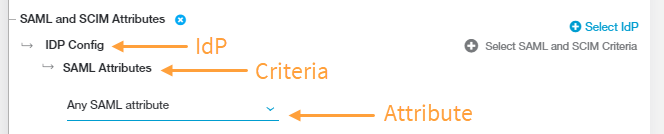
- Click Select IdP and choose the identity provider (IdP) configuration you want to include in the policy rule. The IdP must be configured for User SSO. To learn more, see Configuring an IdP for Single Sign-On. If you need to include multiple IdPs in the policy rule, click Select IdP again.
- Click Select SAML and SCIM Criteria to add the criteria to which this rule applies:
- SAML Attributes or Session Attributes
By default, the policy rule for SAML Attributes is set to Any SAML attribute. Keep this if you want to apply the rule action to any user (i.e., the rule applies to all users, groups, departments, etc.).
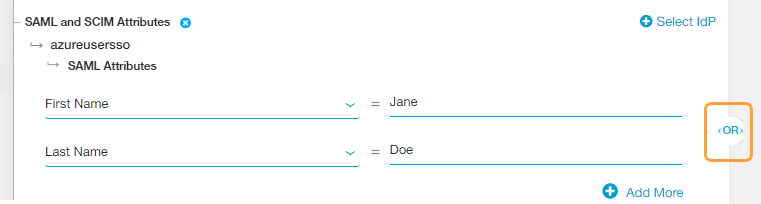
Alternatively, choose a specific SAML attribute from the drop-down menu if you want to apply the rule action to specific users, groups, departments, etc.:
- You can search for a specific attribute, select a listed attribute, or click Clear Selection to remove all selected attributes.
- After you make a selection, enter the SAML attribute value (i.e., the users to whom the rule applies) in the text field that appears.
- Click Add More to add multiple attributes, if necessary.
If you are subscribed to ZIdentity for users, the SAML Attributes option is replaced with Session Attributes. To learn more, What Is ZIdentity?
Close - SCIM Attributes or User Attributes
Choose a specific SCIM attribute from the drop-down menu to apply the rule action to specific users, groups, departments, etc:
- You can search for a specific attribute, select a listed attribute, or click Clear Selection to remove all selected attributes.
- After you make a selection, enter the SCIM attribute value (i.e., the users to whom the rule applies) in the text field that appears.
- Click Add More to add multiple attributes, if necessary.
If you are subscribed to ZIdentity for users, the SCIM Attributes option is replaced with User Attributes. To learn more, see What Is ZIdentity?
Close - SCIM Groups
Choose a specific SCIM group from the drop-down menu to apply the rule action to a specific group:
- You can search for a specific group, select a listed group, or click Clear Selection to remove all selected groups.
- Click Add More to add multiple groups, if necessary.
These criteria appear under SAML and SCIM Attributes > <IdP Name>, where <IdP Name> is name of the IdP configuration you selected in step a.
To process SAML and SCIM criteria in a rule, you must enable the SAML Attributes for Policy setting for SAML and the SCIM Attributes and Groups for Policy setting for SCIM when configuring an IdP. To learn more, see Configuring an IdP for Single Sign-On.
If you added multiple attributes or groups to the policy rule, then an OR Boolean operator is used between them by default. For example, if you selected FirstName and LastName, the policy rule is only applied to users with the specified FirstName OR LastName for that IdP. However, you can toggle this to an AND operator by clicking on it.
CloseIf the corresponding IdP setting (SAML Attributes for Policy) is disabled for SAML, but the policy rule has criteria for SAML attributes, then the rule is evaluated differently depending on the Boolean operator between the criteria:
- OR: The criteria evaluation is skipped for SAML attributes, but is continued for SCIM attributes and SCIM groups.
- AND: The policy rule is not evaluated. You must remove the criteria under SAML Attributes to process the policy rule.
If the corresponding IdP setting (SCIM Attributes and Groups for Policy) is disabled for SCIM, but the policy rule has criteria for SCIM attributes or SCIM groups, then the rule is evaluated differently depending on the Boolean operator between the criteria:
- OR: The criteria evaluation is skipped for SCIM attributes and SCIM groups, but is continued for SAML attributes.
- AND: The policy rule is evaluated. You must remove the criteria for SCIM attributes and SCIM groups to process the policy rule.
The Boolean logic used between Criteria is always displayed. For example, when a user requests access to an application, the policy rule is evaluated to check if an application segment OR its segment group are present AND whether any of the SAML attributes are applicable to the user making the request before it grants or denies access. You can always view the Rule Action and Criteria as well as the applied Boolean logic on the AppProtection Policy page.
- Click Save.