Experience Center
About Private App Microtenants
Contact Zscaler Support to enable this feature for your organization.
A Private App Microtenant is a delegated administrator responsibility that is assigned to an admin by an admin with Private App Microtenant administrator privileges. Private App Microtenants are defined by an authentication domain and assigned to admins based on country, department, and company for role-based administration control.
Private App Microtenants provide the following benefits and enable you to:
- Delegate the responsibilities of an admin.
- Manage the configuration of shared application segments, segment groups, servers, server groups, App Connectors, App Connector Groups, and policies exclusive to users within their country, department, and operating company.
- View the dashboard and logs exclusive to the users within their country, department, and operating company.
- Share application segments between different Private App Microtenants.
A Private App Microtenant is created within a tenant and is used when departments or subsidiaries within an organization want to manage their configurations independently. For example, an organization can delegate the responsibilities of admins directly to the acquired or merged company admins so that they can manage their configurations independently. In the following diagram, admin groups A and B are from USA and India. Both admin groups have access to different tenants but share the same global resources (e.g., applications, App Connectors, etc.). The Private App Microtenant admin assigns the different Private App Microtenants to both admin groups so each group gets their own Private App Microtenant in addition to still having access to the global resources.

Zscaler recommends you consider the following before configuring a Private App Microtenant:
- App Profile Configuration in the Zscaler Client Connector Portal
Admins that want to map machine tunnels to their respective Private App Microtenant must have a one-to-one mapping between an app profile and the individual Private App Microtenant. For example, a tenant has the following app profiles in the Zscaler Client Connector Portal:
Rule Number Policy Name User Groups Machine Token 1 Early_Adopters Beta_Grp None 2 China_Users PRC_Grp None 3 Default All Machine_Token_from_Default_Tenant The following Private App Microtenants are configured:
Private App Microtenant Number Name Authentication Domain 1 Private App Microtenant_for_US_Users us.com 2 Private App Microtenant_for_China_Users prc.com 3 Default All In this example, all machine tunnels enroll against the Default Private App Microtenant. This allows all users to access the Default Private App Microtenant resources over the machine tunnel.
Close
- Configurations That Are Read-Only for Custom Private App Microtenant Admins
- Authentication
- Certificate Management
- Disaster Recovery Management
- Log Streaming Service
- SCIM Management
- Source IP Anchoring
- User Portal
- Configurations That Can Only Be Managed or Configured by the Default Private App Microtenant Admin
- IdP Configuration
- Enrollment (CA) Certificates
- Log Streaming Service
- Private App Microtenants
- SAML Attributes
- Zscaler Client Connector Portal Links
Contact the Default Private App Microtenant admin if you need help configuring or managing certain features and use cases.
Close
- Disaster Recovery Configuration
The Private App Microtenants feature is not supported when disaster recovery is enabled. When Disaster Recovery Mode is activated, all users have access to all applications that are designated for disaster recovery. In the following diagram, user A and B are from USA and India and have access to separate applications when disaster recovery is disabled. After disaster recovery is enabled, both users have access to all applications that are designated for disaster recovery.

When in Disaster Recovery Mode, Private Service Edges and App Connectors mapped within a default or custom Private App Microtenant provide traffic to only applications designated for disaster recovery. To learn more, see Understanding Disaster Recovery.
Close
There can be situations where users from one Private App Microtenant need to access one or more application segments from another Private App Microtenant. Applications that are present in a Private App Microtenant can be shared with other Private App Microtenants. If an application is not shared with any other Private App Microtenant, it can be moved to the Default Private App Microtenant. To learn more, see Sharing Defined Application Segments and Moving Defined Application Segments.
About the Private App Microtenants Page
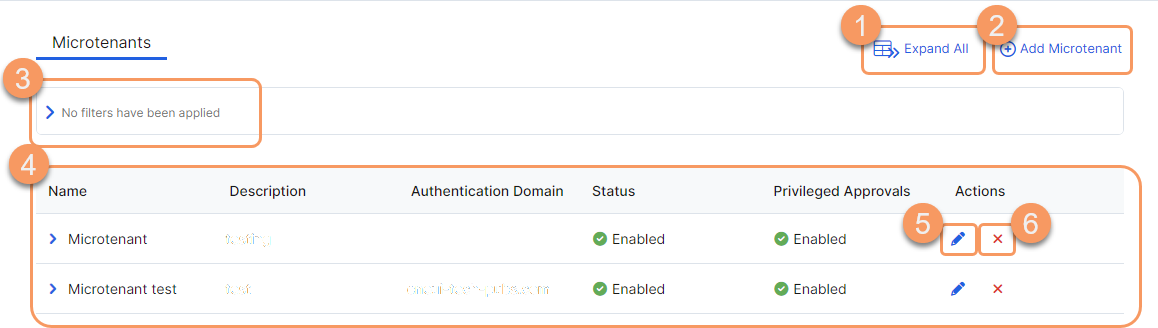
On the Private App Microtenants page (Administration > Role Based Access Control > Private App Microtenants), you can do the following:
- Expand all the rows in the table to see more information about each Private App Microtenant.
- Add a new Private App Microtenant.
- Filter the information that appears in the table. By default, no filters are applied.
- View a list of all Private App Microtenants. For each Private App Microtenant, you can see:
- Name: The name of the Private App Microtenant.
- Description: The description of the Private App Microtenant.
- Authentication Domain: The authentication domain used to authenticate the admins to the Private App Microtenant.
- Status: The status of the Private App Microtenant.
Privileged Approvals: The privileged approval for the Private App Microtenant. Enable to allow approval-based access even if no Authentication Domain is selected. The Emergency Access and Emergency Access Users pages are not visible for Private App Microtenants with Privileged Approvals disabled. This field is Disabled by default.
The Privileged Approvals option is only supported for applications that have Privileged Remote Access enabled. To learn more, see Configuring Defined Application Segments.
Users mapped to Private App Microtenants that are using Private Service Edges reauthenticate when the Private App Microtenant is disabled.
- Delete a Private App Microtenant.