Experience Center
About Posture Management Report
Zscaler Advanced SaaS Security Posture Management (SSPM) is a comprehensive and unified solution that delivers complete security across SaaS applications and platforms, from data visibility to posture and governance. It helps to quickly identify and mitigate risky misconfigurations, control SaaS sprawl and reduce third-party access, and identify users at risk.
- If you have Advanced Posture Management enabled via a license, the Posture Management page redirects to the 3rd-Party App Governance Admin Portal. You can access the 3rd-Party App Governance Admin Portal for detailed posture reports on supported SaaS applications. To learn more information about Advanced SSPM, see What is Advanced Posture Management and About Posture.
- If you don't have Advanced Posture Management enabled via a license, the Posture Management Page with an upgrade banner is visible. To upgrade to Advanced SSPM, contact your Zscaler Account team.
The Posture Management Report shows you the current state of your organization’s security posture for SaaS applications with respect to best practices recommended by Zscaler as well as based on industry standards such as GDPR, HIPAA, PCI, etc. It also allows you to see information on recommended security policies, security threats and their risk levels, and remediation activities. This serves as a starting point to decrease security risks for your organization’s SaaS applications.
To learn how to configure security policies as per the business requirements, see Understanding the SaaS Security Posture Management Policy.
The Posture Management Report provides the following benefits and enables you to:
- Gain visibility and monitor your organization's risk level by your SaaS application's security posture.
- Check your SaaS security posture against various security compliances.
- Analyze and help you remediate your organization's SaaS security posture from potential threats by configuring SaaS applications as per the recommended policies.
About the Posture Management Page
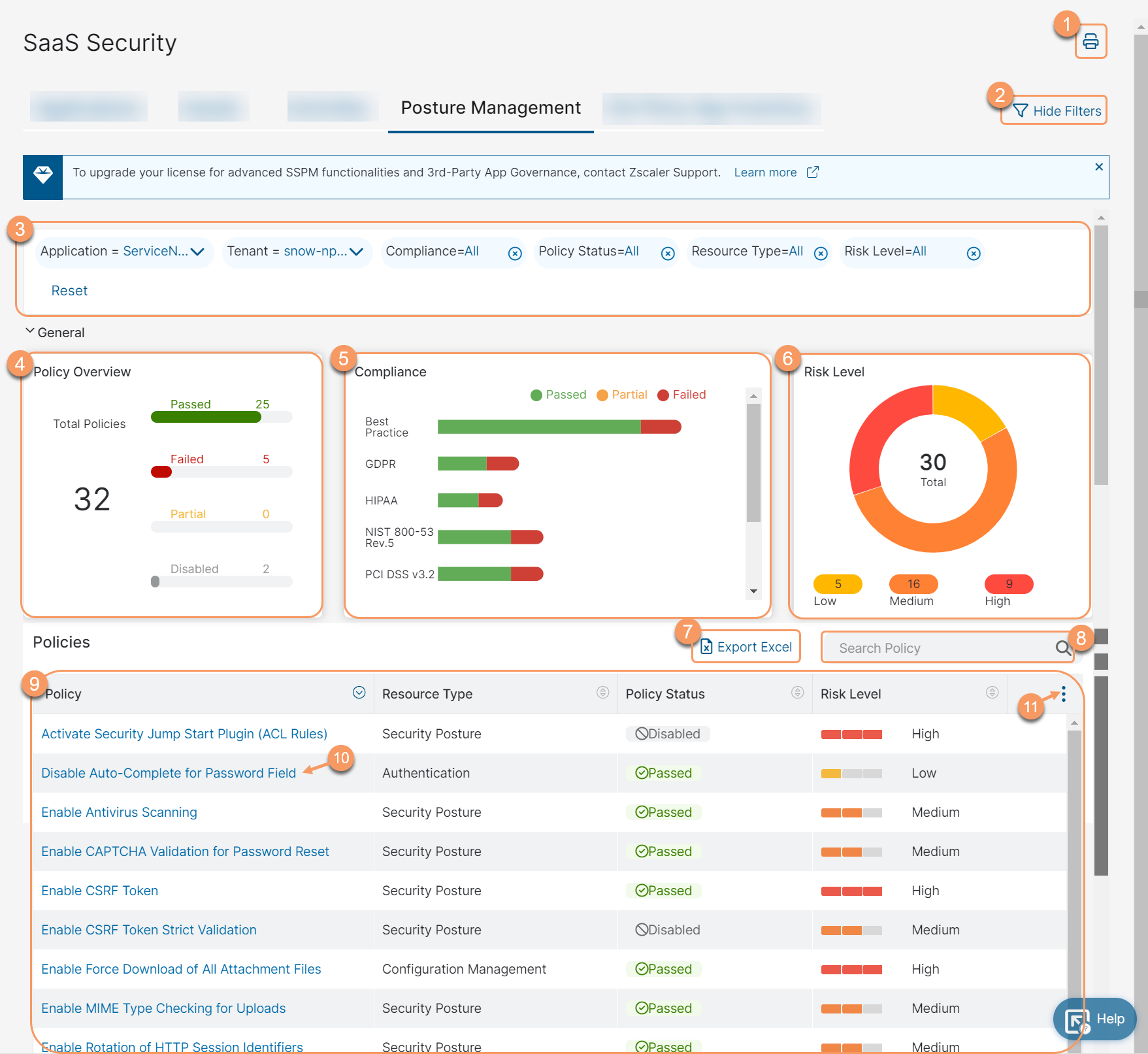
On the Posture Management page (Analytics > Internet & SaaS > Analytics > SaaS Security Report > Posture Management), you can do the following:
- Download the report to a PDF file.
- Show or hide the filter options.
Filter the report. You can show or hide the filter option from the top right. The following filters are available:
- Filters
- Application: View the policies for the application of your choice.
- Tenant: View the policies for the application tenant of your choice.
- Resource Type: View the policies for the resource types of your choice.
- Compliance: View the policies for the compliance of your choice. Irrespective of the compliance for which you want to filter the report, the Compliance widget in #5 lists all the compliances as policies can be applicable for multiple compliances.
- Policy Status: View policies by their status (All, Passed, Failed, Partial, or Disabled).
- Risk Level: View policies by their risk levels (All, High, Low, or Medium).
- Filters
Click Apply to update the page with your selections. You can click Reset at any time.
Policy Overview: View the total number of policies for the selected application and the policy status for each. The following statuses appear:
- Compliance: View the number of policies applicable for each compliance. Hover over the compliance bar to view the split between the passed, failed, and partially passed policies.
- Risk Level: View the pie chart for the total number of policies and their risk level (Low, Medium, or High). The pie chart does not show risk levels of disabled policies.
You can show or hide the preceding three sections together using the arrow next to General.
- Export the Policies table data to an Excel file. The Excel file shows the data as per the filters applied in #3.
- Search for a policy.
- Policies: View a list of all the policies. For each policy, you can view the following information:
- Resource Type: The resource type for the policy.
- Policy: The name of the policy. Click on the policy to view the description of the policy in the drawer view in #10.
- Policy Status: The status of the policy evaluation. The following statuses appear:
- Passed: Your organization's posture control scanned against the policy is correctly configured.
- Failed: Your organization's posture control scanned against the policy is incorrectly configured.
- Partial: Not all the assets scanned against the policy have posture control configured correctly. For example, your organization has 100 users and you enabled multi-factor authentication (MFA) for a subset of users.
- Disabled: The policy is not evaluated because it is disabled.
The Pending status in the Policy Status column appears until the first posture scan is complete when your organization is onboarded for SaaS Security Posture Control. This status can appear whenever a scan is in progress.
- Risk Level: The risk level if the policy is not implemented by your organization.
- Total Assets: The total number of assets that are scanned against the policy.
- Failed Assets: The number of failed assets to comply with the policy.
- Excluded Assets: The number of assets excluded from the SSPM report analysis.
- Partial Assets: The number of assets partially complying with the policy.
You can also search for a specific policy.
- Click on the policy to view detailed information about the policy overview, asset summary, and remediation steps in the drawer view.
- Drawer
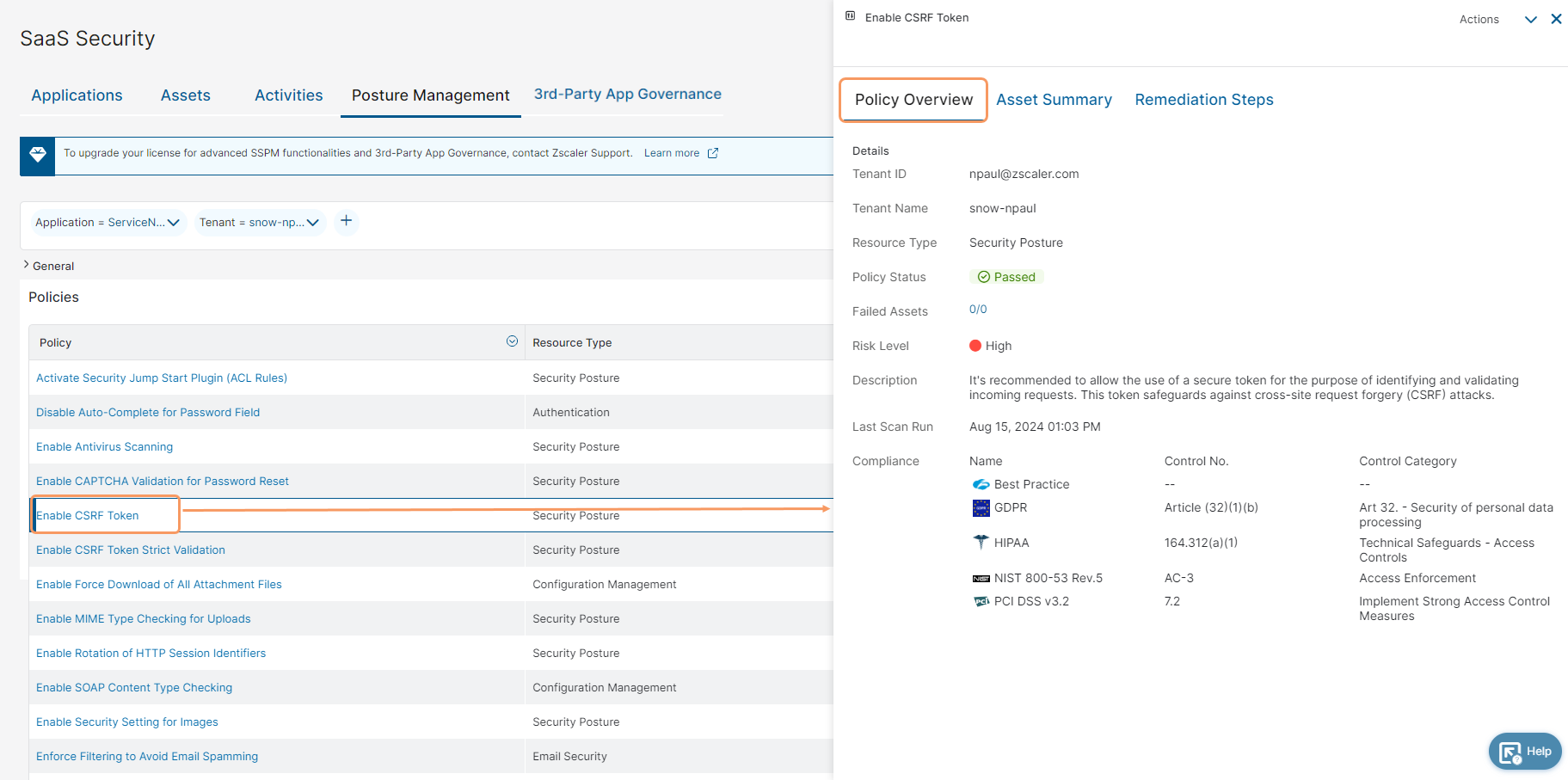
The Actions option is located at the top right of the drawer. You can use it to remediate (only available for select policies), enable, or disable a policy for SSPM analysis at the tenant level, or you can choose to export the information provided in the drawer to an Excel file. The drawer consists of the following three tabs:
- Policy Overview
The Policy Overview tab displays the following information:
- Tenant ID: The tenant ID.
- Tenant Name: The name of the tenant.
- Resource Type: The resource type the policy falls into.
- Policy Status: The policy implementation status (Passed, Failed, Partial, or Disabled).
- Failed Assets: The number of assets from total assets that have misconfigured attributes. Click on the asset number and you're redirected to the Assets Summary tab.
- Risk Level: The risk level if the policy is not implemented (High, Low, or Medium).
- Description: The description of the policy.
- Last Scan Run: The timestamp when the policy was last evaluated.
- Compliance: Displays the compliances the policy is mapped to.
- Asset Summary
The Asset Summary tab displays the following information:
- Description: The description informs why the policy failed or what was evaluated.
- Filter the Assets table by Status or State.
- Search for an asset by its name.
- View a list of all the assets. An asset can be a user or repository, depending on the type of application. For each asset, you can view the following information:
- Status: The policy status for the assets (Passed, Failed, or Partial).
- Repository Name: The name of the repository. This column is visible for source code repository applications.
- Repo ID: The repository ID. This column is visible for source code repository applications.
- Email ID: The email ID of the user. This column is not visible for source code repository applications.
- Display Name: The name of the user. This column is not visible for source code repository applications.
- Visibility: The repository visibility (Private, Public, etc.). This column is visible for source code repository applications.
State: The state of the asset. One of the following states appears:
- Excluded: The asset is excluded from the SSPM report analysis.
- Marked for Remediation: The asset is marked for remediation. When you remediate an asset, the remediation status is updated only after the next scan. Until then, the State column displays Marked for Remediation.
- Remediated: The asset is remediated.
- Remediation Failed: The remediation of the asset failed.
The column displays no information if no actions are performed.
- Action: The actions available for the asset.
- Modify the table and its columns.
- Action: You can perform the following actions on the asset:
- Exclude: Exclude the asset from the SSPM report analysis.
- Remediate: Remediate the asset to comply with the policy. This option is available for select policies.
- Click the dropdown to view the following information:
- General Info: The basic information about the asset.
State Log: The logs for the changes made to the asset. The logs are populated when you perform exclude, do not exclude, or remediate actions on the asset. For each log, you can view the following information:
- Timestamp
- Administrator
- Notes
You can also modify the table and its columns.
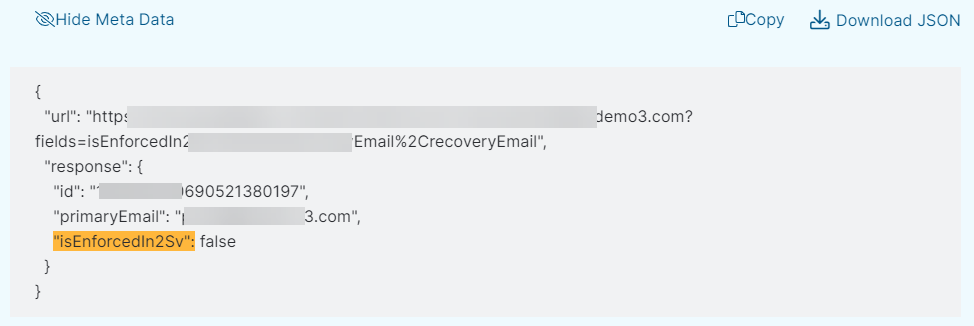
- View Metadata: Click to view the metadata highlighting the part where the configuration requires your attention to comply with the policy. You can copy the part that is displayed in the section or download the entire API response to a JSON file using the Copy or Download JSON option respectively. See image.
Close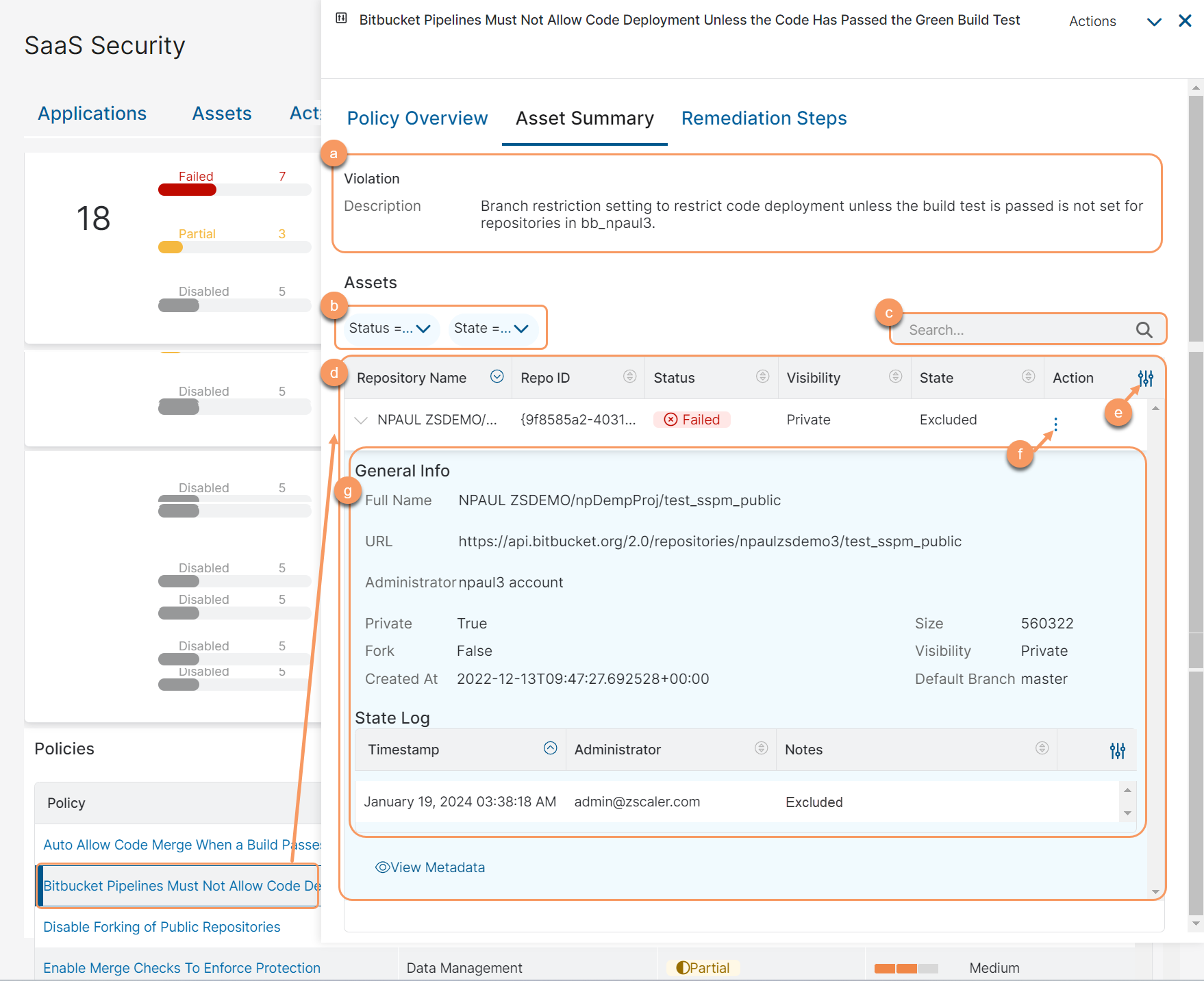
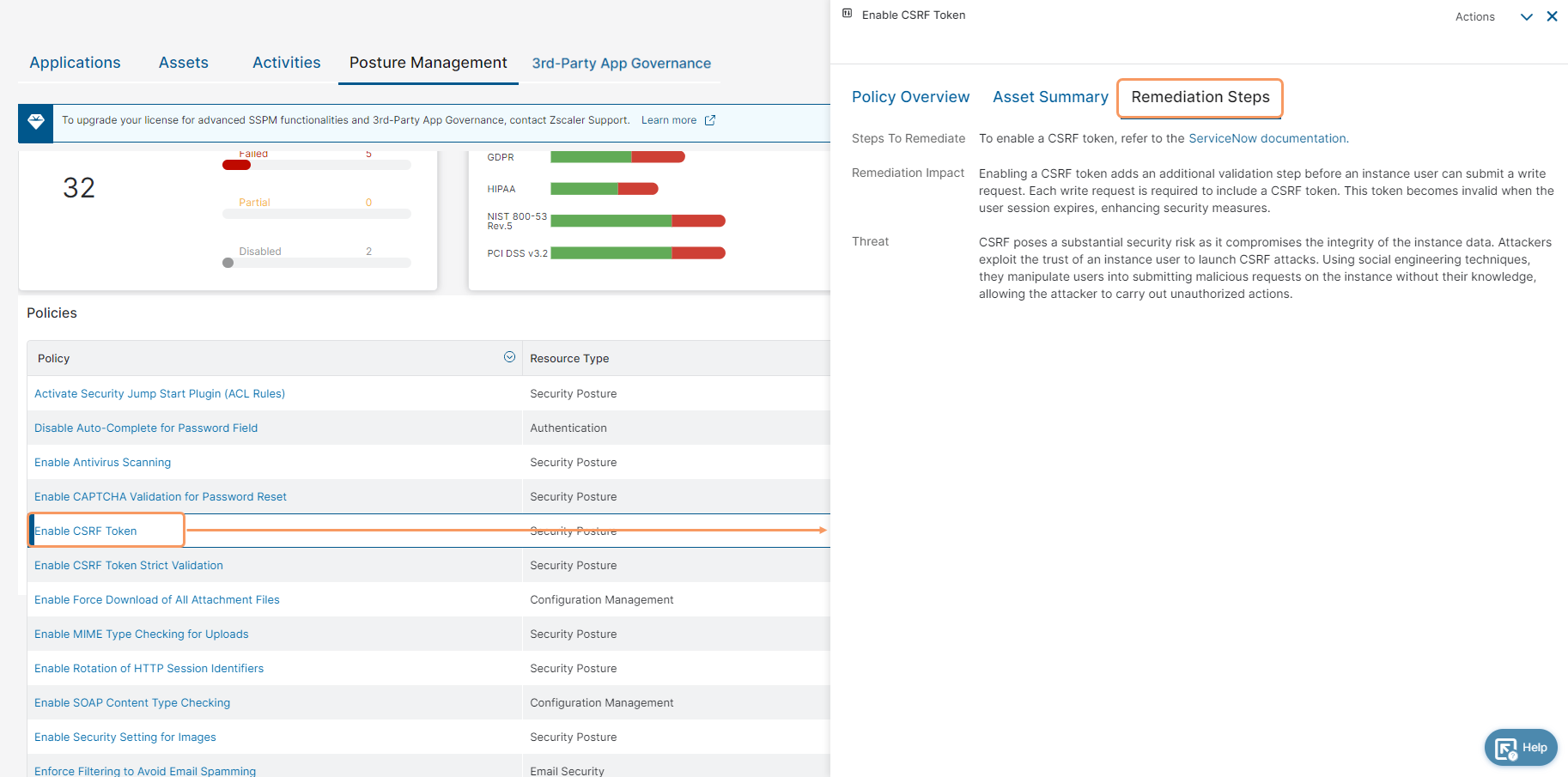
- Remediation Steps
The Remediation Steps tab displays the following information:
- Steps To Remediate: A link that redirects you to remediation steps in the application's help documentation.
- Remediation Impact: The information about how the user's experience changes if you remediate the misconfiguration.
- Threat: The information about potential security risks if the security posture is not configured as per the recommended policy.
- Policy Overview