Experience Center
About IPS Control
Zscaler's Intrusion Prevention System (IPS) uses signature-based detection to monitor and protect your network traffic from intrusion over all ports and protocols. Zscaler's IPS Control uses custom IPS signature rules built and updated by Zscaler's security research team, as well as signatures from industry-leading vendors. In addition to the signatures managed by Zscaler, you can create and deploy custom IPS signatures that are specific to your organization’s requirements. The Zscaler service monitors your traffic in real time using these signatures. As soon as the IPS has examined the contents of your traffic and found a pattern match, it can enforce your security policies inline.
IPS Control provides the following benefits and enables you to:
- Use signature-based detection to monitor your network traffic for malicious activities and prevent attacks by enforcing policies in real time.
- Define granular IPS Control rules using a number of conditions, such as users, groups, or departments, locations, threat categories, network services, source IP addresses, destination IP addresses/FQDNs, etc. Zscaler provides a default IPS rule that blocks all traffic. You can create granular policies of higher precedence (i.e., higher admin rank) than the default rule to explicitly allow specific traffic (e.g., IT Security group traffic matching threats) while blocking all other traffic via the default rule.
- Enforce condition-based actions on your network traffic, such as allowing or blocking traffic. You can also configure rules to allow specific types of traffic to bypass Zscaler's IPS.
- Enhance your security posture by employing custom IPS signatures built using the Snort syntax to identify specific threats.
- Leverage Zscaler Firewall logs to investigate and analyze threats detected in your network.
IPS Control enables you to defend your organization against threats from both web traffic and non-web traffic. This includes protection for HTTP, HTTPS, FTP, DNS, TCP, UDP, and IP-based ports and protocols. However, IPS Control based on custom IPS signature rules protects only non-web traffic. IPS Control also enables you to create granular rules for specific users, groups, departments, and so on.
You can enable IPS Control policies for specific locations by configuring the appropriate option for the location. To learn more, see Enabling the Firewall for Locations. If your organization uses Z-Tunnel 1.0 or PAC files to route traffic, ensure that the firewall is enabled for this type of traffic in the Advanced Settings. Threats detected in your network traffic are displayed under Firewall Insights > Logs. Threats detected in web-only traffic also appear on the Security Dashboard.
- IPS Control is available only with Advanced Firewall. For more information, see Understanding Firewall Capabilities. If you have Advanced Threat Protection and IPS Control, rules created for Advanced Threat Protection are evaluated first.
- Only traffic that transits the Internet & SaaS Private Service Edge or Internet & SaaS Virtual Service Edge can be inspected against custom IPS signature rules. To leverage custom IPS signature rules, your organization must have one of these Internet & SaaS Service Edge deployments.
About the IPS Control Page
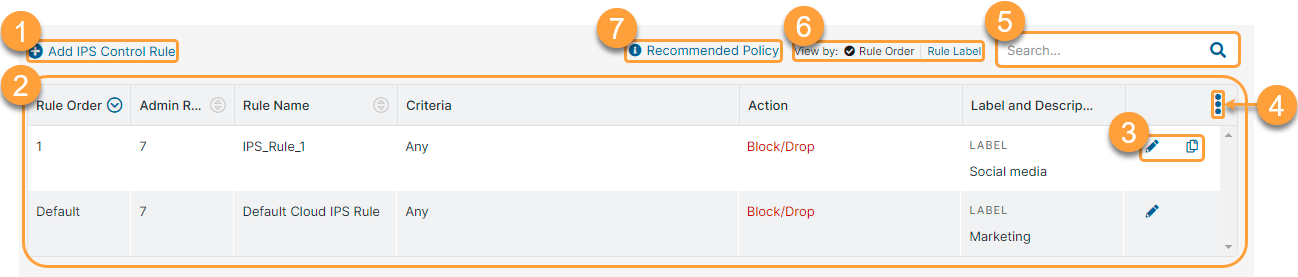
On the IPS Control page (Policies > Cybersecurity > Inline Security > IPS Control), you can do the following:
- Configure an IPS Control rule.
- View a list of all configured IPS Control rules. For each rule you can view the following information:
- Rule Order: The policy rule's order number. IPS Control policy rules are evaluated in ascending numerical order. You can sort this column.
- Admin Rank: The assigned admin rank for the rule. This is visible only if admin ranking is enabled in the Advanced Settings. You can sort this column.
- Rule Name: The name of this rule. You can sort this column.
- Criteria: A description of the different criteria that have been added to this rule.
- Action: The action configured for the policy rule.
- Label and Description: The label and description of the policy rule, if available.
- Edit, duplicate, or delete an IPS Control rule.
- Modify the table and its columns.
- Search for an IPS Control rule.
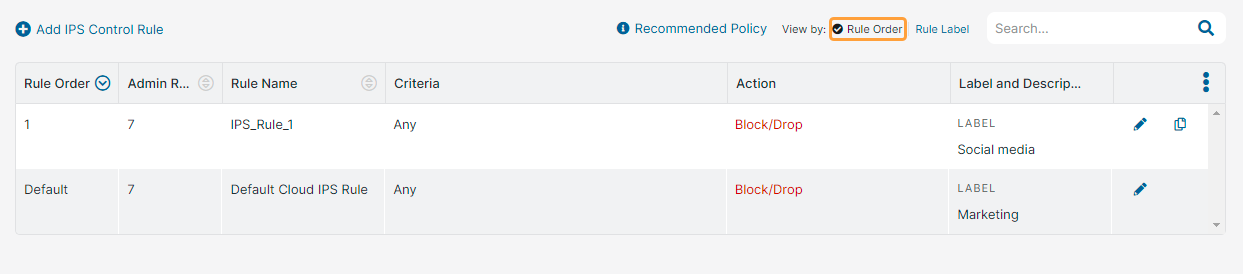
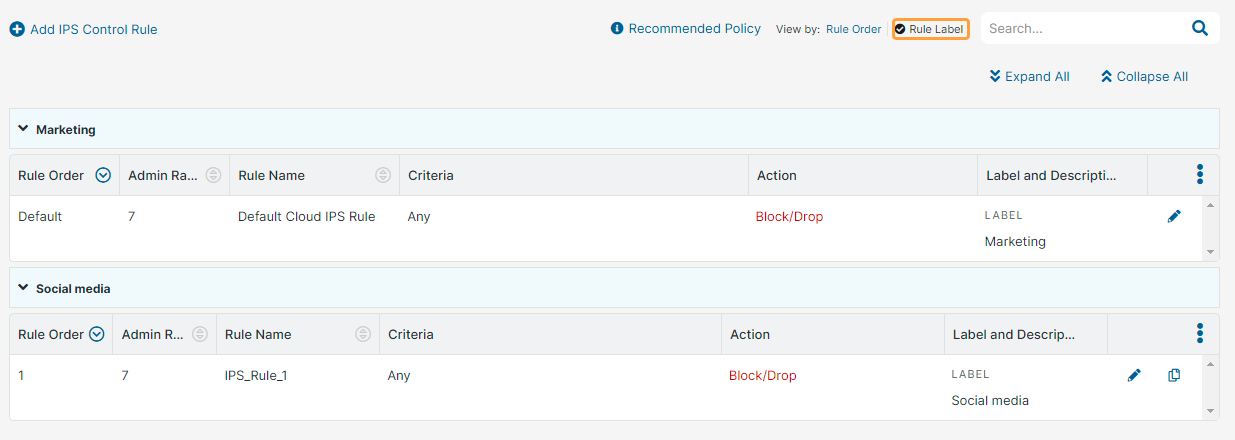
- Select one of the following View by options to see the IPS Control rules accordingly:
Rule Order: Displays the rules based on the rule order. By default, the rules are listed in the ascending rule order.
Rule Label: Displays the rules based on the rule labels. The rules are grouped under the associated rule labels.
You can expand or collapse all the rule labels using the Expand All or Collapse All buttons.
- View the recommended IPS Control policy.