Secure Private Access (ZPA)
SCIM Configuration Guide for Microsoft Azure AD
This guide provides information on how to set up Microsoft Azure Active Directory (AD) to use SCIM in Zscaler Private Access (ZPA). This configuration information is different from setting up Azure AD as an IdP for ZPA.
Zscaler and Microsoft are technology partners. To learn more about integrating Zscaler and Microsoft Azure AD, see the Zscaler and Microsoft Entra ID Passwordless Deployment Guide.
Prerequisites
Ensure that you have:
- A premium Azure AD subscription
- An existing directory in Azure AD
- A ZPA account with an administrator role that allows you to add a SCIM Configuration
Configuring SCIM for Identity Management
Using SCIM allows you to quickly remove users from the ZPA when you delete them in your user directory. To use SCIM, you must configure it in Azure AD.
The following procedure applies to SCIM configurations for ZPA in Azure AD. You need to begin the SCIM configuration process in the ZPA Admin Portal to get the required information in steps 5 and 6.
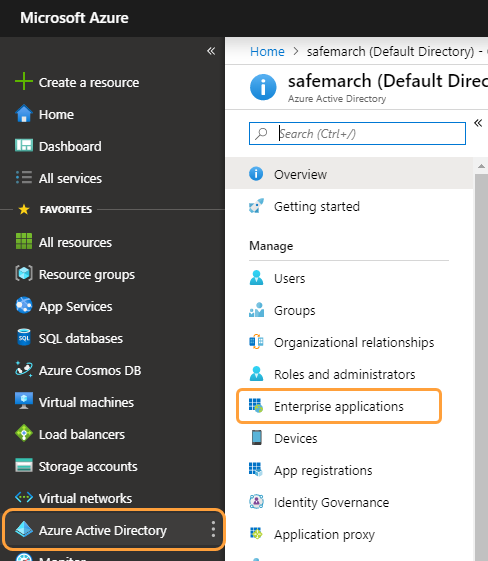
- Log in to the Azure portal and go to Azure Active Directory > Enterprise applications in the left-side navigation.
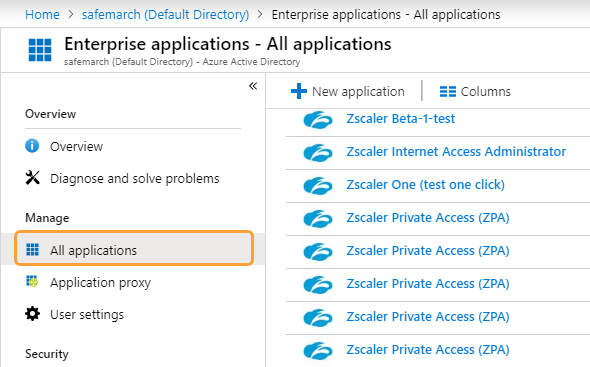
See image. - Click All applications, then click the Zscaler Private Access (ZPA) application you added (in steps 1 to 4) as part of configuring Azure as an IdP. To learn more, see Configuration Guide for Microsoft Azure AD.
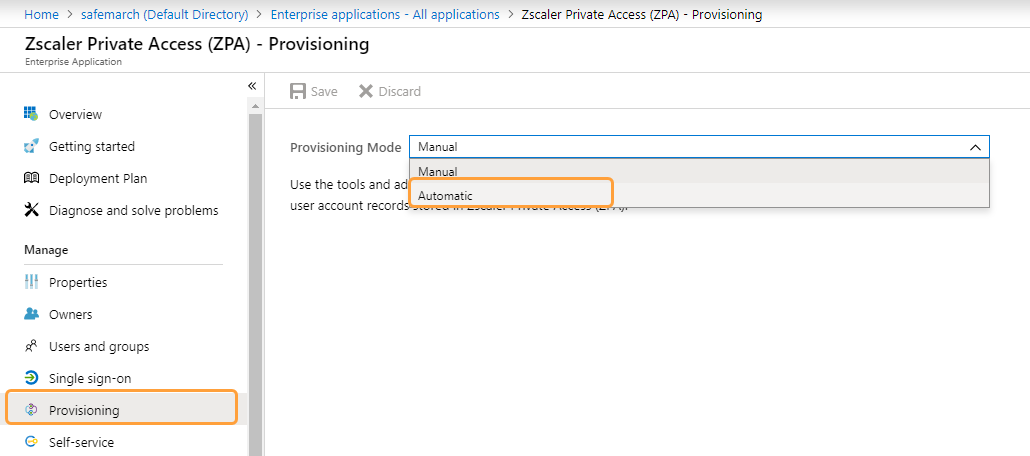
See image. - Click Provisioning in the left-side navigation.
- Select Automatic from the Provisioning Mode drop-down menu.
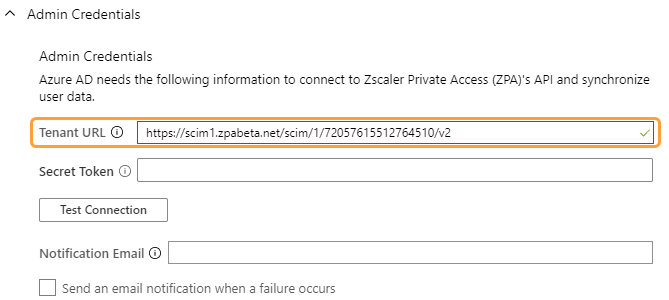
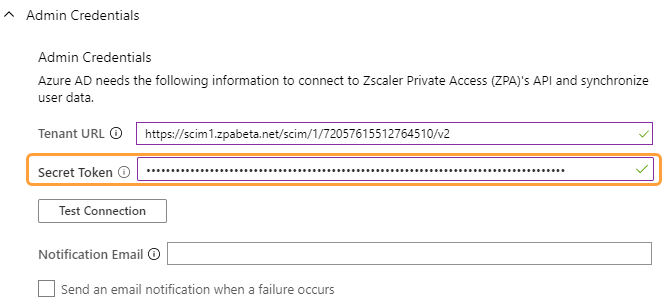
See image. - In the Tenant URL field, enter the SCIM Service Provider Endpoint that is provided when enabling SCIM in the ZPA Admin Portal.
See image. - In the Secret Token field, enter the Bearer Token that is provided when enabling SCIM in the ZPA Admin Portal.
See image. - Click Test Connection. The Azure Active Directory attempts to connect to the SCIM endpoint. When the connection is successful, a verification message appears.
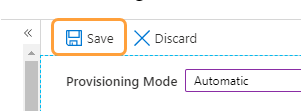
If the attempt fails, error information is displayed. Resolve any errors before moving forward. - Click Save after a successful connection to save your credentials.
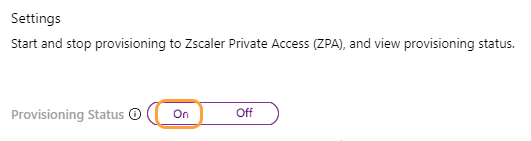
See image. - Set the Provisioning Status to On.
See image. - Set the Scope to Sync only assigned users and groups.
- Click Save again to start the Azure AD provisioning service.
After SCIM is enabled, Zscaler checks if a user is present in the SCIM database. Based on this information, Zscaler decides if the user is allowed or blocked access to ZPA. Customers need to ensure SCIM user sync is complete prior to enabling SCIM policies for these users, otherwise the ZPA service does not recognize the users and evaluate policies for them. After SCIM Sync is enabled, Zscaler recommends waiting a minimum of 48 hours, or up to a week, before enabling SCIM policies. It can take up to several days for the IdP to completely sync all user information to ZPA. Zscaler recommends that SCIM Sync be enabled in advance, prior to enabling SCIM Attributes for Policy. To learn more, see Enabling SCIM for Identity Management.