ITDR
Understanding the Zscaler ITDR Dashboard
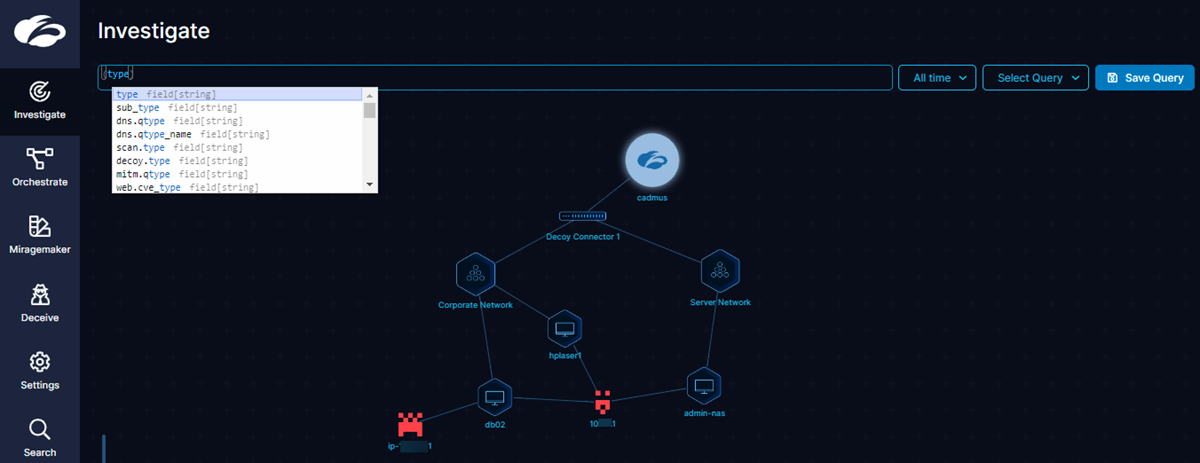
The Zscaler ITDR dashboard (Investigate page) is an interactive and graphical representation of real-time alerts that are the primary indicators of attacker activities.
When an attacker interacts with the decoys, ITDR detects threats, collects information on the attacker's actions and intentions, and generates high-fidelity and real-time alerts on the dashboard.

Viewing and Filtering Graphical Alerts
ITDR detects threats and generates alerts. These alerts represent attacker activities and appear in a graphical format on the dashboard. The graph is interactive and has ITDR elements. Each element represents a ITDR object or an attacker, depicted as icons.
The alert graph has the following elements depicted as icons:
- Zscaler ITDR Admin Portal: A single point of configuration and management for the entire ITDR solution.
- Decoy Connector: Lightweight virtual machines (VMs) that host network decoys. They also act as a network broker to connect the ITDR service to on-premises systems and Active Directory (AD) decoys in your environment.
- Decoy Group: Logically organized networks and Threat Intelligence (TI) decoys based on function, location, system type, etc.
- Decoy: A trap to divert attackers. Decoys look like real assets. The moment the adversary interacts with a decoy, it detects the threat and relays all the information to the ITDR Admin Portal. Each type of decoy is represented by a unique icon. The icon in the following image depicts a network decoy.
- Attacker: When an attacker interacts with the decoys, it is depicted by either a unique identicon or, in the case of TI activity, a country's flag, if available. Icons make it easier to distinguish and visually identify attackers without the need to remember complex IP addresses or hostnames.
You can click an icon on the graph to view the details pane that shows all the attacker activities on the system.
- Filtering Alerts By Time
You can filter alerts over a period of time between the last 10 minutes and all time.
By default, the dashboard displays information for alerts that occurred in the last 7 days.
To filter alerts by time frame:
On the Investigate page, click the Time Selector drop-down menu, and select a time period (e.g., Last 30 days).
To select a custom time frame, provide a Start and End date in years, months, days, hours, and minutes.
- Filtering Alerts Using Queries
You can apply filters using queries to focus on specific alerts. You can use the built-in queries or the query builder to create queries to filter alerts.
Close- Filtering Alerts Using Saved Queries
ITDR provides a list of saved queries to quickly filter certain types of alerts.
On the Investigate page, select a saved query from the Select Query drop-down menu. For example, select Severity-High to filter only high-severity alerts.
Close - Filtering Alerts Using the Query Builder
The query builder helps you to construct and modify queries. You can select the built-in syntax to create simple and advanced query expressions and save them for future use.
Close- Creating a Simple Query
Simple queries have just one parameter. To build a query to filter attacks from a particular IP address:
- On the Investigate page, click the query builder.
Enter
attacker.ip.As you continue to type, the query builder lists the built-in syntax that matches your query.
Select attacker.ip from the drop-down menu and add
is "192.0.2.0"to the query.Alerts from the specified attacker's IP address are filtered and displayed on the dashboard.
You can use various supported fields, parameters, operators, and regular expressions to build queries depending on your requirements. To learn how to build queries, see Understanding and Building Queries.
When using regular expressions to build Dashboard filter queries, make sure that appropriate letter casing is used in the expressions as the Dashboard filter does not support case-agnostic expressions nor the case-insensitivity flag (
Close\I). - Creating an Advanced Query
Advanced queries are complex queries with Boolean logic statements. To filter alerts that match one or more criteria:
- On the Investigate page, click the query builder.
Enter
(type).As you type, the query builder lists the built-in syntax that matches your query syntax.
Select the required built-in syntax from the list and create the advanced query:
(type is "windows") or (type is "network" and sub_type is "file")Alerts that match one of the criteria of the query are filtered and displayed on the dashboard.
You can use various supported fields, parameters, operators, and regular expressions to build queries depending on your requirements. To learn how to build queries, see Understanding and Building Queries.
When using regular expressions to build Dashboard filter queries, make sure that appropriate letter casing is used in the expressions as the Dashboard filter does not support case-agnostic expressions nor the case-insensitivity flag (
Close\I). - Saving a Query
You can create queries and save them for future use.
To save a query:
- On the Investigate page, create a simple query or an advanced query.
- (Optional) Select a time frame from the time selector drop-down menu (e.g., Last 30 days).
Click Save Query.
In the Save Query window:
- Name: Enter the name of the query.
- Include time period: (Optional) Enable if you want the query to record the selected time period and restore the time period settings when the query is selected in the future.
Click Save query.
The query is saved and is listed in the Select Query drop-down menu.
Click the Delete icon to delete the query that you have saved.
- Creating a Simple Query
- Filtering Alerts Using Saved Queries
Using the Chronology Slider
The chronology slider shows you a graph of attack volume by time. After you filter alerts by time frame, you can drag the controls at both ends of the chronology slider to select a subset of time from your main filter.
For example, if you have filtered alerts for the last 30 days, you can drag the controls at both ends of the chronology slider to trim the timeline to the first 10 days. Click the Apply Current Range (![]() ) button to apply the time range and view the alert graph for the subset of time.
) button to apply the time range and view the alert graph for the subset of time.
Click the Start Replay (![]() ) button to replay the registered alerts in the sequence they occurred. This helps you to analyze the chronology of when the attacks played out.
) button to replay the registered alerts in the sequence they occurred. This helps you to analyze the chronology of when the attacks played out.
Customizing the Dashboard
You can use the display controls on the dashboard to customize the alert graph display.
- Zoom Slider: Zooms in and out of the alert graph.
- Fit to Screen: Makes the elements of the alert graph fit to screen resolution so that all the graph elements are visible.
- Rearrange Elements: Rearranges the elements of the alert graph to their original position, if they are scattered over the screen.
- Lock Elements: Locks all the elements of the alert graph on the screen so that other elements do not move if you move one element.
- Full-Screen Toggle: Toggles to full-screen mode.
- Customizing the Dashboard Using Additional Filters
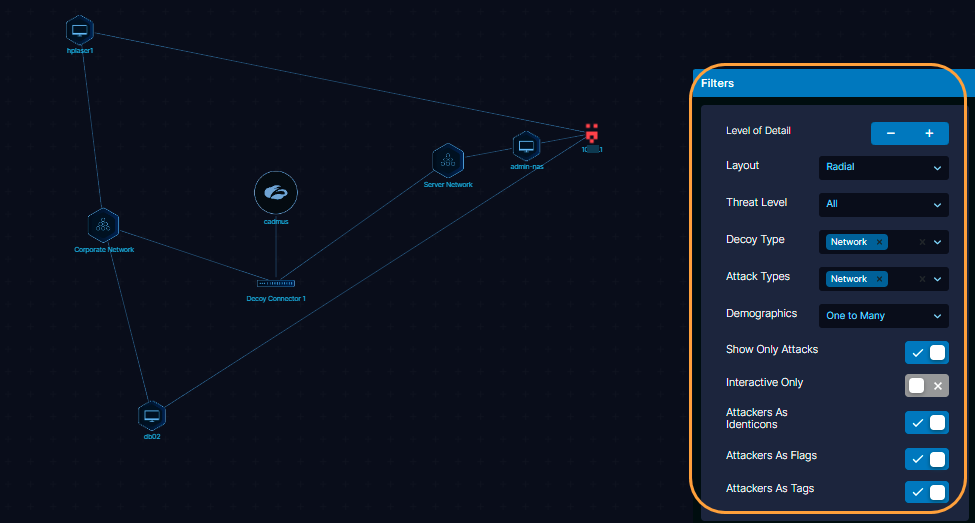
You can customize the dashboard using additional filters. The filters allow you to select the alert graph layout, level of detail of the alert graph, filter type of attacks, etc.
To customize the dashboard using filters:
On the Investigate page, click the filter icon in the bottom right corner of the dashboard.
In the Filters window:
- Level of Detail: Allows you to reduce or increase the level of element or object details on the alert graph. The first level is the ITDR Admin Portal, followed by Decoy Connectors, Decoy Groups, and Decoys. Click the minus (-) icon to reduce the number of elements on the graph and view basic details of the attack. Click the plus (+) icon to increase the number of elements on the graph and view the in-depth details of the attack. The number on the filter icon shows the current level of detail.
- Layout: Select a layout for the alert graph from the drop-down menu:
- Default
- Hierarchy (Tree layout)
- Radial (Circular layout)
- Threat Level: Select a threat level from the drop-down menu to filter alerts based on the threat severity:
- All
- Medium and Higher
- Only High
- Decoy Type: Select a decoy type from the drop-down menu to filter alerts for the specified decoy type (Landmine, Network, TI, etc.).
- Attack Types: Select an attack type from the drop-down menu to filter alerts for the specified attack type (Network, MITM, etc.).
- Demographics: Select a demographic level to filter the alerts based on the interaction between the attacker and the ITDR objects. The options are:
- All
- One to Many
- Many to One
- One to One
- Show Only Attacks: Enable to show only those objects on the alert chart that are attacked.
- Interactive Only: Enable to show attacks only when there is an interaction between the adversaries and the decoys. For example, if Interactive Only is enabled, attacks like network scans are not shown.
- Attackers as Identicons: Enable to show attacker icons as identicons. Disable to show a generic attacker icon instead of a unique identicon for each attacker.
- Attackers as Flags: Enable to show threat intelligence attack icons as country flags, if available.
- Attackers as Tags: Enable to show attacker icons as tagged names. You can tag an attacker icon with an alternate text for your reference. If Attackers as Tags is enabled, the attacker icons are shown with tagged names.