Posture Control (DSPM)
Adding Account Details and Deploying Templates
After deploying the orchestrator template, add the target accounts that must be monitored and deploy the monitoring and CloudTrail templates that include policies and permissions providing DSPM with read-only access to the target accounts.
To add account details and deploy templates:
- On the Overview page, go to Manage > Add Account.
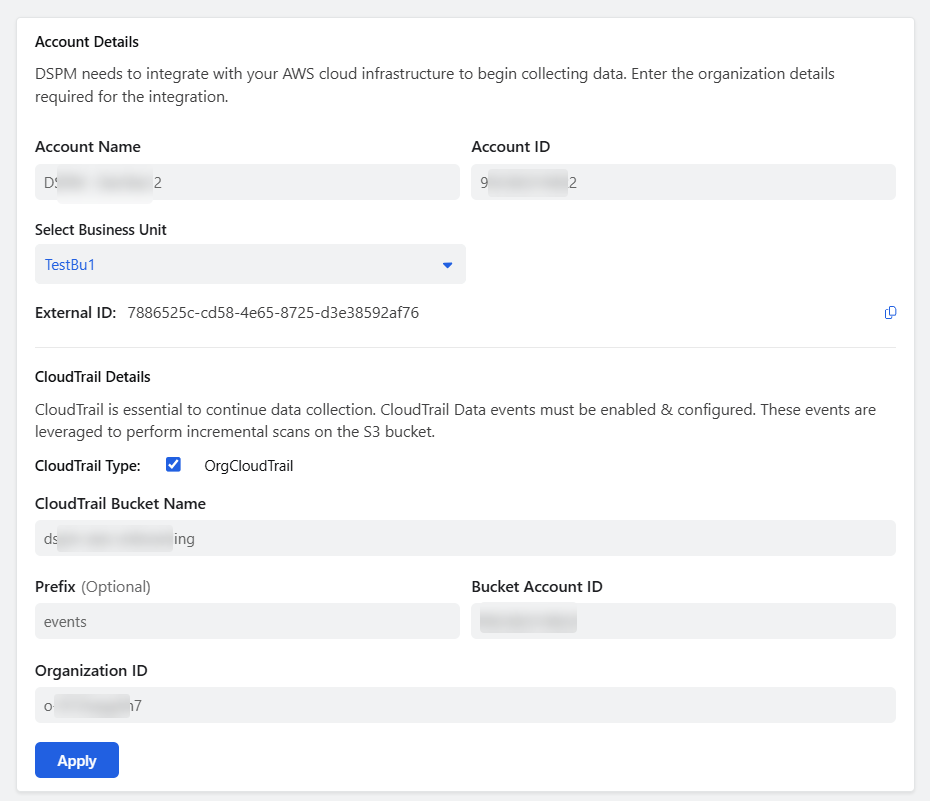
In the Account Details window:
- Under Account Details:
- Account Name: Enter the AWS account name that must be monitored.
- Account ID: Enter the 12-digit AWS account ID.
- Select Business Unit: A default business unit is assigned. Select another business unit, if required.
- Under CloudTrail Details, enter the S3 bucket details where the CloudTrail events are logged.
- CloudTrail Type: Select the OrgCloudTrail checkbox, if it is an organization CloudTrail.
- CloudTrail Bucket Name: Enter the S3 bucket name.
- Prefix (Optional): Enter the prefix, if any.
- Bucket Account ID: Enter the 12-digit AWS account ID.
- Organization ID: Enter the AWS organization ID.
- Click Apply.
- Under Account Details:
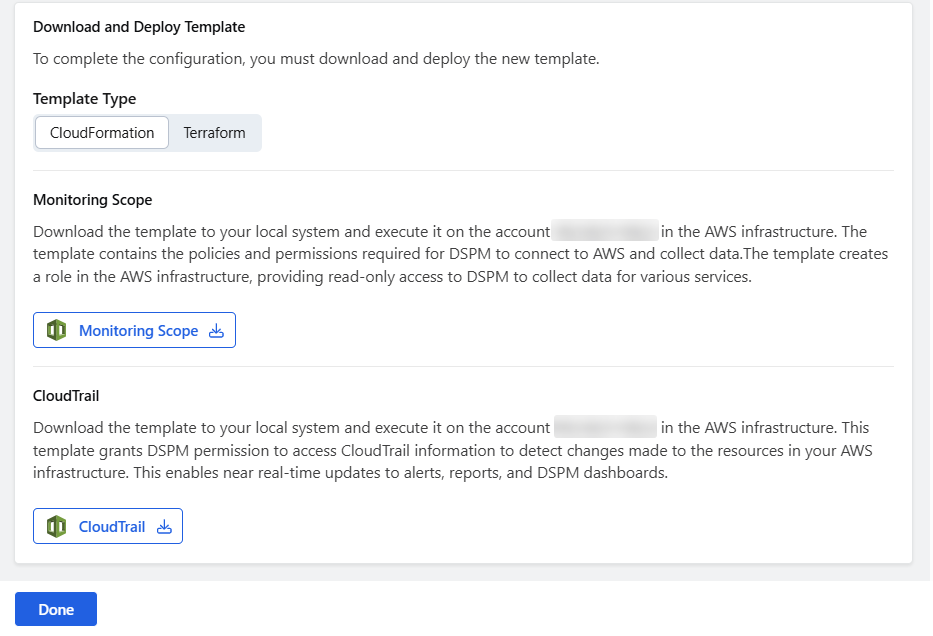
Under Download and Deploy Template, select the template type (CloudFormation or Terraform) and deploy the following templates:
- Monitoring Scope
- To deploy CloudFormation template
- a. Download the monitoring scope template.
Click Monitoring Scope to download the template as a ZIP file and extract it to your local system. The ZIP file includes:
Close - b. Create StackSets in the AWS Management Console.
- Sign in to the target account and go to CloudFormation.
- In the left-side navigation, select StackSets.
- Click Create StackSet.
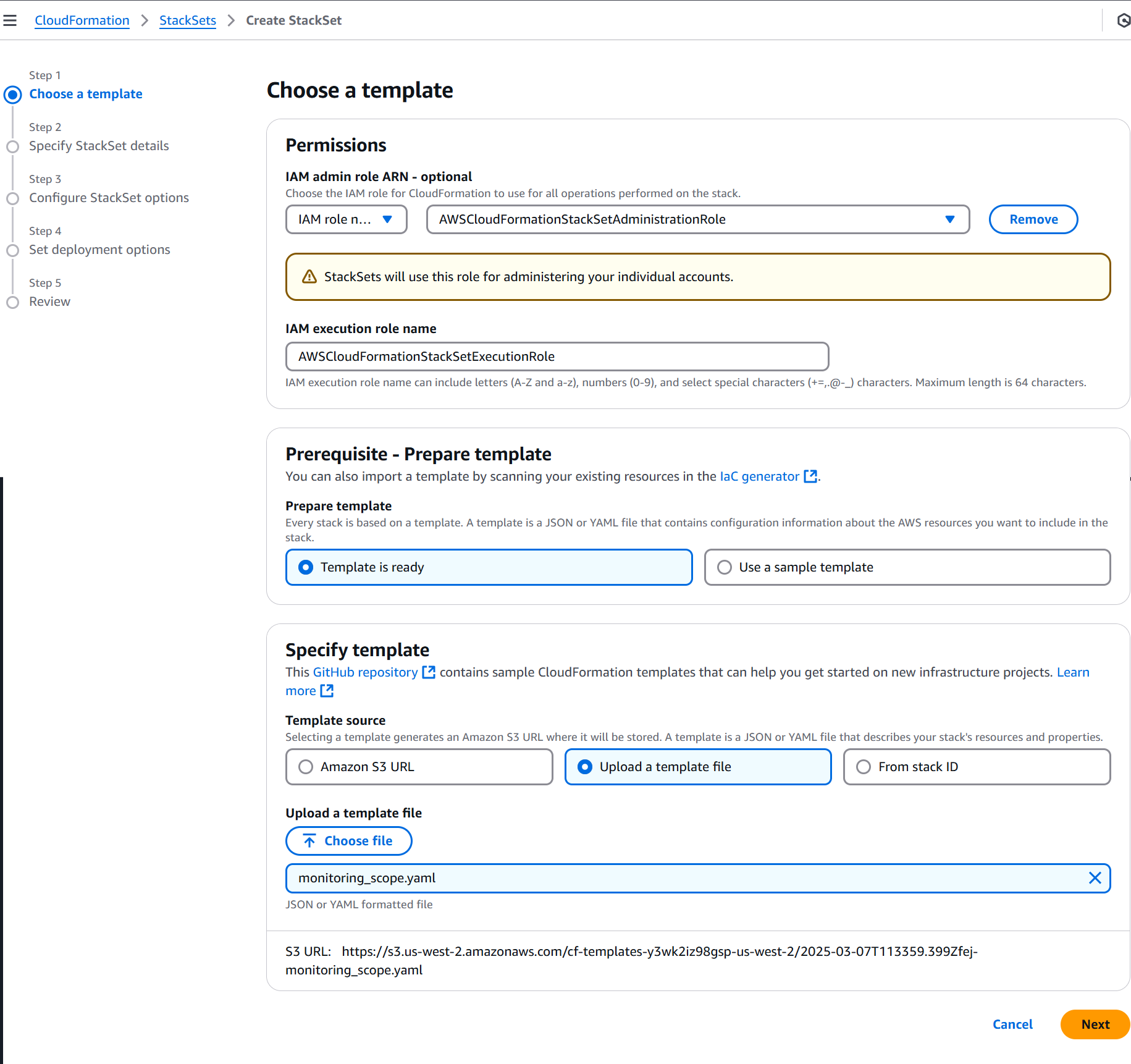
On the Choose a template page:
- Permissions: Select Service managed permissions.
- Prerequisite - Prepare template: Select Template is ready.
- Specify template: Select Upload a template file and click Choose file. Browse to the location where the downloaded ZIP file is extracted, select the YAML file, and then click Open.
- Click Next.
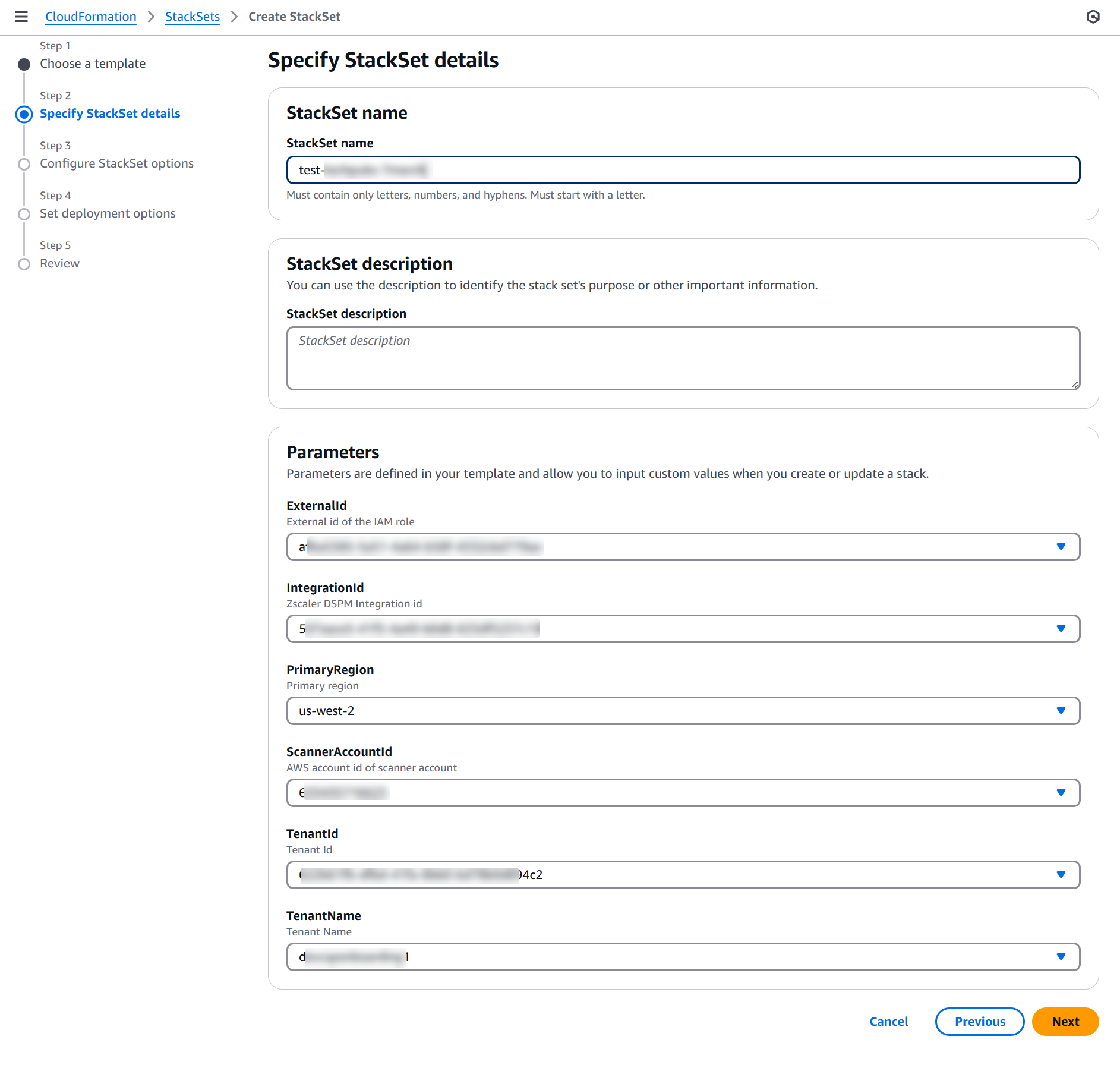
On the Specify StackSet Details page:
- StackSet name: Enter a unique and friendly name for the StackSet.
- Verify the parameters that are auto-populated.
- Click Next.
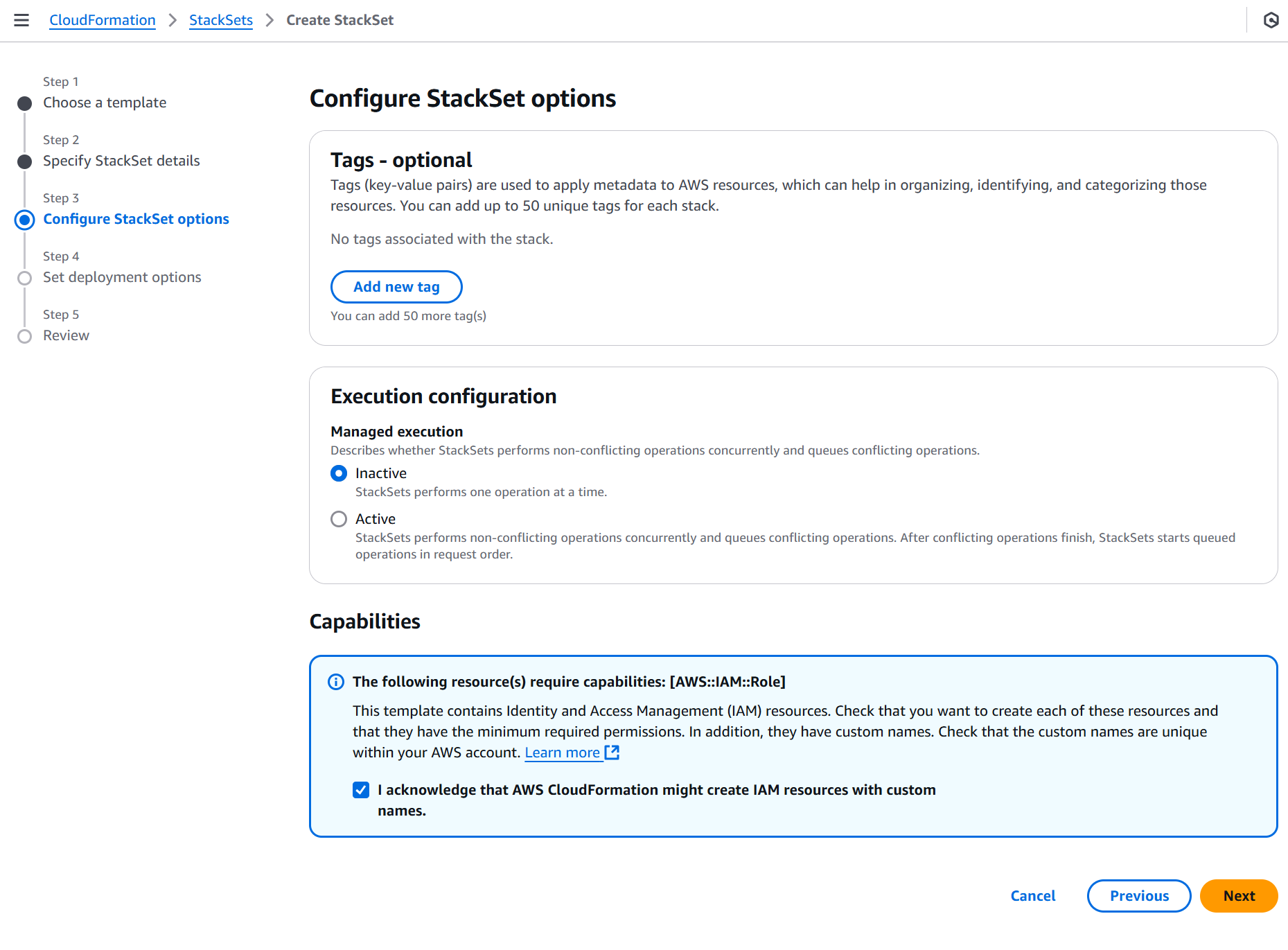
On the Configure StackSet options page, select the I acknowledge checkbox for AWS CloudFormation to create IAM resources with custom names and click Next.
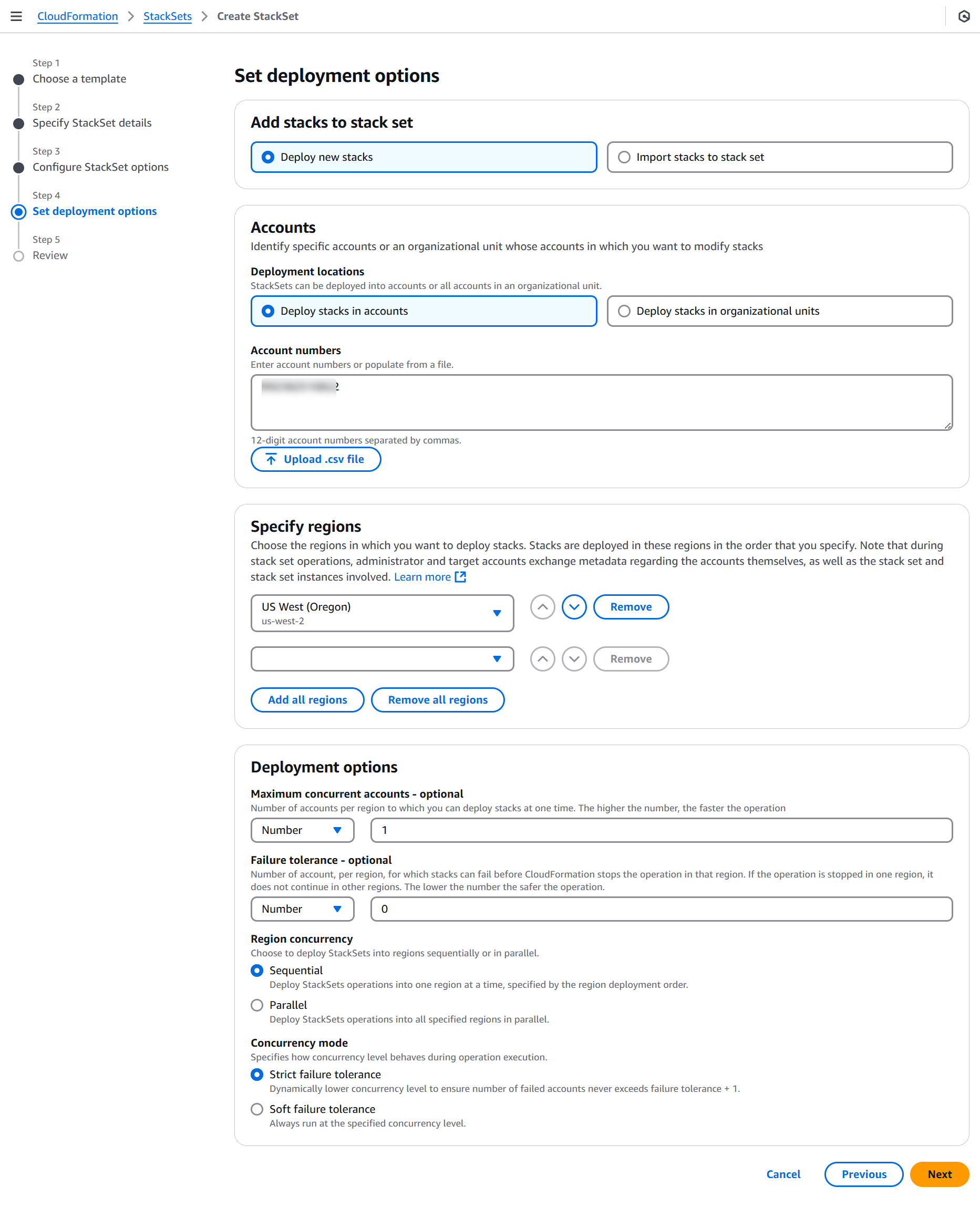
On the Set deployment options page:
- Add stacks to stack set: Select Deploy new stacks.
- Deployment targets: Select Deploy to organization.
- Auto-deployment options:
- Automatic deployment: Select Activated to automatically deploy additional stack instances for any new account added to the OU in the future.
- Account removal behavior: Select Delete stacks to remove stack instances if an account is removed from the OU.
- Specify regions: Select the regions in which the data stores must be scanned.
- Region concurrency: Select Sequential to deploy the StackSets in a sequential order.
- Click Next.
On the Review page, review the StackSet details and click Submit.
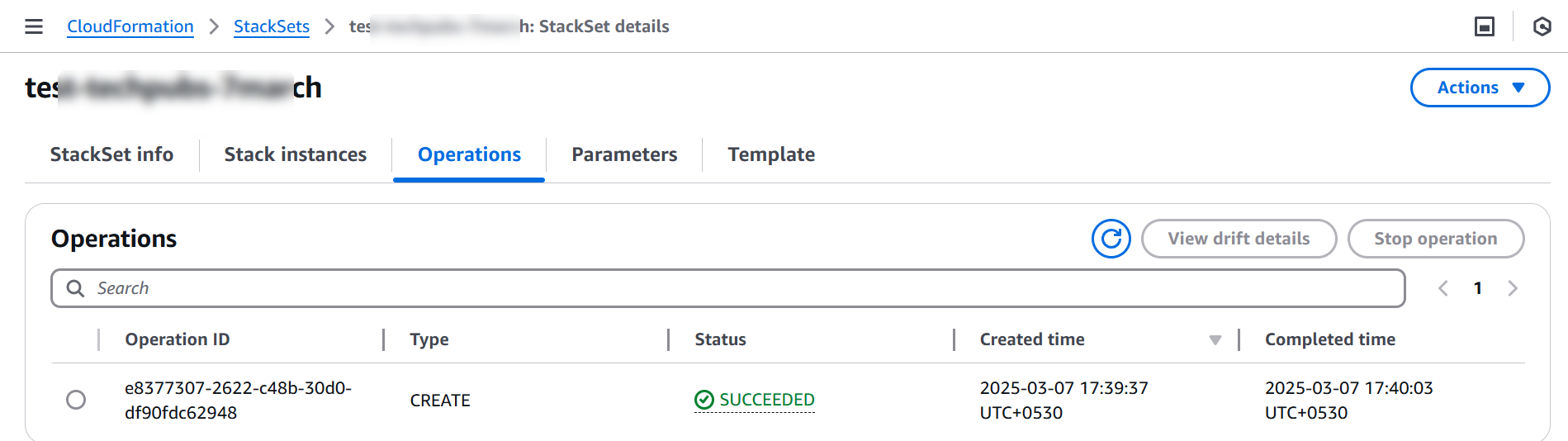
On the Operations tab, you can view the status of the StackSet deployment.
- a. Download the monitoring scope template.
- To deploy Terraform template
- a. Download the monitoring scope template.
Click Monitoring Scope to download the template as a ZIP file and extract it to your local system. The ZIP file includes:
- A CSV file with the target account details.
- Multiple Terraform files with policies and permissions.
- A README file with instructions for running the template.
- b. Update and deploy the Terraform files.
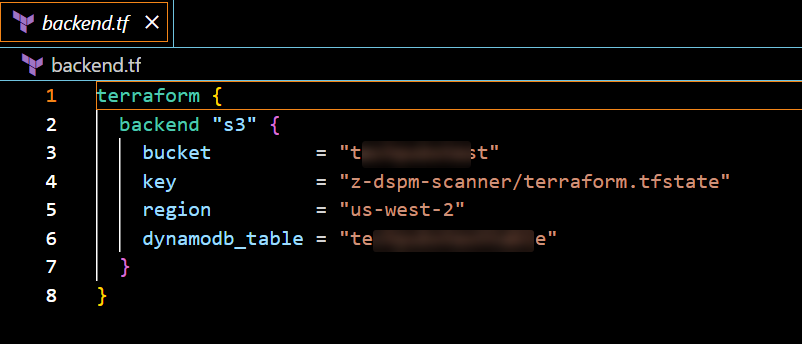
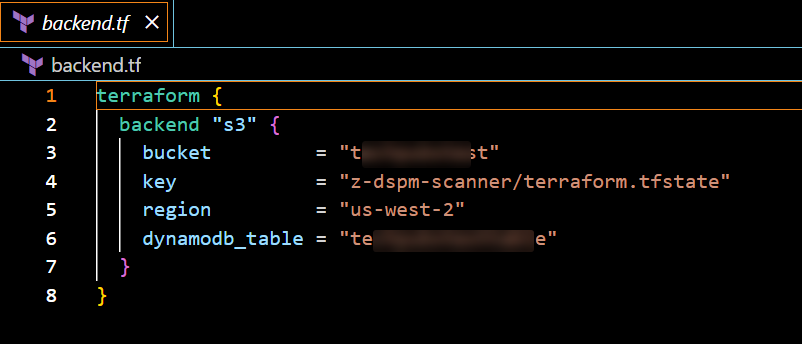
Update the
backend.tffile with the name of the storage services where you want to store the Terraform state files. For example:- bucket: Enter the name of the S3 bucket.
- region: Enter the primary region of the target account.
- dynamoDB_table: Enter the name of the dynamoDB table in the primary region of the target account.
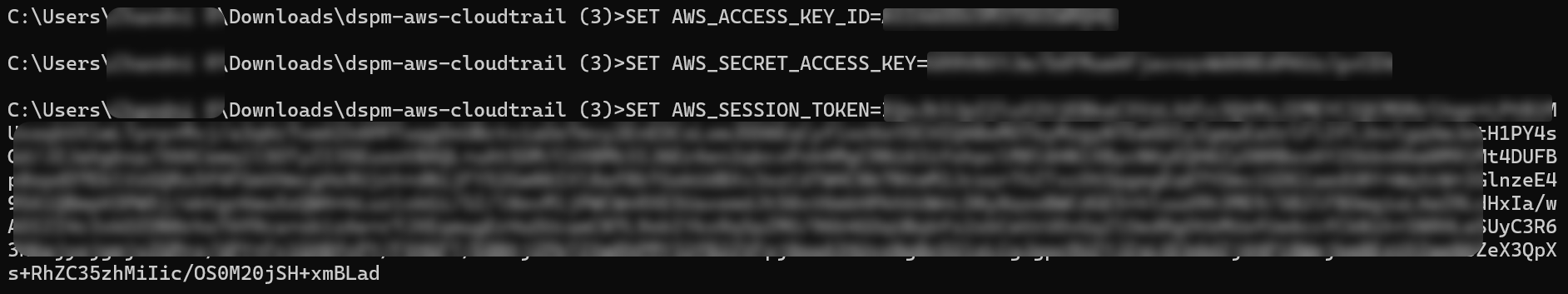
- Open the Command Prompt or any other CLI app in your local system.
- Switch to the directory containing the downloaded Terraform files.
- Copy and paste the access keys of the target account and press
Enter. - Run the following commands:
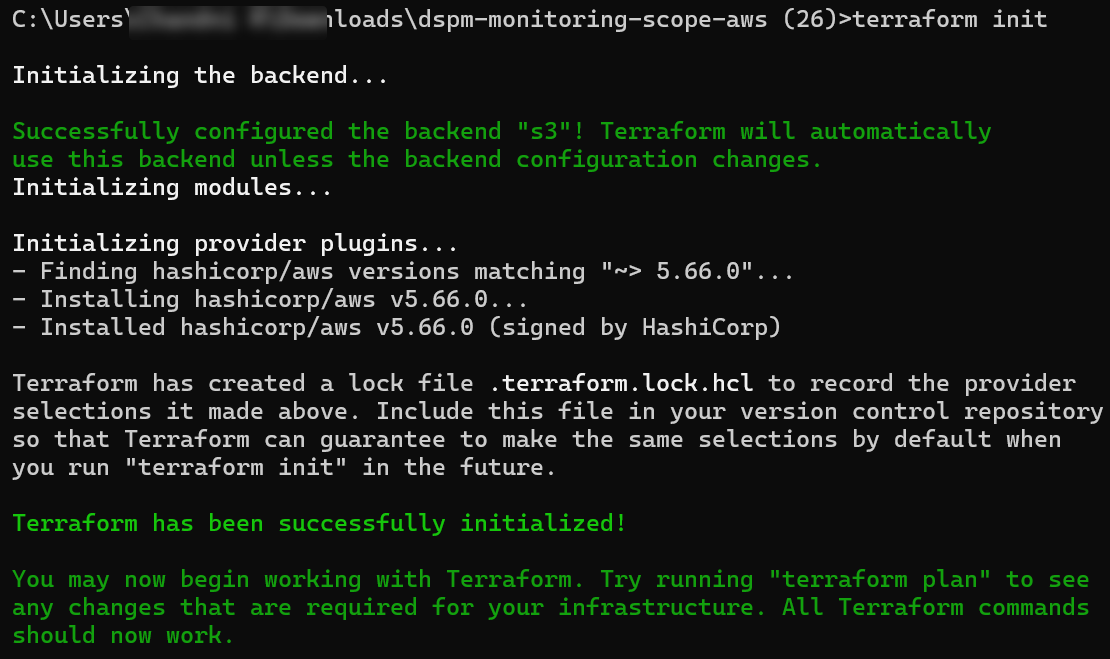
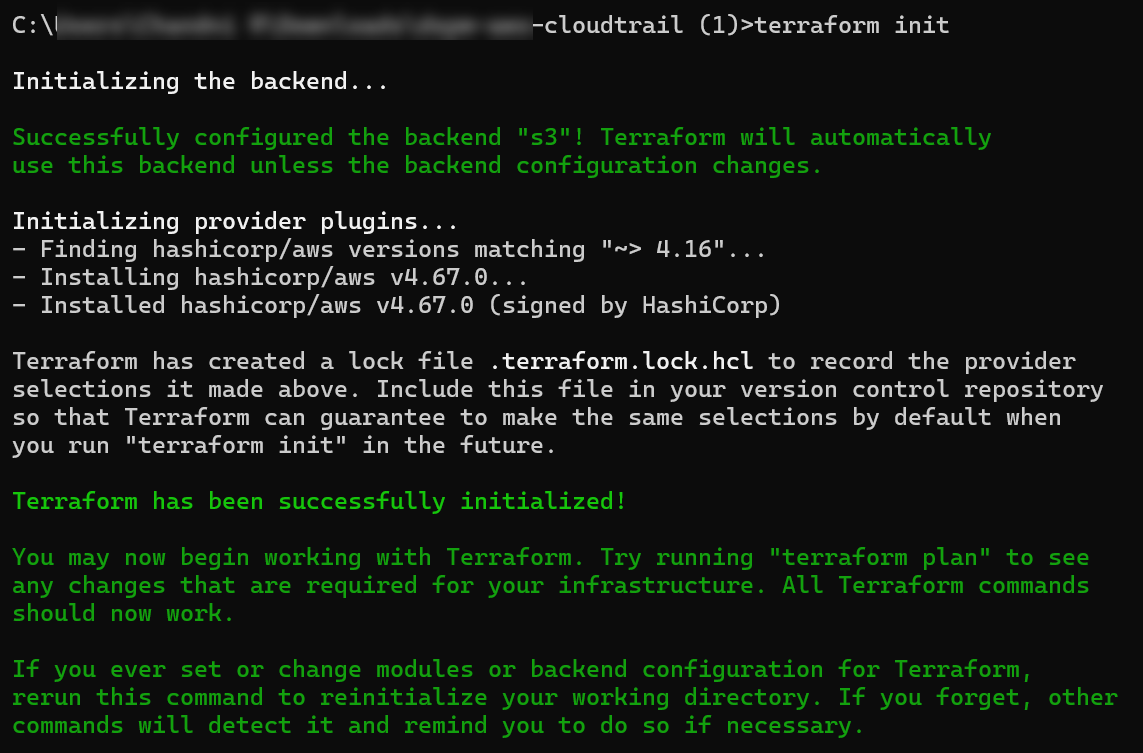
To initialize the Terraform working directory:
terraform initTo verify the changes in the Terraform configuration:
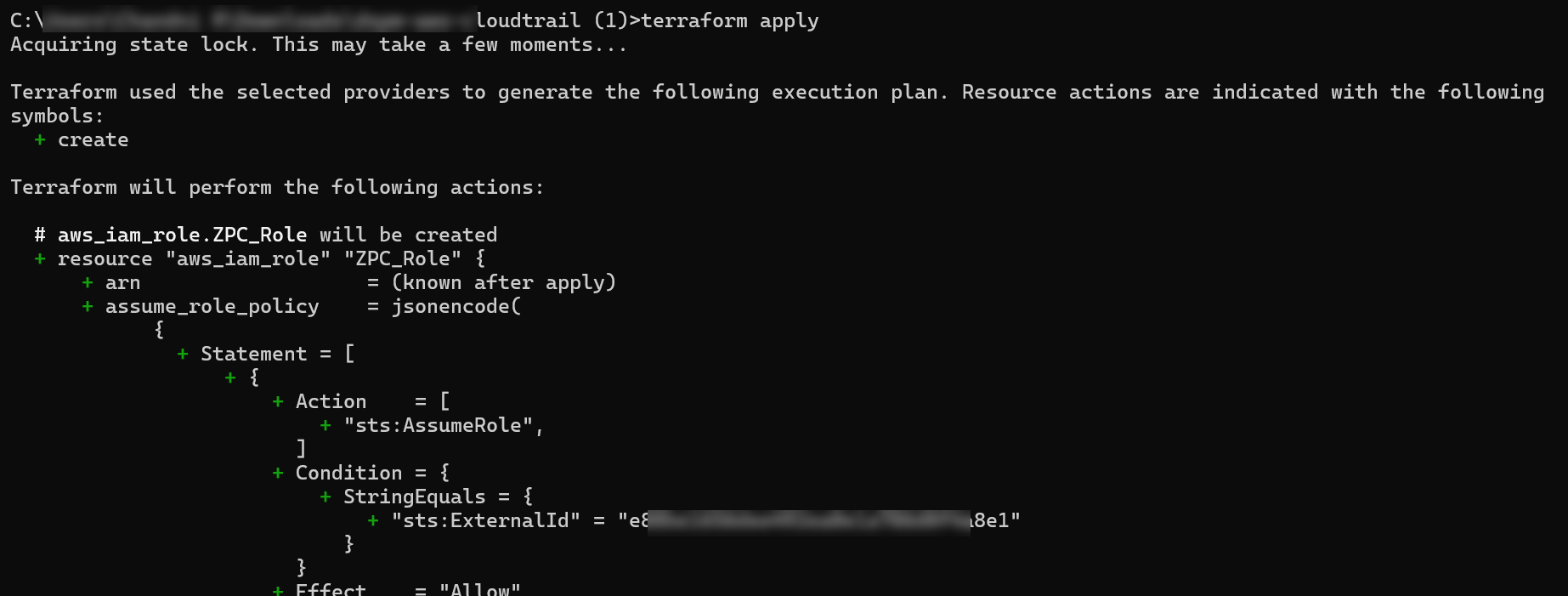
terraform planTo run the Terraform script:
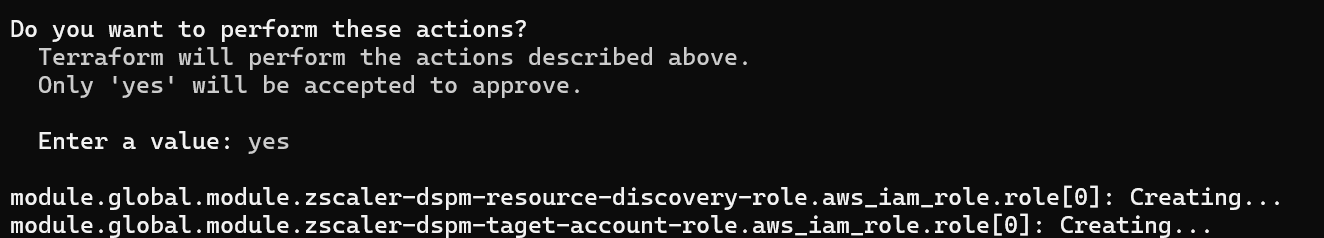
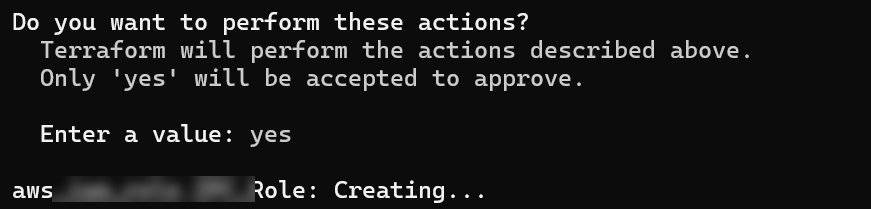
terraform applyUnder Do you want to perform these actions?, enter
yesand pressEnter.
- a. Download the monitoring scope template.
- To deploy CloudFormation template
- CloudTrail
- To deploy CloudFormation template
- a. Download the CloudTrail template.
Click CloudTrail to download the template as a YAML file to your local system.
Close - b. Create stacks in the AWS Management Console.
- Sign in to the AWS account where CloudTrail S3 bucket is available and go to CloudFormation.
- In the left-side navigation, select Stacks.
- Click Create stack.
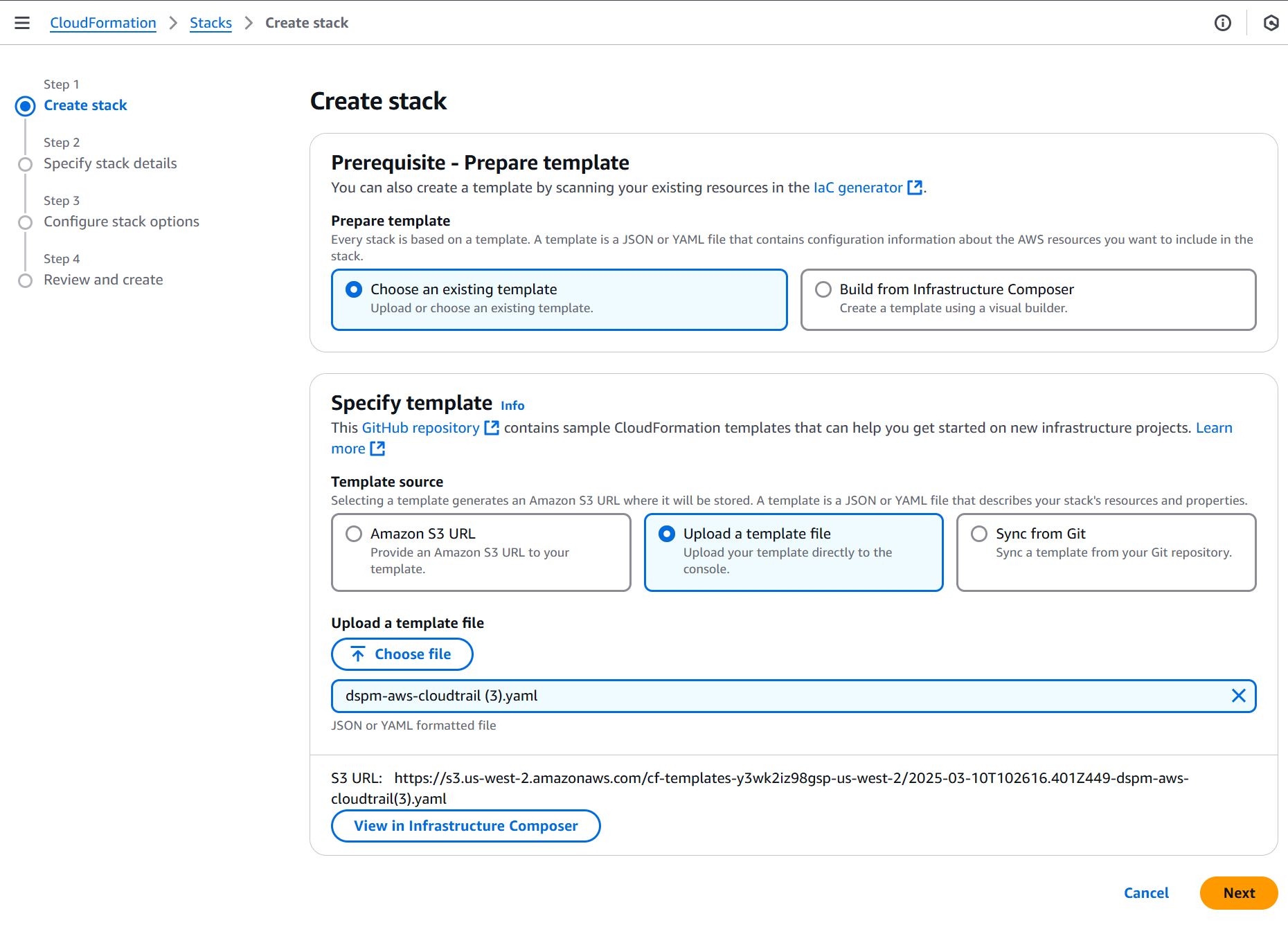
On the Create stack page:
- Prepare template: Select Choose an existing template.
- Specify template: Select Upload a template file to upload the template you downloaded from the DSPM Admin Portal.
- Upload a template file: Click Choose file, browse and select template, then click Open.
- Click Next.
- On the Specify stack details page, under Stack name, enter a unique stack name.
- Click Next.
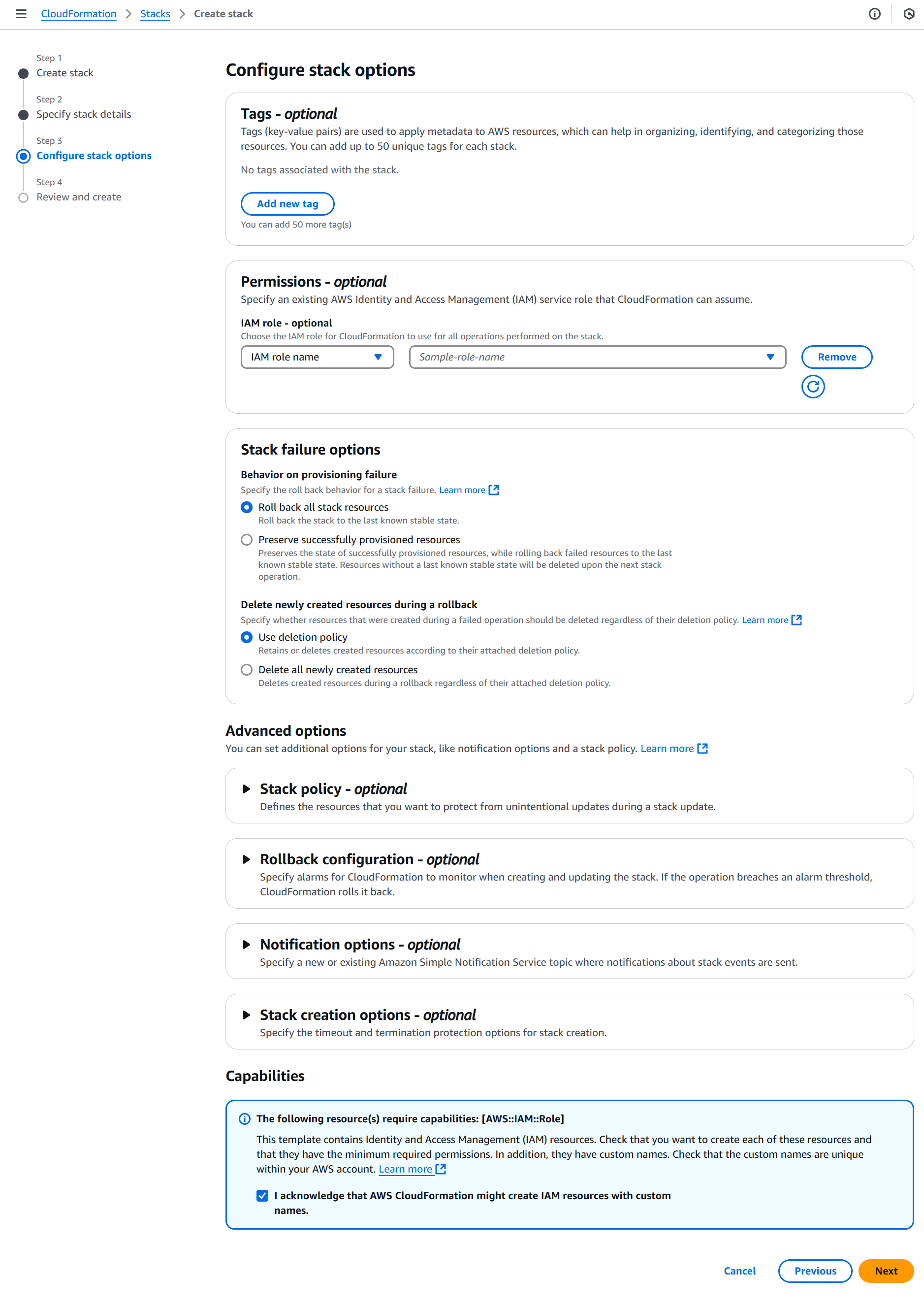
On the Configure stack options page, select the I acknowledge checkbox for AWS CloudFormation to create IAM resources with custom names and click Next.
- On the Review and create page, click Submit.
- a. Download the CloudTrail template.
- To deploy Terraform template
- a. Download the CloudTrail template.
Click CloudTrail to download the template as a ZIP file and extract it to your local system. The ZIP file includes:
- Multiple Terraform files.
- A README file with instructions for running the template.
- b. Update and deploy the Terraform files.
Update the
backend.tf filewith the name of the storage services where you want to store the Terraform state files. For example:- bucket: Enter the name of the S3 bucket.
- region: Enter the region where the S3 bucket is present.
- dynamodb_table: Enter the name of the DynamoDB table.
- Open the Command Prompt or any other CLI app in your local system.
- Switch to the directory that contains the Terraform template.
Copy and paste the access keys of the account and press
Enter.- Run the following commands:
To initialize the Terraform working directory:
terraform initTo verify the changes in the Terraform configuration:
terraform planTo run the Terraform script:
terraform applyFor Do you want to perform these actions?, enter
yesand pressEnter.
- a. Download the CloudTrail template.
- To deploy CloudFormation template
- Monitoring Scope
- Click Done.
DSPM validates the template deployment every hour by checking the roles created and permissions assigned. You can also run an on-demand validation to check if the target accounts are onboarded successfully.
You can view the status of the target accounts on the Overview page.