Zero Trust Device Segmentation
Managing Your Assets
The Assets section provides admins with visibility into all endpoints connected to the network along with their health status.
Zero Trust Device Segmentation leverages multiple techniques (e.g., DHCP options, HTTP User-Agent, SSL fingerprint) to help automatically identify assets. In addition, the application integrates with third-party vendors such as Armis to further enhance the accuracy of the device discovery.
After an asset has been discovered, Device Segmentation tags the asset automatically. If you have integrated Device Segmentation with third-party vendors (e.g., Armis), then additional tags are created. You can also assign custom tags to assets. To learn more, see Working with Tags.
To view and edit assets:
- Go to Asset AI > Assets.
- In the upper right, select how you want to view the assets.
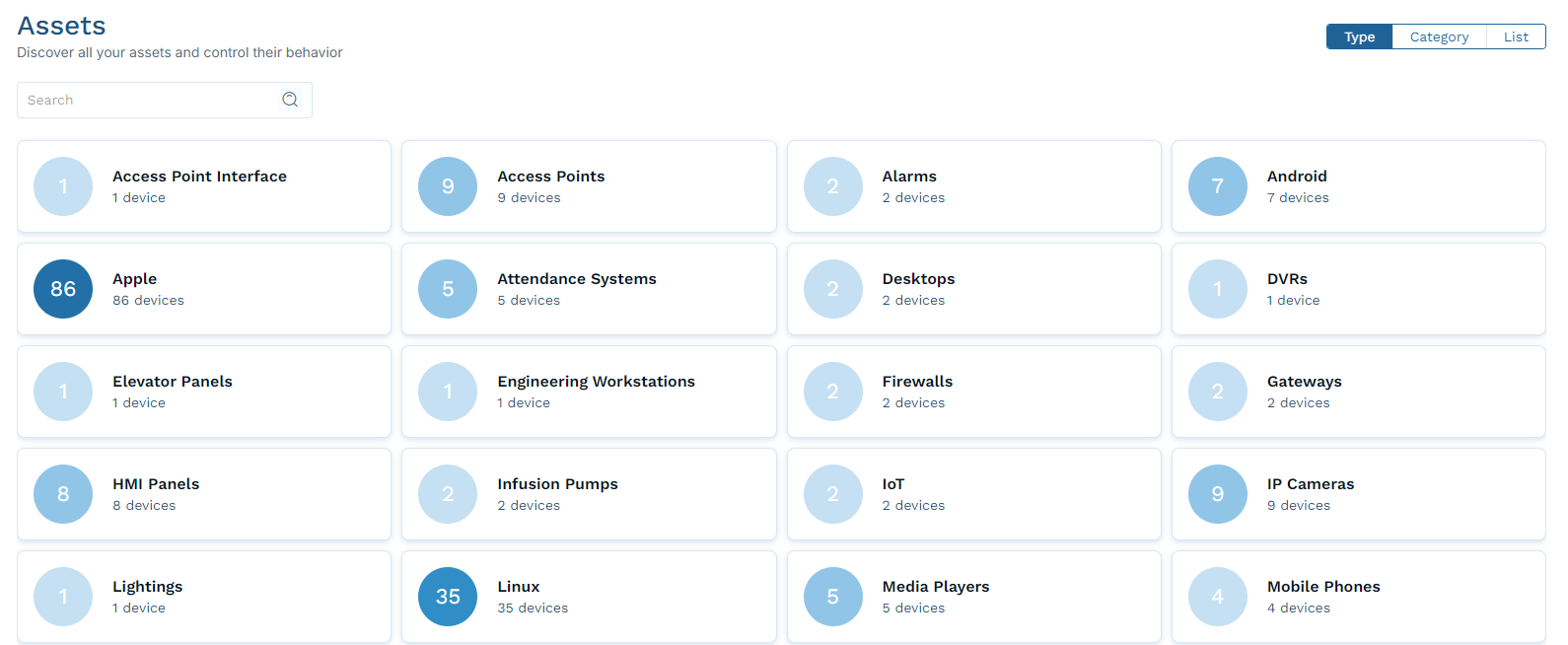
- View Assets by Type
Select Type to view assets grouped by device type. Click any type to open a list of assets of that type.
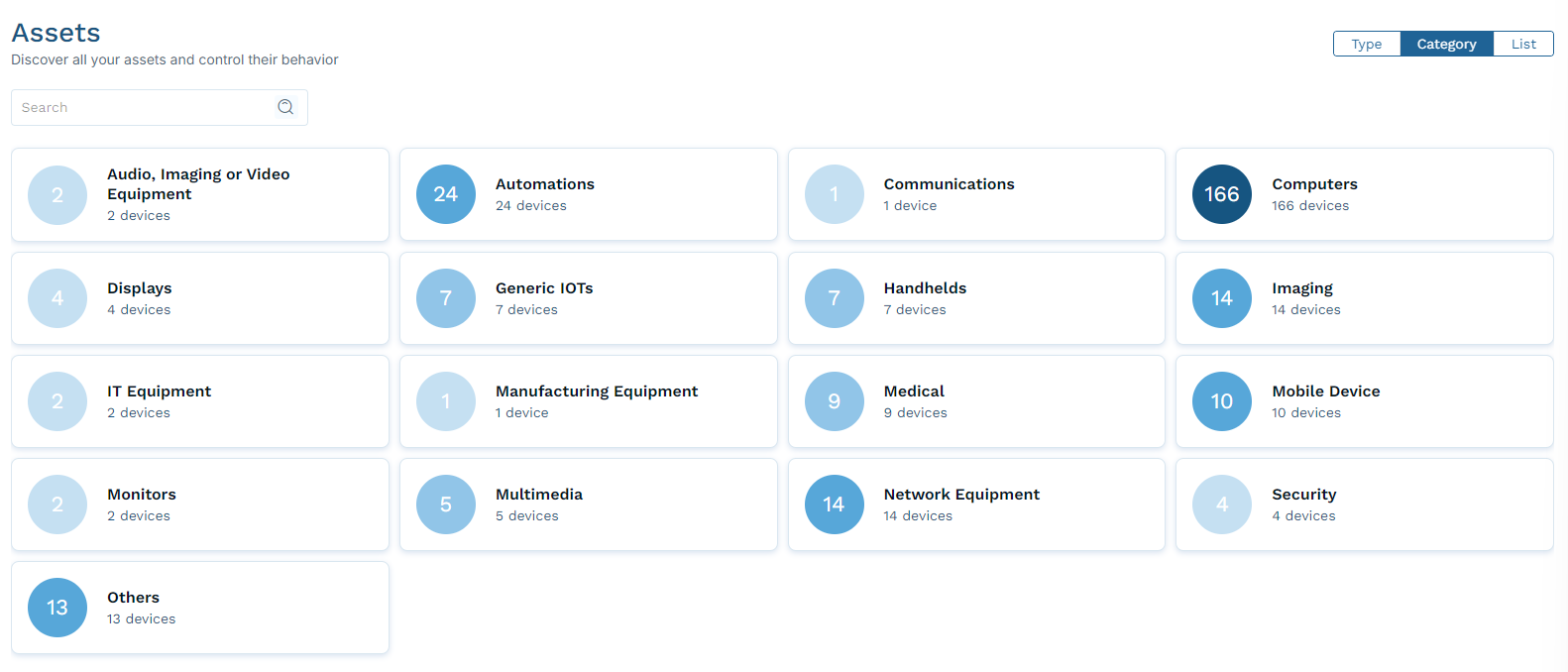
Close - View Assets by Category
Select Category to view assets grouped by device category. Click any category to open a list of assets of that category.
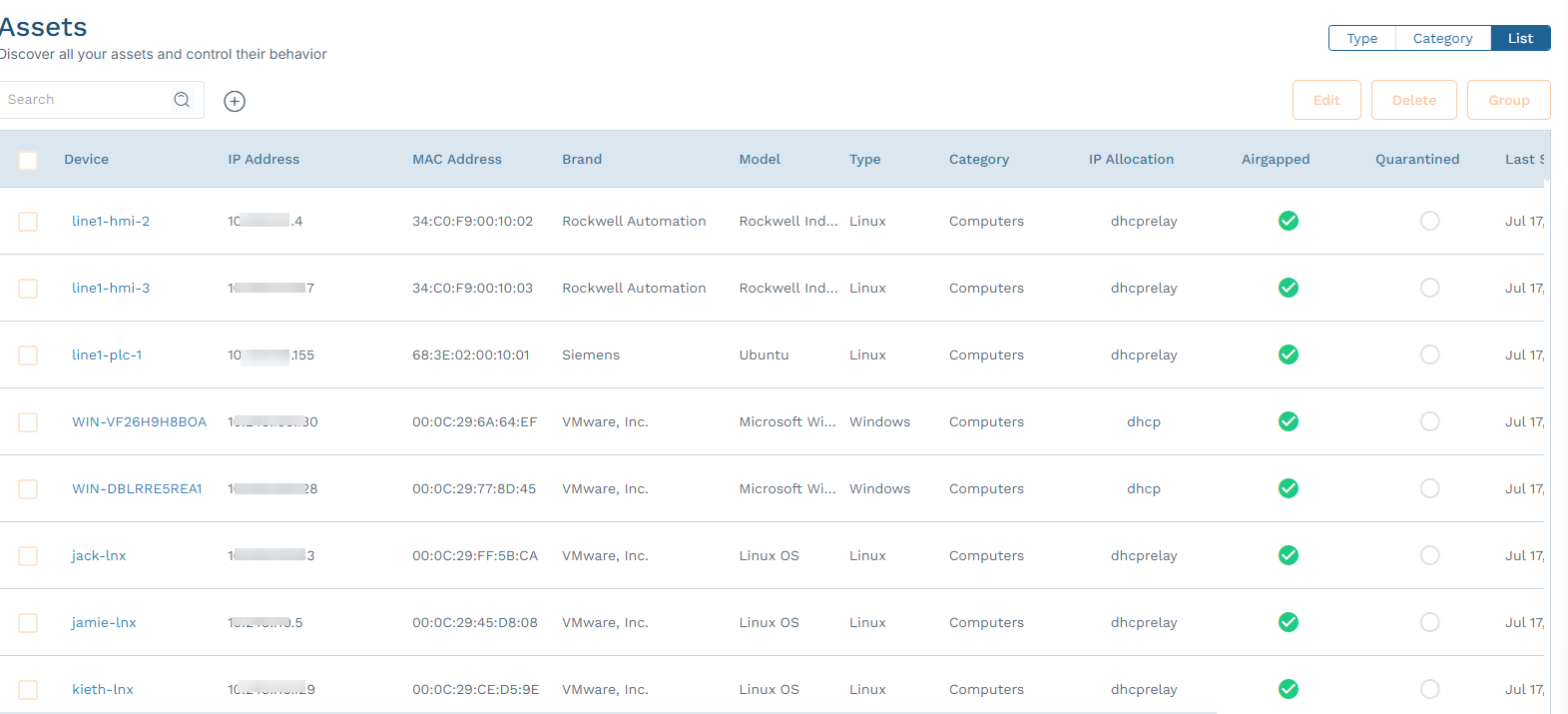
Close - View Assets in a List
- View Assets by Type
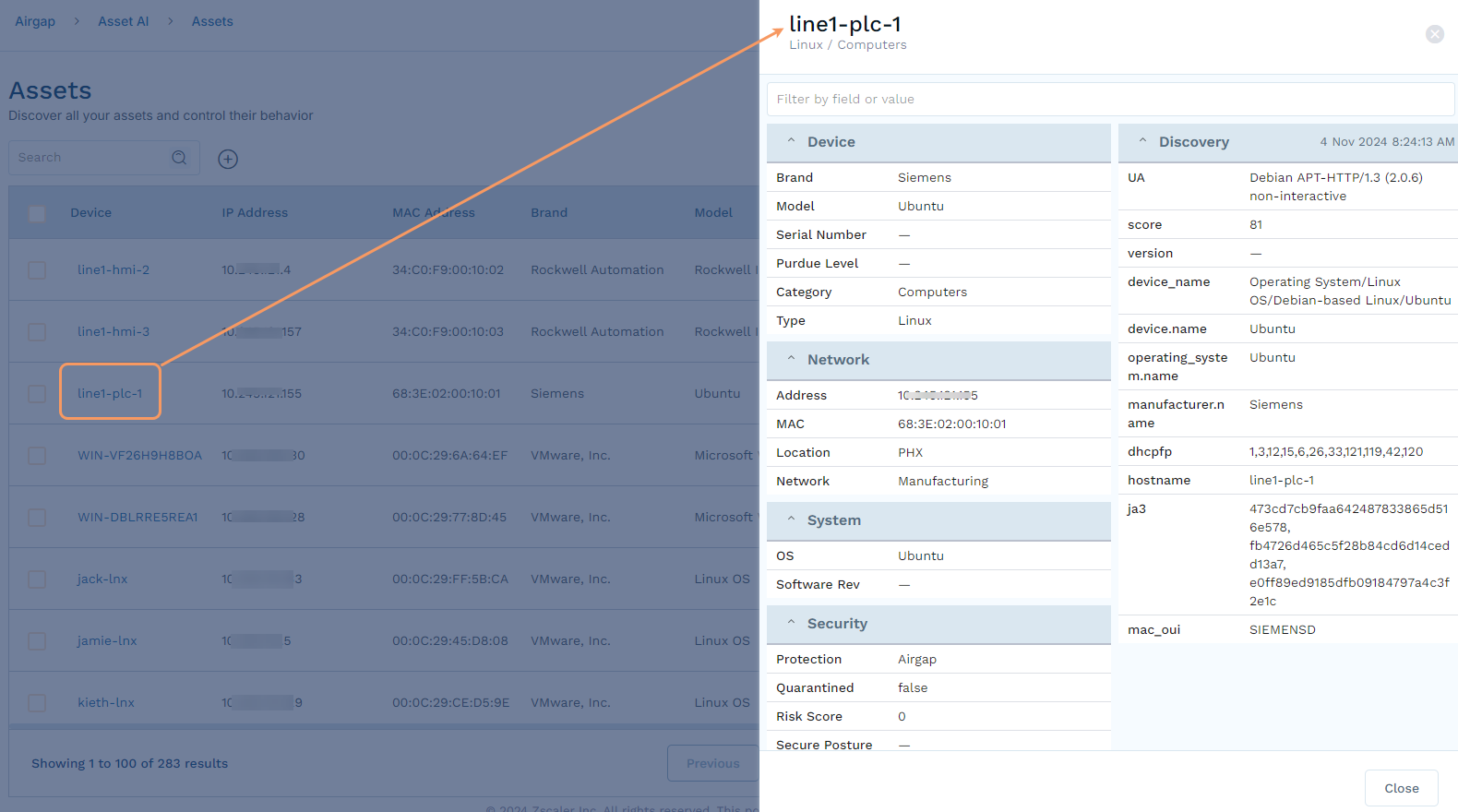
To view more detail on an asset, click the link for that asset in any list (either all assets or for a specific type or category).
Edit a Device
To edit a device:
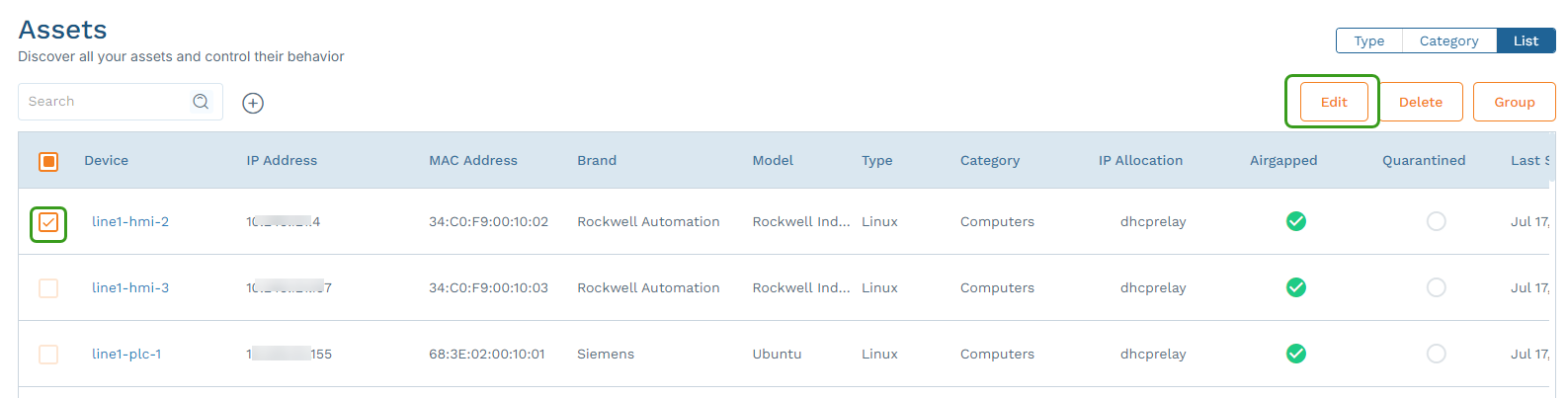
- View the assets in a list view (either all assets or for a specific type or category).
Select the checkbox next to one or more devices and click Edit.
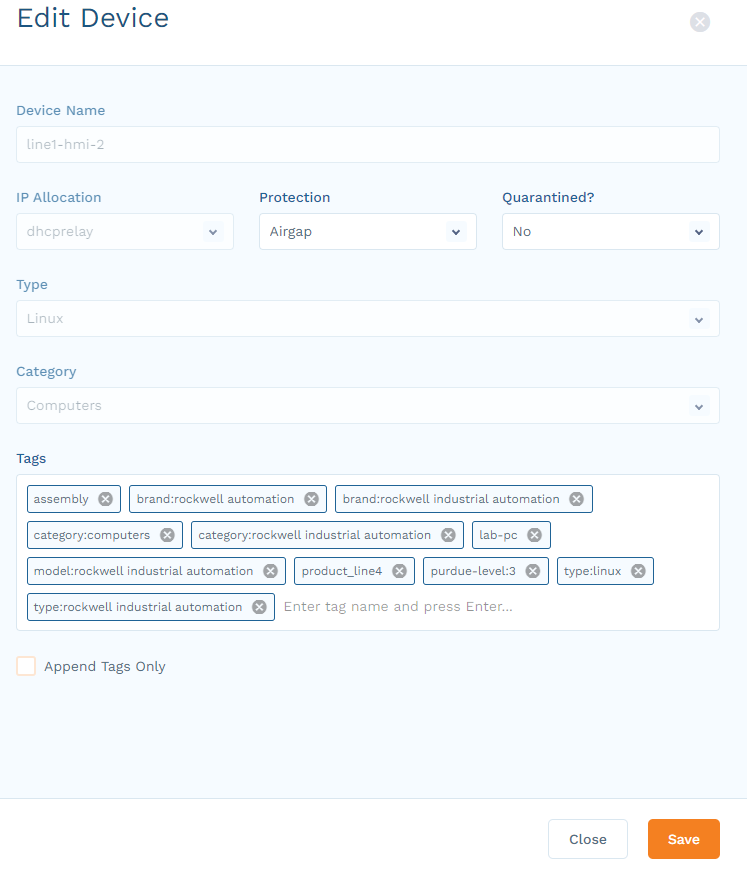
In the Edit Device panel, make the desired changes and click Save. If you are editing multiple devices, your changes affect all devices.
The Protection drop-down menu allows you to select among three different solutions: Airgap, Airgap-Lite, and Airgap+. To learn more, see Understanding Protection Solutions.
Quarantine a Device
If an unfamiliar device appears on the Assets page, you can put that device into quarantine while you perform additional investigation. A device placed into quarantine can access the internet but not the private networks. Inbound connectivity is also allowed so that an admin could remotely connect to the quarantined device.
To place a device into quarantine, edit the device as described previously, and then select Yes in the Quarantined? box before saving.