Zero Trust Device Segmentation
Managing Segmentation Policies
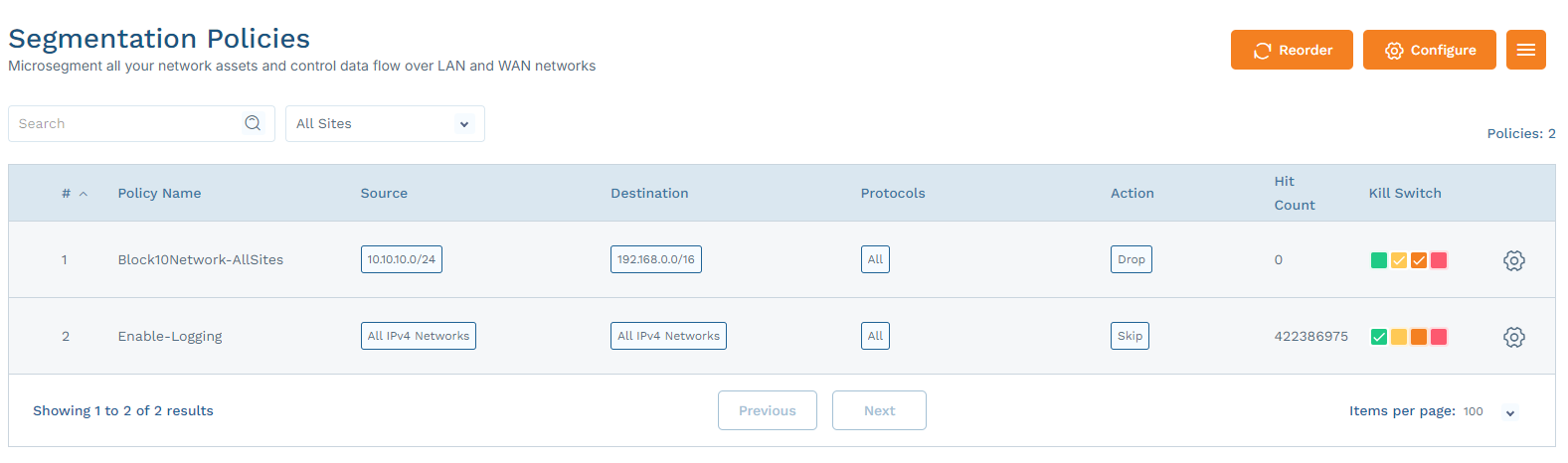
Segmentation policies are essential for defining and enforcing access controls between different network segments, applications, and user groups, thereby enhancing security and compliance.
Zero Trust Device Segmentation allows admins to create network-isolation and endpoint-isolation policies to mitigate lateral threat movements. You can configure policies for a source and destination based on user, TCP/UDP port, IP, network, MAC, or using various group objects. To learn more, see Managing Objects and Groups.
To create or edit a policy rule:
Go to Security > Segmentation Policies.
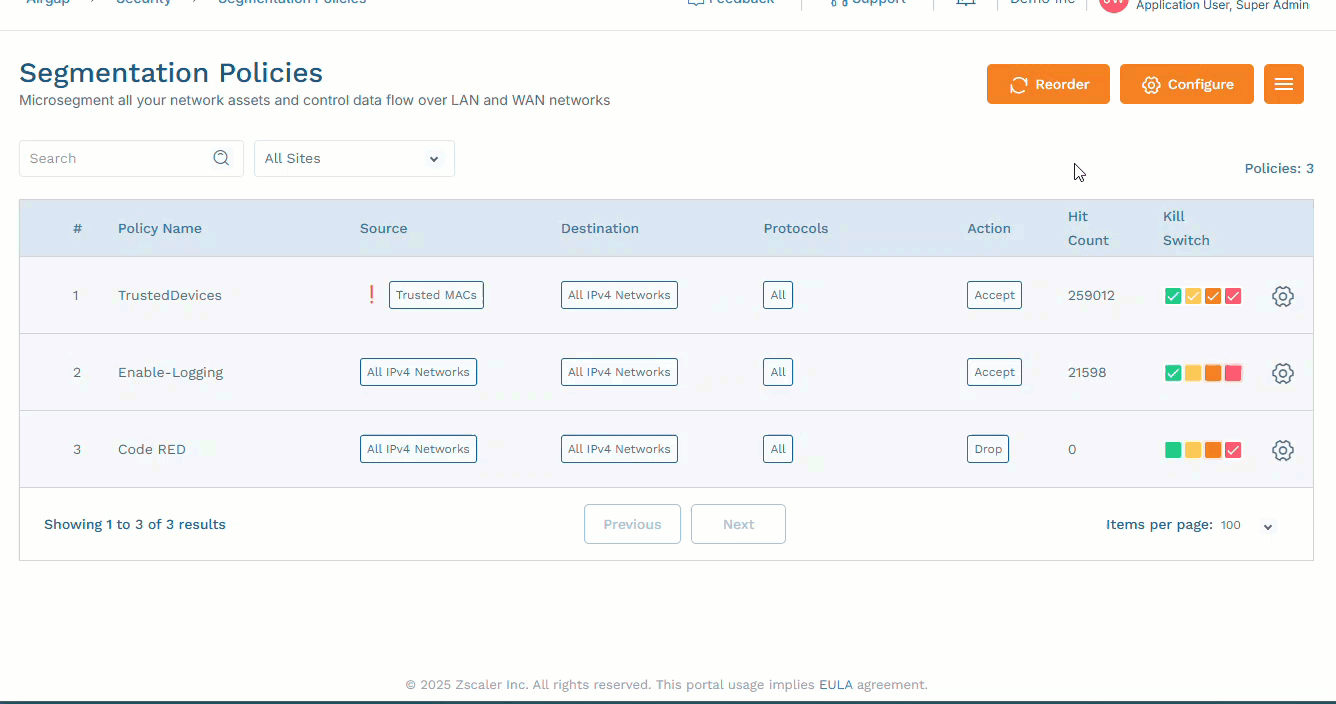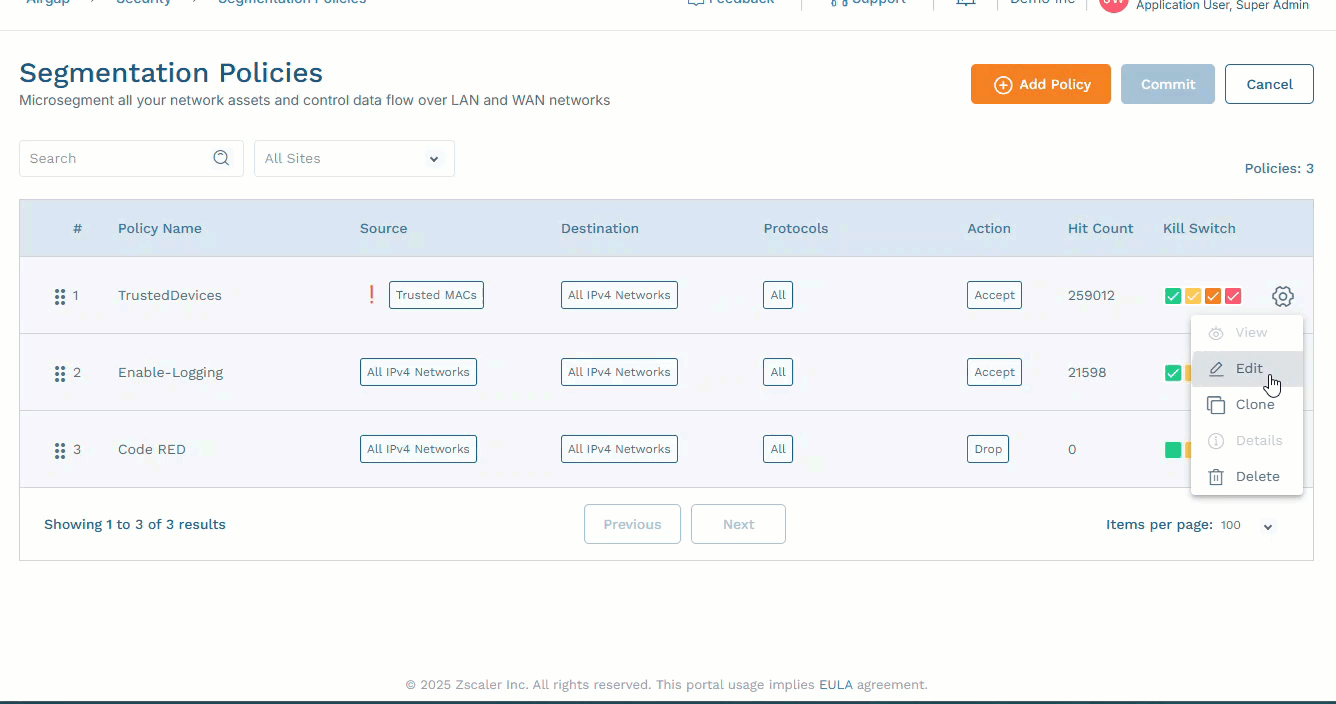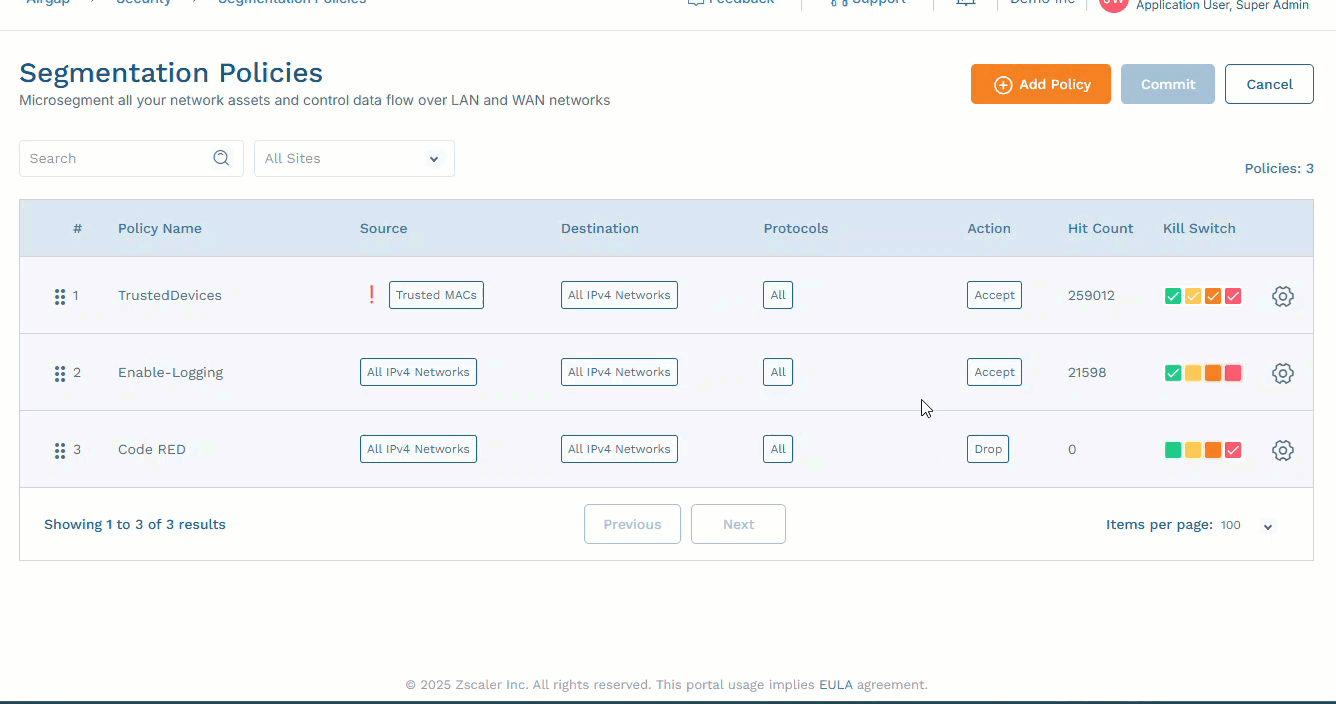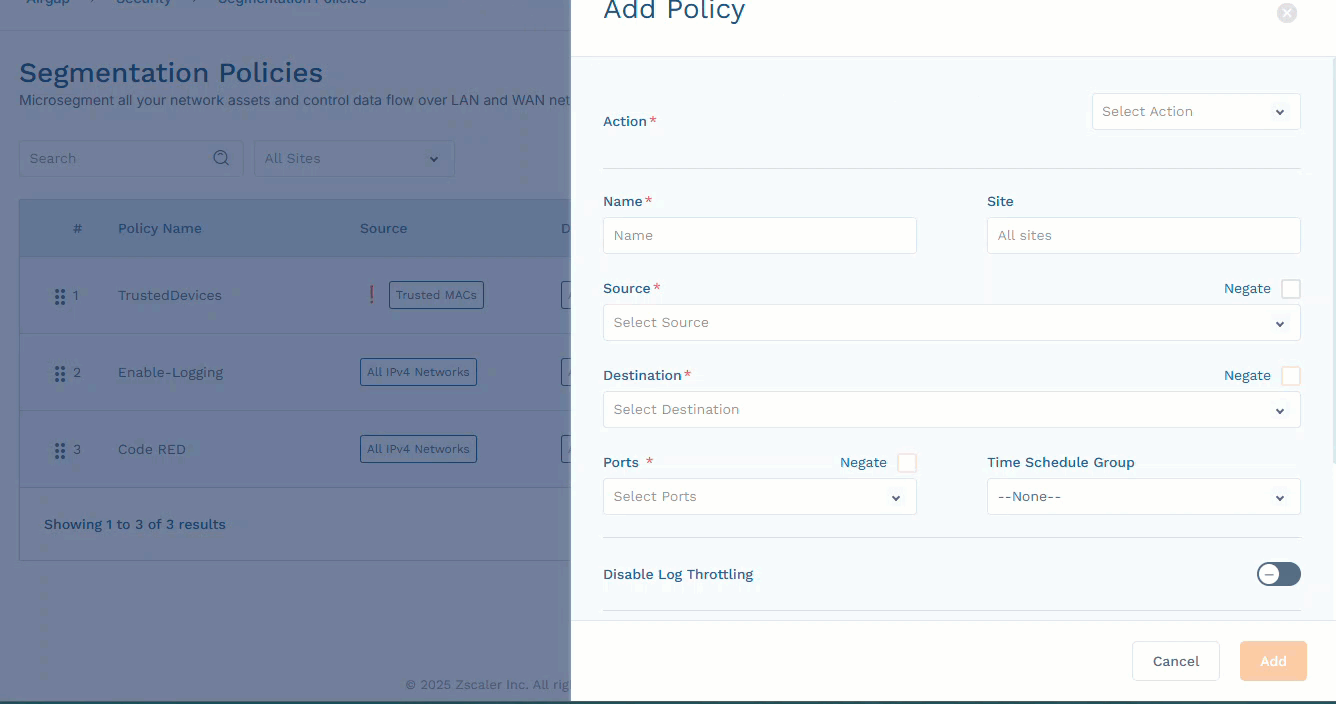
Click Configure, then:
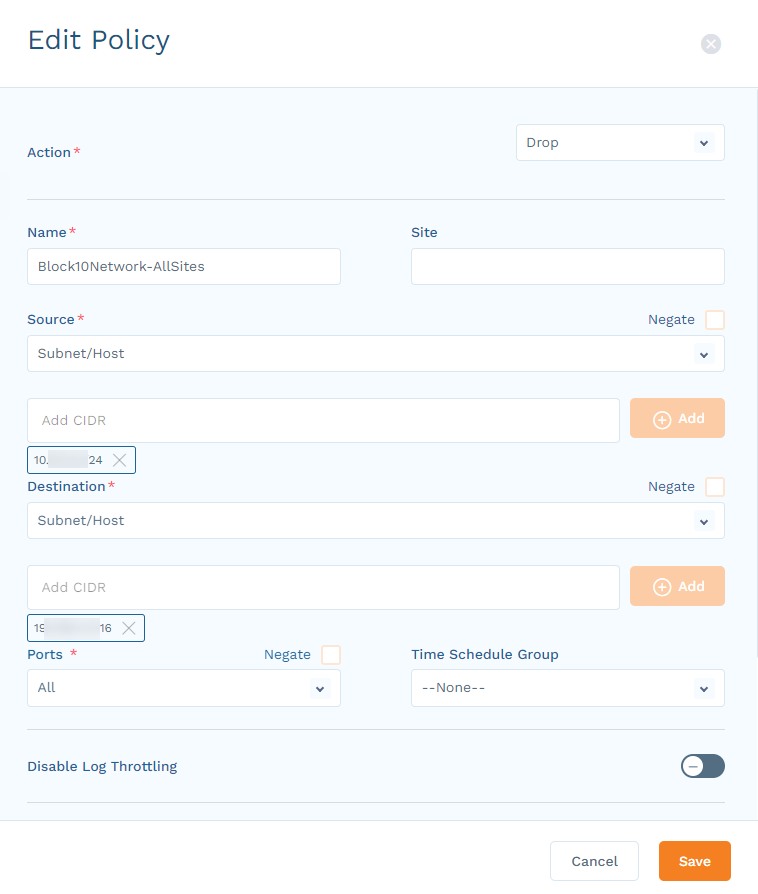
- To edit an existing policy, click the Gear icon next to that policy and select Edit.
- To add a new policy, click Add Policy.
In the Add Policy or Edit Policy panel, define the policy as needed.
To configure a drop deny rule on various parameters between a source and destination pair, select Drop in the Action drop-down menu, then specify the Source and Destination from the drop-down menus.