Secure Private Access (ZPA)
About IdP Configuration
Watch a video about IdP configuration.
For users to access your applications via ZPA, they must first authenticate into Zscaler Client Connector using any SAML 2.0-compliant identity provider (IdP) with the service provider-initiated (SP-initiated) model. ZPA user SSO is SP-initiated, but ZPA admin SSO can be SP-initiated or IdP-initiated. When a ZPA admin selects Single Sign-On Using IdP on the ZPA Admin Portal's Sign In page, the login is SP-initiated. If the ZPA admin logs directly into their IdP, it's IdP-initiated.
Prior to configuring your IdP, Zscaler recommends reading IdP Configuration Best Practices.
The IdP must be configured to recognize Zscaler as a valid SP, and you must configure the full details for the IdP within the ZPA Admin Portal. To learn more, see Configuring an IdP for Single Sign-On.
IdP configuration provides the following benefits and enables you to:
- Authenticate and access applications via ZPA.
- Use SCIM, a standard protocol for automating the exchange of identity information, so that you can provision users and groups.
About the IdP Configuration Page
The IdP Configuration page is read-only if you are subscribed to ZIdentity] for users. To learn more, see What Is ZIdentity?
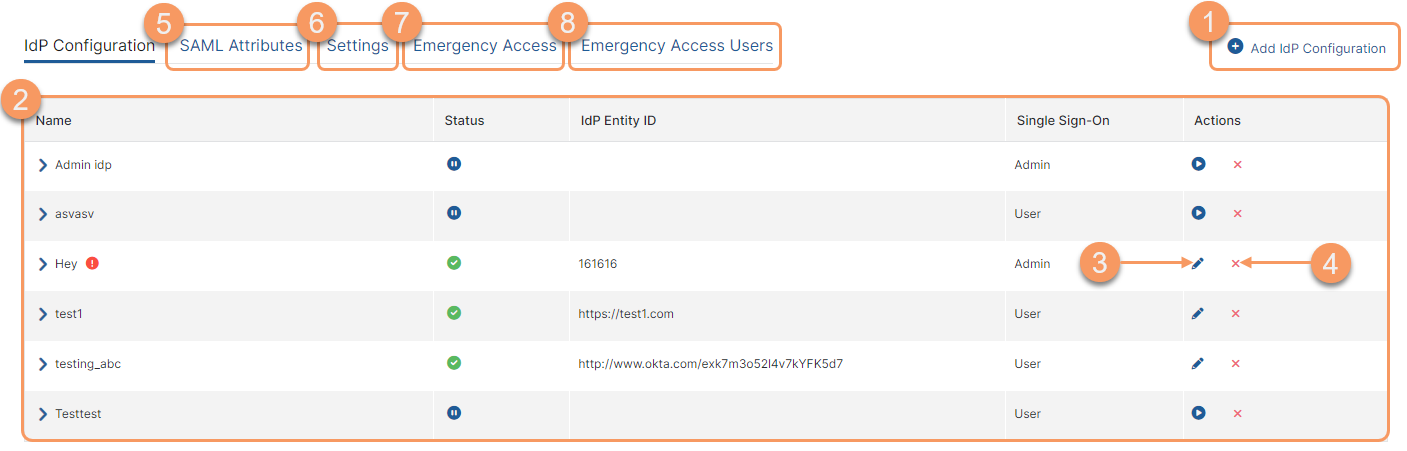
On the IdP Configuration page (Authentication > User Authentication > IdP Configuration), you can do the following:
The Add icon is hidden if you are subscribed to ZIdentity for users. To learn more, see What Is ZIdentity?
- View a list of the names of all IdPs that were configured for your organization. For each IdP configuration, you can see:
Name: The name of the IdP configuration. An icon shows next to the name of the IdP if the IdP certificate is close to expiring or has expired:
- If the IdP certificate has expired, a red warning icon (
 ) is displayed.
) is displayed. - If the IdP certificate has less than 7 days before expiration, a yellow caution icon (
 ) is displayed.
) is displayed. - If the IdP certificate has less than 30 days before expiration, an orange info icon (
 ) is displayed.
) is displayed.
If the IdP certificate is part of a certificate chain instead of a single certificate, the certificate expiring the earliest is considered to reflect the expiration icons.
- If the IdP certificate has expired, a red warning icon (
- Status: The status of the IdP configuration (i.e., enabled, disabled, or resume if the configuration was paused during set up).
- IdP Entity ID: The entity ID URL for the IdP.
- Single Sign-On: Indicates whether the IdP is set up for Admin or User SSO.
If the IdP configuration was set up prior to the Multiple Identity Provider Support for Single Sign-On release and was configured to use Both (i.e., admin and user SSO), it still functions as before. However, it is listed in the table with Admin, User displayed for this column.
See image.
You can expand the row to view details regarding the configuration, import SAML attributes, or verify that SSO was configured correctly for the IdP.
- Edit an existing IdP configuration.
- Delete an IdP configuration.
An IdP cannot be deleted if it is used for emergency access. When an IdP gets deleted, all user risk scores associated with users of that IdP are also deleted.
- Go to the SAML Attributes page to import attributes or add them manually. If you expand the row to view details for an IdP configuration set up for User SSO, you can click Show Attributes to see a filtered view of the SAML Attributes page for that IdP.
- Go to the Settings page to modify authentication settings (e.g., enabling Remote Assistance).
- Go to the Emergency Access page to configure emergency access for third-party users.
- Go to the Emergency Access Users page to view and manage users designated for emergency access.